Too many cybersecurity teams are betting on the wrong tools. They invest in SIEMs expecting real-time protection or deploy EDRs thinking they’ve covered cloud, email, and identity too. The result? Gaps no one notices until it’s too late.
A 2024 report by Palo Alto Networks found that 54% of organizations see tool fragmentation in cloud environments as a top security challenge.
That fragmentation isn’t just technical. It reflects a deeper confusion about what these tools do and how they fit together.
So, what’s the difference between EDR, MDR, XDR, SIEM, SOAR, and even antivirus? More importantly, how do you know what your organization actually needs?
In this guide, I’ll break it all down with zero fluff. You’ll get clarity, comparisons, and the confidence to make the right call for your team, your budget, and your risk profile.
What These Cybersecurity Tools Really Do And Why They’re Often Confused?
Let’s be honest – most cybersecurity tools today sound like alphabet soup.
EDR, MDR, XDR, SIEM, SOAR… it’s not just jargon overload, it’s decision paralysis.
The confusion usually starts when teams ask questions like:
“Isn’t XDR just EDR with cloud?”
“Do I need both SIEM and SOAR?”
“Can MDR replace my internal SOC?”
These questions aren’t coming from inexperience. They’re coming from real-world chaos. Most mid-sized organizations aren’t trying to play buzzword bingo. They’re trying to:
- Build the right defense architecture.
- Avoid buying overlapping tools.
- Justify budget to non-technical leadership.
- Respond faster to actual threats.
And that’s where the chaos begins. Because many of these tools sound the same, solve overlapping problems, and are pitched by vendors as silver bullets.

Before we dive into full comparisons, let’s take a clear-eyed look at what each tool really does, where it fits, where it doesn’t, and why it matters.
Recommended Read: Looking to map out your actual threat exposure before deciding on SIEM, SOAR, or XDR? Check out our guide on 10 Essential Use Cases for Attack Surface Management to see how better visibility into your digital footprint can help clarify which security tools are really necessary.

EDR is Your Eyes and Reflexes at the Endpoint Level
Imagine you’re defending a building. The endpoint is every door and window — every laptop, every server, every phone that touches your network.
EDR, or Endpoint Detection and Response, is the trained guard stationed at each one. It doesn’t just check for known threats. It watches behaviors and learns. And when something seems off, it acts fast.
This tool evolved because traditional antivirus just wasn’t cutting it anymore. Malware got smarter. Threats moved faster. Organizations needed something that could not only detect but respond — isolate, investigate, and contain — all without waiting for human intervention. That’s what made EDR the foundation of modern endpoint protection.
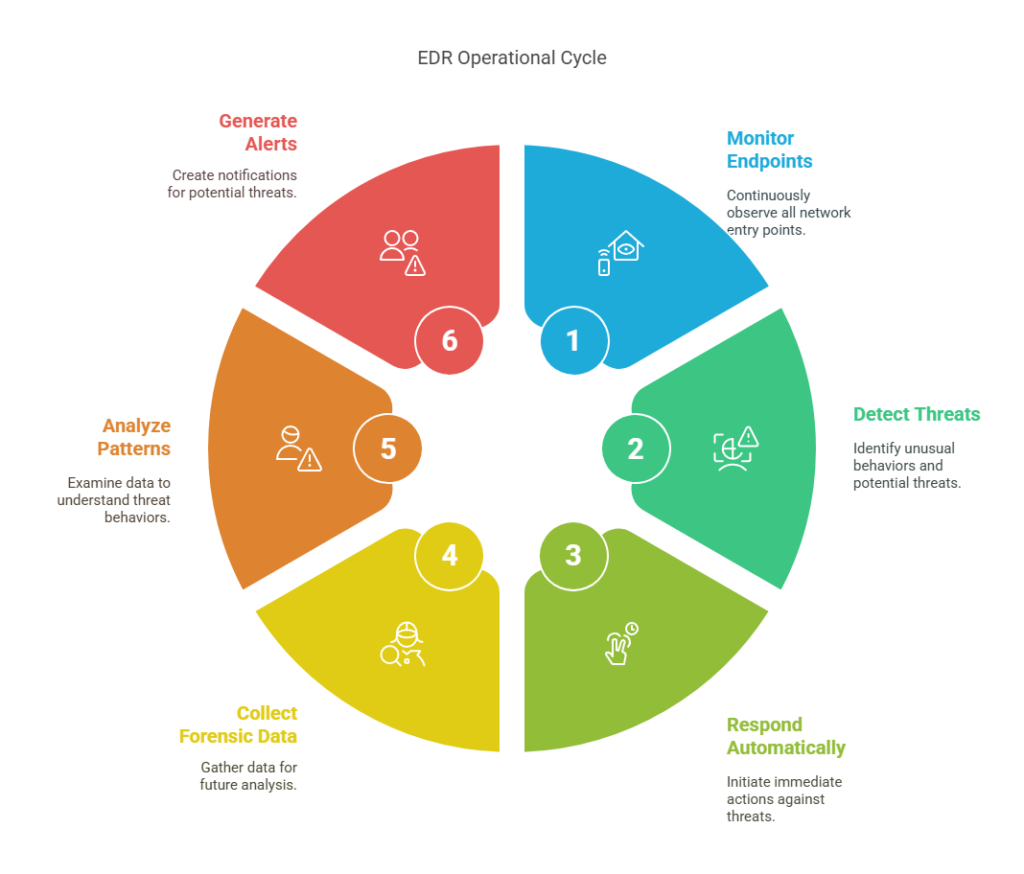
It continuously monitors, collects forensic data, and analyzes patterns to catch zero-day exploits, lateral movement, or ransomware in action. But here’s the catch: EDR is only as good as the analyst behind it. It generates alerts. Lots of them. And unless you’ve got a seasoned security team watching the dashboard, those alerts can drown you.
Still, for organizations with an in-house SOC or at least a few skilled defenders, EDR is non-negotiable. It’s the layer that sees what firewalls and SIEMs can’t. It’s the reflex that stops an attacker before they pivot deeper into the network.
Datacipher Recommends: Start with EDR if you already have a team that understands threat triage and wants hands-on control. Avoid using EDR as your only defense layer. It’s powerful, but not complete on its own.
MDR is Your 24/7 Security Team Without the Headcount
You can buy the best security tools in the world, but if no one’s watching them you’re still exposed. That’s where MDR, or Managed Detection and Response, steps in. It’s not just a tool. It’s a service. A team. A brain that never sleeps.
MDR is what you bring in when you don’t have the luxury of a full-time, around-the-clock SOC. It combines powerful technologies like EDR and SIEM with real human expertise — analysts, responders, and threat hunters — who monitor your environment, investigate alerts, and take action when something suspicious happens.
What makes MDR so valuable isn’t just the tech stack. It’s the outcomes. You get alert triage, root cause analysis, and even remediation in some cases. All this can be done without hiring five new people or burning out the one security engineer you do have.

Over the years, MDR has become the default security strategy for mid-sized organizations that need enterprise-grade coverage but can’t afford enterprise headcount. It turns detection into a managed outcome. It filters out noise, escalates what matters, and gives you a clear view of what’s going wrong and how it’s being handled.
That said, MDR isn’t one-size-fits-all. Some services are glorified alert-forwarders. Others go deep into your environment and actually stop threats in motion. Knowing the difference and picking the right partner is where strategy meets survival.
Datacipher Recommends: Choose MDR when you lack 24/7 coverage or the internal muscle to respond fast. Avoid MDR vendors who won’t customize their detection rules to fit your environment. Cookie-cutter protection leads to blind spots.
XDR is the Control Room That Sees It All and Connects the Dots
If EDR is your guard at the door, and MDR is the team watching the cameras, then XDR — Extended Detection and Response — is the control room that links every sensor, every feed, every alert into one unified view. It’s not just about endpoints anymore. It’s endpoints, yes, but also cloud, network, identity, email – the whole chessboard.
XDR was born out of frustration. Security teams were drowning in siloed alerts from a dozen tools. Each platform saw its own corner of the attack, but no one saw the full picture. XDR changes that. It stitches data together from multiple layers of the stack and applies analytics to detect threats that would otherwise go unnoticed in isolation.
Think of it like this: one login attempt might look normal. A failed login, followed by lateral movement, followed by privilege escalation. That’s a breach unfolding.
XDR sees the chain. It connects behaviors across tools and makes detection contextual, not just reactive. Where it gets powerful is in response.
A good XDR platform doesn’t just tell you something’s wrong — it suggests what to do next, sometimes even acts automatically. And because it has eyes on multiple domains, its response can be broader and faster than what EDR alone could manage.
But XDR isn’t magic. It still needs tuning. It still needs people who understand your environment. And not all XDRs are built equal: some are open, some are vendor-locked. The difference can define your agility in the face of real attacks.
Datacipher Recommends: Go for XDR when you want unified visibility and smarter, correlated detection across multiple domains. Avoid XDR solutions that lock you into their ecosystem. Flexibility and integration should never be compromised.
SIEM is Your Security Archive, Alarm System, and Investigator Rolled Into One
For years, SIEM — Security Information and Event Management — has been the backbone of enterprise security. It’s not flashy. It’s not fast. But when configured well, it’s the most critical source of truth in your entire security program.
SIEM doesn’t detect threats in real-time the way EDR does. What it does is collect logs from everywhere. From firewalls, servers, cloud apps, and authentication systems and correlate all that data to surface anomalies, patterns, and possible incidents. It’s your archive. Your audit trail. Your forensic toolkit. And sometimes, your early warning system.
The original promise of SIEM was visibility. But over time, it evolved into a compliance engine, a breach investigation tool, and — when tuned well — a near real-time alerting platform. That’s the keyword, though: tuned well.
Because most SIEMs out of the box are noisy, vague, and overwhelming. The value is unlocked only when you deeply understand your environment and define the rules that actually matter.
What makes SIEM essential today is context. While EDR sees an attack on one machine, SIEM might show that the attacker tried the same trick on ten others and succeeded on two. It helps you see how threats propagate. It helps you reconstruct what happened. And most importantly, it helps you prove it to leadership, auditors, and insurers.
Still, SIEM is not plug-and-play. It demands ongoing care. And if you don’t have the people or processes to maintain it, it can become an expensive log warehouse rather than a threat detection asset.
Datacipher Recommends: Invest in SIEM when you need centralized visibility, historical context, and audit readiness. Avoid relying on SIEM alone for real-time threat response. Pair it with SOAR or XDR for faster action.
Recommended Read: Cortex XSIAM vs. Traditional SIEM: Why Modern SOCs Need Automation-First Platforms
SOAR is Your Automation Engine When Alert Fatigue Becomes a Threat
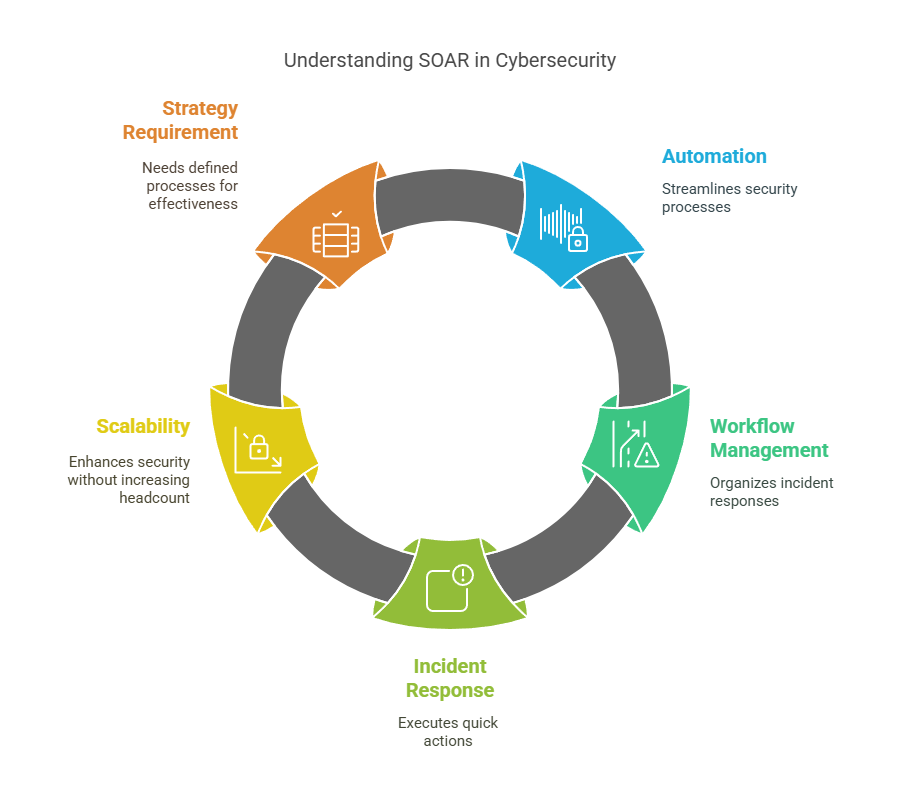
At some point, detection isn’t the problem. It’s the flood of alerts. The duplication. The manual tickets. The endless switching between tools just to respond to one incident. That’s when SOAR — Security Orchestration, Automation, and Response — becomes your saving grace.
SOAR isn’t a detection tool. It doesn’t tell you what’s wrong. Instead, it tells your tools and your team what to do next. It connects systems, automates workflows, and slashes response times. Think of it as the brainstem of your security stack: fast, instinctive, and repeatable.
Let’s say your SIEM flags a suspicious login, your EDR detects process injection, and your email filter tags a phishing attempt. SOAR pulls that context together, creates an incident, enriches it with threat intel, and auto-quarantines the endpoint — all in seconds.
No tickets. No human bottleneck. Just action.
The real beauty of SOAR is that it scales your security maturity without scaling your headcount. It turns tribal knowledge into structured playbooks. Over time, it trains your security response to behave like your best analyst every time.
But here’s the catch: SOAR only works when you know what you want it to do. Automation without strategy is chaos on autopilot. That’s why SOAR shines brightest in mature environments where processes are already defined — and the goal is speed, not guesswork.
Datacipher Recommends: Bring in SOAR when your team is drowning in alerts and already knows how incidents should be handled. Avoid implementing SOAR too early. Without defined workflows, it becomes a high-maintenance dashboard with no clear value.
Editor’s note: If you’re evaluating platforms, this comparison of top SOAR tools for enterprises can help you choose the right fit for your environment.
Antivirus is the Security Tool We All Outgrew, But Still Need
Before EDR, before XDR, before SOCs and SIEMs, there was antivirus. It was the first line of defense most companies ever installed. For years, it did its job well: scanning files, matching them against known malware signatures, and quarantining the bad stuff.
But the world changed. Malware stopped behaving like malware. Threats became fileless, evasive, polymorphic. Attackers started chaining exploits across vectors that antivirus was never built to see, let alone stop. And so antivirus began to fade into the background, replaced by more adaptive, behavior-based systems like EDR and XDR.
But here’s the twist: antivirus never really went away. Most modern EDR solutions include antivirus-like features under the hood.
And for organizations with minimal security budgets, a solid antivirus — especially one with cloud threat intel and real-time protection — is still better than nothing.
The danger comes when organizations think antivirus is enough. That it’ll stop ransomware. That it’ll detect insider threats. That it’s smart enough to handle today’s threat landscape. It’s not.
Antivirus is no longer your security strategy. It’s your bare minimum. Your seatbelt. You wouldn’t drive a racecar with just a seatbelt, right? You’d want airbags, collision detection, a pit crew – that’s what modern security stacks offer. Antivirus is part of that stack, but never the star of the show.
Datacipher Recommends: Use antivirus only as a foundational layer, not as your main line of defense. Upgrade to EDR or XDR the moment your threat model includes anything beyond basic malware – which, in today’s world, is almost always.
The Only Cybersecurity Tool Comparison Table You’ll Ever Need
Choosing between EDR, MDR, XDR, SIEM, SOAR, and antivirus isn’t just a matter of picking the newest or most expensive option. It’s about finding the right tool for the right job at the right stage of your security maturity.
Each tool in this table solves a different problem. Each one requires different levels of investment, effort, and team readiness. Depending on your current environment, some may be critical while others can wait.
This isn’t a vendor checklist or feature matrix. This real-world comparison is designed for security teams and decision-makers needing clarity quickly.
We’re answering questions like:
- What does each tool actually do?
- When should you bring it into your stack?
- What are the trade-offs?
- Can one replace another?
- And what’s the risk of skipping it?
Let’s break it down.
| Outsourced threat detection and response across endpoints and networks. | EDR | MDR | XDR | SIEM | SOAR | Antivirus |
| What It Does | Monitors and responds to endpoint threats using behavioral analysis. | All the tools it integrates with | Correlates and responds to threats across multiple layers. | Aggregates, stores, and analyzes logs from across your environment. | Automates security workflows and incident response across tools. | Scans and blocks known malware using signature-based detection. |
| Covers | Endpoints (laptops, servers, mobile) | Endpoints, sometimes network and cloud | Endpoint, cloud, email, identity, network | Entire IT environment (logs, events, flows) | Can replace antivirus but needs SIEM/SOAR support | Endpoints only |
| Detection Strength | Strong for behavior-based, real-time detection | Strong; combines tech + human analysis | Very strong; multi-source correlation | Depends on rules; great for compliance + forensics | N/A — depends on other tools | Low for modern threats; good for known malware |
| Who Operates It | Internal security team or SOC | External managed SOC provider | Internal SOC or hybrid model | Internal team or MSP | Internal SOC with playbook maturity | Automatically or basic IT admin |
| Effort to Deploy & Maintain | Medium to High | Low to Medium | Medium | High | High | Low |
| Best Fit For | Orgs with in-house security analysts or lean SOCs | Mid-sized orgs without 24/7 internal teams | Teams needing unified, cross-domain visibility | Mature orgs needing audit trails and deep analysis | Mature teams with defined response processes | Very small orgs or legacy systems |
| Can It Replace Other Tools? | Limited customization, depending on provider’s visibility | Replaces internal SOC for many use cases | May consolidate EDR + SIEM + partial SOAR | No — complements detection tools like EDR/XDR | No — extends SIEM, EDR, etc. functionality | No — obsolete as standalone defense |
| Where It Falls Short | Limited visibility beyond endpoints, noisy if unmanaged | May require vendor ecosystem; needs tuning | May require vendor ecosystem, needs tuning | Not real-time, alert fatigue if poorly tuned | Ineffective without existing processes and detection tools | Misses fileless, polymorphic, advanced threats |
| When to Add It to Your Stack | When you’re beyond basic AV and need endpoint visibility | When you can’t monitor 24/7 in-house | When you want integrated, faster detection across the stack | When compliance or forensic investigation is critical | When alert overload or response delays hit | Start here if no security tools exist |
| Risk of Not Having It | Blind to advanced attacks on endpoints, slower response | Slower breach detection, over-reliance on in-house alerts | Fragmented alerts, missed complex attack chains | Poor historical visibility, audit failure risk | Slow incident response, inconsistent workflows | Basic malware goes undetected, but not enough on its own |
EDR vs MDR vs XDR vs SIEM vs SOAR vs Antivirus: Key Differences Explained
You’ve now seen what each of these tools does. But when it comes down to deciding between them, that’s where the real work begins.
This section breaks down the most commonly searched cybersecurity tool comparisons. These are the matchups teams debate during vendor shortlisting, board justifications, and late-night strategy calls. We’re not just comparing features. We’re helping you decide:
- Which tool fits your current environment?
- When does one replace the other or not?
- And what happens if you choose wrong?
Let’s start with the most foundational showdown: EDR vs MDR.
EDR vs MDR: Do You Need a Tool or a Team?
Both EDR and MDR promise one thing: detection and response. But how they deliver that promise couldn’t be more different.
EDR is like giving your team a scalpel, a microscope, and a forensic lab and saying, “Go stop threats.”
It’s software, deeply embedded in your endpoints. It tracks behaviors, flags anomalies, isolates infected systems, and collects telemetry in real-time. It’s powerful. But it assumes you have people who know what they’re looking at.

MDR, on the other hand, is like hiring a full surgical team that shows up when something goes wrong. It often includes EDR under the hood, but what you’re really buying is the human layer. Around-the-clock analysts. Threat hunters. Incident responders. They don’t just detect: they investigate, escalate, and sometimes remediate for you.
From a technical standpoint, EDR is typically faster and more customizable if your team knows how to use it. MDR trades some of that control for speed-to-expertise. You get 24/7 coverage without having to build it yourself.
So the choice isn’t purely technical — it’s operational.
Choose EDR if…
- You have a skilled in-house security team.
- You want full control over how threats are handled.
- You need fast detection at the endpoint level.
Choose MDR if…
- You don’t have 24/7 security staff.
- You need immediate coverage without the hiring pain.
- You want experts who can handle triage and escalation for you.
Datacipher Insight
Most organizations don’t realize that EDR isn’t “set and forget.” It needs tuning, attention, and response playbooks. If you don’t have a team for that, start with MDR and graduate to EDR when you’re ready to take the wheel.
EDR vs XDR: Are You Protecting Endpoints or Everything?
EDR and XDR share DNA. Both are about detection and response. Both aim to catch threats fast. But the difference is scope and strategy.
EDR focuses strictly on endpoints. Think laptops, desktops, servers. It monitors those devices in real-time, flags suspicious behavior, and gives you the ability to investigate or contain a threat on the spot. It’s focused, precise, and deeply effective at what it does, but it sees only one slice of the environment.
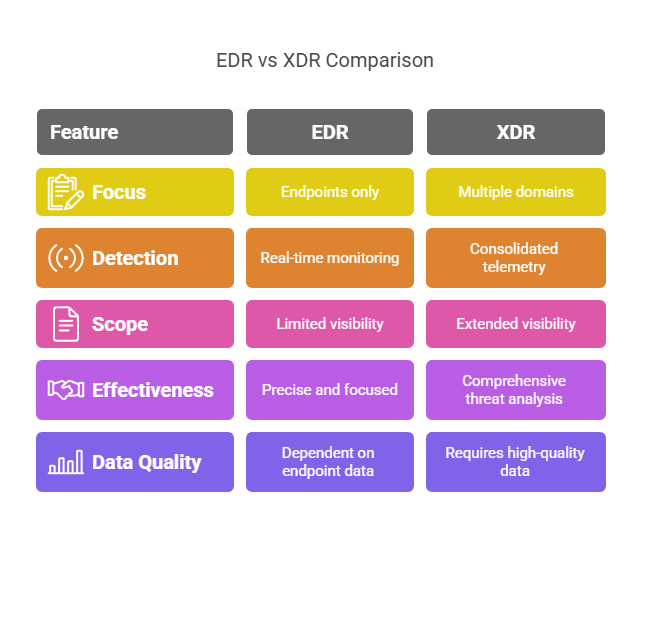
XDR takes that foundation and extends it. The “X” stands for “extended,” and it means visibility across multiple domains – not just endpoints, but also email, cloud workloads, identity systems, and network traffic. In other words, XDR connects the dots across your entire attack surface.
Technically, XDR consolidates and correlates telemetry from tools you’re already running. It reduces noise, identifies multi-stage attacks, and gives analysts a unified interface to investigate and respond. If EDR tells you who was compromised, XDR shows you how the compromise spread and where to shut it down.
But here’s the catch: XDR works best when it has access to high-quality data from across your stack. If your organization doesn’t yet have solid logging or coverage in cloud, email, and identity, XDR won’t reach its full potential.
Choose EDR if…
- You need a rock-solid solution for endpoint visibility.
- You’re just getting started and want focused protection.
- Your current stack is limited to endpoints.
Choose XDR if…
- You want cross-domain correlation (email, network, cloud, identity).
- Your team is overwhelmed by alerts from multiple tools.
- You want faster detection of complex, lateral threats.
Datacipher Insight
If your threat surface includes cloud services, remote workforces, or SaaS apps, XDR gives you the big-picture context that EDR can’t. But it’s only as good as the data it ingests. Start with EDR, but level up to XDR when you’re ready to unify your detection strategy.
EDR vs SIEM: Real-Time Reflexes vs. Strategic Visibility
At first glance, EDR and SIEM might seem to do the same thing. Both collect data, detect threats, and fire alerts. But under the hood, they’re built for completely different purposes.
EDR is your real-time reflex system. It watches what’s happening on your endpoints right now, process activity, user behavior, and file execution. It’s about catching bad stuff as it unfolds and giving you tools to respond immediately: isolate machines, kill processes, run forensic queries.
SIEM, on the other hand, is your long-term memory. It ingests logs from across your environment, not just endpoints but also firewalls, cloud apps, identity systems, and beyond. It’s where you correlate activity across weeks or months. It’s what you use for compliance, audit reporting, threat hunting, and deep forensic investigations.
In short:
- EDR shows you the breach happening today.
- SIEM helps you understand what led to it over the past month.
From a technical perspective, EDR is faster and lighter. SIEM is deeper and broader, but only if you have the time, resources, and rules to make sense of the data.
These tools don’t compete. They complement. But the confusion comes when teams assume a SIEM will do what EDR does or vice versa.
Choose EDR if…
- You need fast detection and response at the device level.
- You care more about stopping attacks than reporting on them.
- You have limited resources and want immediate security value.
Choose SIEM if…
- You need historical visibility across systems.
- You’re required to meet compliance and audit standards.
- You want to correlate logs across multiple tools and timeframes.
Datacipher Insight
If your team is small, start with EDR, as it delivers value faster. But if you’re in a regulated industry or need long-term investigation capabilities, a well-tuned SIEM is essential. Just don’t expect it to stop threats on its own.
EDR vs SOAR: Detection vs. Decision-Making on Autopilot
EDR is the tool that sees something suspicious and says, “Hey, look here.” SOAR is the system that says, “I already did.”
They’re not the same, and they were never meant to be.
EDR is built to detect threats at the endpoint and offer detailed visibility – file hashes, running processes, registry changes, network connections. It’s your magnifying glass and your panic button. It spots the threat and lets your analyst dig in, investigate, and decide what to do.

SOAR — Security Orchestration, Automation, and Response — steps in after the alert. It’s the air traffic controller. It receives signals from EDR, SIEM, XDR, or other tools and then follows a defined playbook: enrich the data, open a ticket, trigger a Slack alert, block an IP, isolate a host – whatever your team’s response workflow demands.
Where EDR excels in detection and containment at the endpoint level, SOAR shines in repeatability, speed, and scale. It reduces human fatigue. It handles repetitive tasks. And when implemented well, it ensures that every threat is handled the same way whether it happens at 2 p.m. or 2 a.m.
But SOAR is only as smart as the processes you feed into it. If your detection strategy isn’t already in place (with EDR, SIEM, or XDR), SOAR has nothing to act on.
Choose EDR if…
- You want deep visibility into endpoint activity.
- You need real-time containment on devices.
- You’re still developing your incident response workflows.
Choose SOAR if…
- You’re drowning in alerts and manual triage.
- Your team already knows what to do, but doing it takes too long.
- You need a faster, consistent execution of response actions.
Datacipher Insight
SOAR doesn’t replace EDR; it supercharges it. Start with solid detection and clear playbooks. Then, layer in SOAR to turn your analysts’ instincts into automated action. That’s where scale meets precision.
EDR vs Antivirus: Legacy Guard vs Intelligent Defense
This is the comparison most teams think they understand — but often don’t.
Antivirus (AV) is the original endpoint protector. It scans files, compares them to known signatures, and blocks anything that matches. It’s simple, fast, and low-cost. But that’s also the problem; modern threats don’t look like yesterday’s malware anymore.
EDR, by contrast, doesn’t just scan files. It watches behaviors, looks at what processes are doing, how users interact with systems, whether a PowerShell command suddenly downloads a remote payload, or if a trusted process behaves abnormally. It doesn’t just block known threats but investigates the unknown.
Technically, EDR includes antivirus-like protection as part of its baseline. But that’s just the start. EDR gives you real-time visibility, forensic data collection, alerting, triage workflows, and the ability to isolate compromised machines on the fly.
Antivirus tells you, “This file is bad.”
EDR tells you, “This behavior is suspicious, and here’s what happened before and after.”
So what’s the takeaway? Antivirus is a feature. EDR is a platform.
Choose Antivirus if…
- You’re a very small business with no IT staff.
- You’re running legacy systems that can’t support modern EDR agents.
- Budget is your only driver, and threat exposure is minimal.
Choose EDR if…
- You need proactive protection against unknown or evolving threats.
- You want visibility, not just blocking.
- You’re ready to move beyond “set and forget” security.
Datacipher Insight
AV is not a security strategy. It’s a safety net. If your current defense relies on antivirus alone, you’re operating on borrowed time. Transition to EDR the moment your business connects to the cloud, supports remote users, or holds any sensitive data.
MDR vs SIEM: Managed Eyes vs Internal Intelligence
MDR and SIEM often show up in the same conversation, but they solve very different problems, and in completely different ways.
MDR(Managed Detection and Response) is a service. You pay for a team of external experts to monitor, detect, investigate, and sometimes respond to threats in your environment often using their own tools. You’re outsourcing the brains and the boots.
SIEM, on the other hand, is a platform. It collects logs from across your environment — endpoints, cloud, firewall, identity systems — and gives you the ability to analyze and correlate them. But it won’t do the thinking for you. You still need humans to interpret the data, write detection rules, tune alerts, and manage the system daily.
Where MDR gives you outcomes — “We investigated this threat, here’s what we found”, SIEM gives you raw materials. It’s up to your team to extract insights and take action. That’s powerful if you’ve got a mature SOC. Dangerous if you don’t.
In short:
- MDR is buying expertise and response capacity.
- SIEM is building long-term security infrastructure.
Both can exist together. In fact, a good MDR provider may even use your SIEM. But you don’t choose them for the same reason.
Choose MDR if…
- You need 24/7 monitoring but can’t staff a SOC.
- You want immediate incident response without hiring a full team.
- You need outcomes, not dashboards.
Choose SIEM if…
- You already have a security team that knows how to handle alerts.
- You need historical visibility and audit trails.
- You want deep, long-term telemetry across all systems.
Datacipher Insight
If you’re early in your security maturity, MDR gives you a faster return on investment. SIEM becomes powerful when you have internal processes — or a partner — to make sense of the data. Don’t buy it just to “tick a box.”
MDR vs XDR: Managed Expertise vs Unified Detection
At first glance, MDR and XDR might look like competitors. Both promise detection, response, and coverage across multiple security layers. But the truth is: they aren’t the same type of offering at all.
MDR is a managed service. You get a team of experts who handle detection and response for you, often using a stack that includes EDR, log analysis, threat intelligence, and sometimes even XDR itself. What you’re buying is people. Human eyes. 24/7 monitoring. Incident reports in your inbox.
XDR is a technology platform. It’s the evolution of EDR — extended across endpoints, cloud, email, identity, and network. It automatically correlates signals across these layers to detect complex attacks that would otherwise slip through the cracks. It gives your team (or your MDR provider) the context they need to act faster.
Here’s the cleanest way to think about it:
- MDR uses tools (like XDR) to deliver outcomes.
- XDR is the tool.
In fact, many modern MDR services are built on top of XDR platforms. But XDR alone won’t solve your security staffing problem. And MDR without a strong underlying platform won’t scale effectively.
Choose MDR if…
- You don’t have a team to manage detection and response.
- You want outsourced security outcomes, not more tools to manage.
- You need fast, human-led triage and remediation.
Choose XDR if…
- You have a team but lack visibility across systems.
- You want correlated detection across endpoint, cloud, and identity.
- You need a centralized console for faster investigations.
Datacipher Insight
If you’re building from scratch, start with MDR. But make sure it runs on a platform like XDR. If you already have an internal SOC, XDR will supercharge their effectiveness. The best setups? MDR + XDR, working together with clear visibility and fast action.
XDR vs SIEM: Unified Detection vs Historical Visibility
This is one of the most strategic decisions security leaders face today. Both XDR and SIEM promise better visibility, smarter detection, and improved response. But how they get there (and what they prioritize) is fundamentally different.
XDR is designed for real-time, cross-domain threat detection. It connects endpoint, cloud, email, identity, and network signals into a single platform, automatically correlates events, and flags suspicious activity with rich context. Think of it as the next-gen SOC interface — made for faster detection and streamlined investigations.
SIEM, by contrast, is about centralized log collection and deep historical analysis. It ingests logs from everything: firewalls, servers, applications, cloud, OT systems. It’s not optimized for real-time correlation out of the box. But it gives you the raw data you need for audits, compliance, and forensic deep-dives.
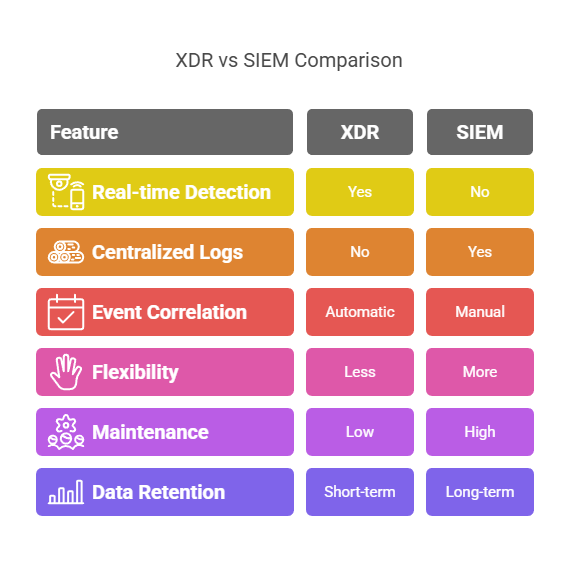
Here’s where people go wrong: they expect SIEM to behave like XDR. However, SIEM depends on rules and tuning. Without constant maintenance, it becomes a noisy log warehouse. XDR, on the other hand, comes pre-wired for faster detection. But it’s less flexible if you need long-term data retention or niche log sources.
In mature environments, they often coexist:
- XDR for real-time response.
- SIEM for compliance, visibility, and deep investigation.
Choose XDR if…
- You want faster detection across multiple threat vectors.
- You have an operational team that needs speed and context.
- You care more about stopping threats than storing logs.
Choose SIEM if…
- You need long-term log storage and custom reporting.
- You’re bound by regulatory or audit requirements.
- You have a team that can tune rules and queries.
Datacipher Insight
Don’t rip out your SIEM just because XDR looks shinier. But don’t build your modern detection stack only on SIEM either. For most organizations, the future is hybrid — XDR for front-line defense, SIEM for long-term visibility and evidence.
XDR vs SOAR: Context-Rich Alerts vs Coordinated Action
XDR and SOAR both live at the heart of modern security operations, but they solve two very different problems.
XDR is built for smart detection and correlation. It ingests data from endpoints, cloud, email, and identity systems. It automatically connects dots across those sources to surface sophisticated, multi-step attacks. It gives analysts context-rich alerts, attack timelines, and the ability to investigate fast – all in one console.
SOAR, meanwhile, exists to automate what happens next. Once a threat is detected (whether by XDR, SIEM, or anything else), SOAR follows a playbook. It enriches the alert with threat intel, assigns severity, creates a ticket, notifies the right team, and can even take automated action – block an IP, isolate a device, reset a user’s credentials.
Here’s the real difference:
- XDR helps detect faster and investigate smarter.
- SOAR helps respond faster and more consistently.
They don’t compete. They complete each other. XDR gives you clarity. SOAR gives you speed.
But don’t be fooled by automation hype: SOAR only works when you’ve mapped out your processes clearly. Without playbooks, it’s just a glorified orchestration tool with no real impact.
Choose XDR if…
- You want cross-domain visibility and faster triage.
- You need deeper insights into multi-stage threats.
- You have too many siloed alerts with no context.
Choose SOAR if…
- Your team is overwhelmed by alerts and repetitive tasks.
- You already know your response workflows but need to execute faster.
- You want to scale your SOC without hiring more analysts.
Datacipher Insight
XDR helps you see smarter. SOAR helps you act faster. If you’re already overwhelmed with alerts but still handling incidents manually, SOAR is your force multiplier. But make sure your detection layer (like XDR) is solid first.
SOAR vs SIEM: Centralized Logs vs Centralized Response
SOAR and SIEM are often bundled together in conversations – and sometimes even in vendor platforms – but their core purposes are completely different.
SIEM is all about log aggregation, search, and historical analysis. It pulls in structured and unstructured data from across your IT stack: endpoints, servers, firewalls, identity systems, SaaS apps.
You use it to detect anomalies, meet compliance requirements, and investigate incidents with a long tail.
SOAR, on the other hand, is about coordinated, automated response. It’s not focused on storing data; it’s focused on what happens after an alert is triggered. It connects your existing security tools and uses pre-built workflows (playbooks) to enrich, prioritize, and respond to threats automatically.
Put simply:
- SIEM is the brain that stores and studies.
- SOAR is the muscle that moves.
One digs deep. The other moves fast.
When used together, SIEM identifies what’s happening, and SOAR carries out the next steps without needing constant human involvement. But using SOAR without a good SIEM (or another detection engine like XDR) is like having a fire drill team and no smoke detectors.
Choose SIEM if…
- You need to collect and retain logs for audit, compliance, or long-term forensics.
- You have a team that can manage alerts, queries, and tuning.
- You want visibility into everything, even the noise.
Choose SOAR if…
- You’re already detecting threats but can’t keep up with response.
- You want to automate repetitive security tasks.
- You’re ready to codify incident response into playbooks.
Datacipher Insight
Most teams adopt SIEM first and SOAR later, and that’s smart. However, don’t assume SOAR will fix a noisy or poorly tuned SIEM. Get your detection foundation right, then layer SOAR to unlock speed, consistency, and scale.
EDR vs MDR vs XDR: Which One Actually Fits Your Security Strategy?
If you’re a growing organization trying to modernize your security posture, this is the fork in the road. EDR, MDR, and XDR are often pitched as must-haves, but choosing all three at once isn’t always realistic. And choosing the wrong one? That’s expensive.
So, let’s break it down.
EDR is your foundation. It lives on your endpoints. It sees what’s happening in real time. It gives you visibility and response power, if you have people to operate it. It’s best when you’ve got a small but skilled team that can triage alerts and run investigations.
MDR is the service layer. It’s not a tool; it’s a team. Usually built on top of an EDR (and increasingly, XDR), MDR gives you round-the-clock coverage without hiring full-time staff. Great for lean security teams or companies that want outcomes, not dashboards.
XDR is your visibility upgrade. It connects the dots across your environment — endpoint, email, identity, cloud, and network. It’s not just about seeing more; it’s about seeing smarter. It correlates activity and tells a richer story than EDR alone.

Here’s the secret most vendors don’t tell you: You’re not really choosing one over the other; you’re choosing your starting point.
Choose EDR if…
- You have an internal security team.
- You want deep visibility on endpoints and hands-on control.
- You’re building your stack layer by layer.
Choose MDR if…
- You need detection + response now but don’t have the staff.
- You want to offload triage, escalation, and investigation.
- You’re okay with a managed service operating your stack.
Choose XDR if…
- You’re struggling with alert fatigue from too many siloed tools.
- You want to correlate threats across endpoint, identity, cloud, and email.
- You already have security staff but need better signal-to-noise.
Datacipher Insight
Start with MDR if you need help now. Add EDR if you want control later. Invest in XDR if your visibility is fragmented and you need clarity across the stack. The smartest organizations use all three but in the right order, for the right reasons.
Still Confused? This Decision Matrix Will Help You Choose the Right Tool
By now, you’ve seen the breakdowns. You’ve compared tools side by side. But if you’re still asking:
“What’s the right tool for our size of team?”
“Should we start with EDR, or go straight to MDR?”
“Do we really need SOAR or is that overkill?”
Then this matrix is for you.
We created it based on real-world use cases we’ve seen across hundreds of organizations — from startups with no security staff to regulated enterprises building mature SOCs.
It maps out which tool fits which scenario using a simple, decision-friendly language:
- Yes – Strongly recommended based on this situation.
- Maybe – Could work depending on maturity, staffing, or existing tools.
- No – Not recommended as a first move in this situation.
You can use it as a starting point, not a prescription. Your environment might be unique. But if you’re unsure where to begin or which tool should come next in your stack, this matrix will give you clarity fast.
| Use Case | EDR | MDR | XDR | SIEM | SOAR | Antivirus |
| Small IT team, no dedicated security staff | No | Yes | No | No | No | Yes |
| Mid-sized org, needs 24/7 coverage but no SOC | Maybe | Yes | Maybe | Maybe | No | Yes |
| In-house SOC with strong analysts, needs deep endpoint visibility | Yes | No | Maybe | Yes | Yes | Maybe |
| Org struggling with alert fatigue and slow response | Maybe | Maybe | Yes | Yes | Yes | No |
| Compliance-heavy industry (e.g., finance, healthcare) | Yes | Maybe | Yes | Yes | Maybe | Yes |
| Mature team, needs automation and workflow orchestration | Maybe | No | Yes | Yes | Yes | No |
| Legacy systems, just need basic malware protection | No | No | No | No | No | Yes |
| Already using EDR, wants cross-domain correlation and context | No | No | Yes | Maybe | Maybe | No |
| Wants to reduce number of vendors and unify security view | Maybe | Maybe | Yes | No | Yes | No |
How Datacipher Helps You Choose, Implement, and Optimize the Right Security Tools?
No two security stacks are alike, and neither are the organizations behind them.
That’s why at Datacipher, we don’t just recommend tools. We help you build the right architecture, select the right vendors, and orchestrate it all into a security program that actually works for your business.
Whether you’re a fast-scaling company looking for MDR, a compliance-heavy enterprise refining your SIEM, or a security team trying to integrate EDR and SOAR – our team brings hands-on experience, sharp technical judgment, and vendor-agnostic clarity to every project.
We’ve worked with organizations worldwide to:
- Design and deploy endpoint protection strategies.
- Build detection and response workflows using SIEM, SOAR, and custom integrations.
- Implement managed security services that deliver 24/7 coverage without the hiring pressure.
- Optimize alert triage, reduce noise, and streamline incident response.
For instance, a mid-sized fintech had a small internal security team overwhelmed by alerts and blind spots across cloud, email, and endpoints. We implemented a managed XDR solution, fine-tuned detection rules, and automated their response workflows. Within weeks, they had 24/7 visibility, reduced noise, and faster incident response. All this without having to expand headcount.
You don’t need a dozen tools. You need the right combination tuned to your risks, people, and environment. And that’s what we do best.
Do you need help deploying the right solution for your organization? Talk to our cybersecurity experts, and we’ll help you map the path that fits best for you.