Endpoint security is no longer a “nice-to-have” – it’s a business imperative. In fact, compromised endpoints significantly account for breaches. If you’re reading this, you’re already aware of the risks every connected device poses. From laptops to smartphones, these endpoints are prime targets for cybercriminals. But the question is: how do you safeguard them effectively?
This endpoint security checklist will provide you with a practical, actionable guide to implementing a robust endpoint security strategy. You’ll learn exactly what needs to be in place, why it matters, and how to integrate it into your existing infrastructure without overcomplicating the process.
By the end of this article, you will have a clear roadmap to enhance your endpoint security posture, reduce risks, and ensure that every device within your organization is effectively secured.

1. Advanced Endpoint Protection (Beyond Traditional Antivirus)
In the age of sophisticated cyber threats, traditional antivirus software simply can’t keep up. According to the 2024 IBM Cost of a Data Breach Report, endpoint vulnerabilities were one of the top three initial attack vectors, contributing significantly to breach incidents. That makes relying solely on signature-based detection a dangerous gamble.
Advanced Endpoint Protection (AEP) is designed for today’s threat landscape. By combining AI, behavioral analytics, and real-time monitoring, AEP identifies threats based on how they behave—not just what they look like. It detects fileless malware, zero-day exploits, and other evasive tactics that traditional antivirus misses. Even better, it automates containment and response, reducing attacker dwell time.
If your endpoint protection still relies on outdated tools, you’re not secure—you’re exposed. AEP transforms your endpoints from liabilities into intelligent first lines of defense.
2. Extended Detection & Response for Real-Time Threat Hunting
Cyber threats are no longer confined to isolated parts of your network. To maintain robust security, comprehensive visibility across all platforms is essential. Extended Detection and Response (XDR) integrates data from endpoints, networks, and cloud environments, offering a unified security perspective.
Unlike traditional security tools that may operate in silos, XDR provides real-time threat hunting and accelerates response times. While specific metrics on XDR’s impact vary, the integration of advanced technologies like security AI and automation has been shown to significantly reduce the time to identify and contain breaches.
This unified approach enables security teams to correlate data from multiple sources, enhancing the detection of sophisticated attacks that might evade conventional defenses.
Implementing XDR transforms your security posture from reactive to proactive, ensuring that threats are not just detected but actively hunted and neutralized.
3. AI-Powered Ransomware Protection & Behavioral Analysis
Ransomware remains one of the most devastating cyber threats. In 2024, IBM’s Security X-Force reported that ransomware accounted for 20% of all cyber incidents. Traditional defenses often fail to detect new, sophisticated variants, making advanced protection essential.
AI and machine learning enable your endpoint security to identify ransomware behaviors before they execute. By analyzing endpoint activities, these advanced tools can detect unusual patterns, such as unauthorized data access or rapid file encryption, which are typical signs of ransomware attacks. The system then takes immediate action, isolating the affected endpoint and preventing further spread.
This proactive behavioral analysis minimizes the chances of ransomware infiltrating your network and ensures a faster, automated response to contain threats before they escalate.
4. Strict Endpoint Access Controls and Identity Management
Endpoints often represent the most vulnerable aspects of an organization’s security infrastructure, especially when unauthorized users can easily gain access. A Forrester study highlighted that 80% of IT security breaches involve privileged credential access. Without proper controls, attackers can exploit vulnerabilities and gain unauthorized access to sensitive data.
Implementing robust endpoint access controls is vital for defining who can access specific resources and under what conditions. Strong identity management practices, including multi-factor authentication (MFA) and least-privilege access principles, significantly limit exposure to critical systems. By ensuring that only authorized users can interact with essential resources, organizations can substantially reduce their attack surface.
Advanced endpoint security solutions offer integrated identity management, continuously verifying and authenticating user access in real-time. This approach ensures that only trusted devices and users are permitted to interact with your network, providing an additional layer of defense against unauthorized access.
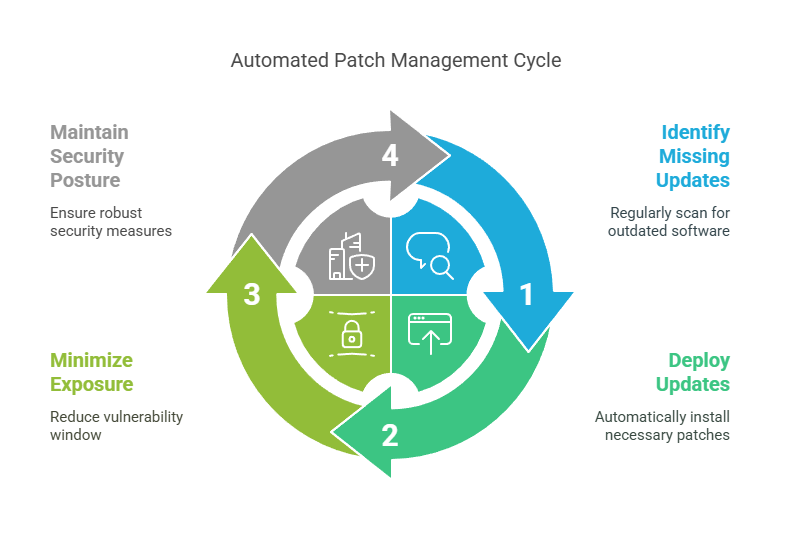
5. Patch Management and Software Update Automation
Outdated software remains one of the most exploited attack vectors.
Attackers often exploit such vulnerabilities to gain unauthorized access to endpoints and infiltrate networks, underscoring the critical need for effective patch management.
Automating patch management ensures that security updates are applied promptly, minimizing the window of exposure for potential exploits and maintaining a robust security posture. Endpoint security platforms with automated patching capabilities not only detect missing updates but also deploy them seamlessly, preventing vulnerabilities from being exploited.
Integrating automated patch management into your endpoint security strategy is essential for proactive defense, significantly reducing the risk of attacks stemming from unpatched vulnerabilities.
6. Zero Trust Policies for Endpoint Security
The traditional security model of trusting users inside the network perimeter is no longer sufficient. The 2024 Verizon Data Breach Investigations Report highlights that 68% of breaches involve a non-malicious human element, such as errors or social engineering attacks.
Zero Trust operates on the principle that trust is never implicit, regardless of whether the user is inside or outside the corporate network. Every access request is continuously verified, and every device, user, and application must be authenticated before any access is granted. This approach drastically reduces the risk of lateral movement by attackers and ensures tighter control over who can access critical systems.
Implementing Zero Trust for endpoint security means no device, whether employee or guest, gets a free pass. Only verified, authenticated users and endpoints can interact with sensitive resources, reinforcing your network’s security perimeter.
For a deeper dive into how organizations can secure their entire attack surface, including endpoints, check out the eBook 10 Essential Use Cases for Attack Surface Management. It covers how to gain visibility, reduce blind spots, and proactively mitigate endpoint security risks.

7. Data Encryption and Secure Backup Strategies
Data breaches often result in unauthorized access to sensitive information, leading to severe financial and reputational damage. Implementing robust data encryption ensures that even if attackers gain access to your endpoints, the information they obtain remains unreadable without the proper decryption keys.
Equally important are secure backup strategies. Automated backups, combined with encryption, provide a reliable recovery point in case of ransomware attacks or data corruption. This approach ensures your data is always protected and recoverable, minimizing downtime and maintaining business continuity.
Integrating both encryption and secure backup protocols into your endpoint security strategy is essential for preventing data theft and ensuring resilience against security incidents.
8. Endpoint Threat Intelligence and Proactive Monitoring
Traditional security solutions often react to attacks after they’ve occurred, leaving organizations vulnerable. Proactive threat intelligence and monitoring are essential to stay ahead of emerging threats. While specific metrics on the effectiveness of threat intelligence vary, integrating such intelligence enables security teams to identify and mitigate potential threats before they infiltrate systems.
Proactive monitoring, combined with endpoint threat intelligence, ensures continuous analysis of endpoints for anomalies, malicious activities, and potential risks. Utilizing real-time threat feeds allows security solutions to detect suspicious patterns and take immediate action, preventing breaches from escalating.
Integrating endpoint threat intelligence into your security infrastructure not only strengthens defenses but also aids in identifying zero-day vulnerabilities and threat actors, enabling proactive risk mitigation.
9. Compliance and Audit Readiness for Endpoint Security Standards
With increasingly strict regulatory requirements, ensuring compliance with security standards has become a major concern for businesses. Non-compliance can lead to significant financial penalties, reputational damage, and operational disruptions.
Endpoint security solutions must be configured to meet industry-specific regulations, such as GDPR, HIPAA, or PCI DSS. This includes ensuring that endpoints are protected against unauthorized access, data breaches, and other security risks that could result in non-compliance.
Implementing a solution that includes automated compliance checks, audit trails, and real-time monitoring helps businesses prepare for security audits and stay aligned with regulatory requirements. Proactive compliance ensures that endpoint security is continuously aligned with evolving standards, reducing the risk of costly penalties and reputational damage.
10. 24/7 Incident Response for Endpoint Breaches
A breach can occur at any time, and a swift response is critical to minimize damage. The 2024 IBM Cost of a Data Breach Report revealed that the global average cost of a data breach reached $4.88 million, a 10% increase from the previous year. Additionally, 70% of breached organizations reported significant or very significant disruption to their operations.
These statistics underscore the importance of having a robust incident response plan in place. A dedicated 24/7 incident response team ensures that when a breach is detected, it is contained immediately, minimizing potential damage. From detecting malicious activity to recovering compromised endpoints, having experts available around the clock significantly reduces the impact of cyberattacks.
The best endpoint security solutions integrate incident response directly into the platform, offering automated alerts, forensic analysis, and actionable insights to neutralize threats quickly. By providing continuous monitoring and rapid remediation, you ensure your organization is always prepared, no matter when a breach occurs.
Recommended Read: To optimize incident response and leverage automation for faster threat mitigation, explore the Practical Guide to Deploying SecOps Automation. This guide provides actionable insights on how to streamline security operations, reduce alert fatigue, and implement automated playbooks for endpoint protection.

Conclusion
Endpoint security isn’t just a checkbox; it’s the cornerstone of your cybersecurity strategy. In today’s world, where breaches are inevitable, the question is not if an attack will happen, but when. That’s why taking a proactive, comprehensive approach is essential to mitigate risks and protect your organization’s critical assets.
Datacipher’s endpoint security services offer a level of protection that goes beyond traditional solutions. With AI-powered threat detection, Extended Detection and Response, and real-time monitoring, Datacipher ensures that every device in your network is fortified against the most sophisticated attacks. Their 24/7 incident response and digital forensics ensure that, in the event of a breach, the impact is minimized, and recovery is swift.
When it comes to endpoint security, don’t settle for anything less than the best. Our solutions are tailored to meet the evolving needs of modern enterprises, ensuring your endpoints are always secure, compliant, and resilient.
Ready to protect your endpoints and stay ahead of evolving threats? Reach out to us today for a customized endpoint security strategy that will safeguard your business from the inside out.
CMO’s Note: Want a copy of this endpoint security checklist? Grab the PDF here.
Frequently Asked Questions
1. What is endpoint security, and why is it important for my business?
Endpoint security refers to the practice of protecting devices like laptops, smartphones, and desktops from cyber threats. These devices are often the entry points for attacks, and without robust endpoint security, businesses are vulnerable to breaches, data theft, and malware. Protecting endpoints is essential for securing your network and data integrity.
2. How does AI-powered endpoint security protect against advanced threats like ransomware?
AI-powered endpoint security uses machine learning to analyze patterns and detect anomalies in real-time. By recognizing the early signs of ransomware, like abnormal file encryption or suspicious user activity, AI can block attacks before they spread. It proactively defends against even the most advanced and previously unknown threats, ensuring fast, automated protection.
3. What should I look for when choosing an endpoint security provider?
Look for a provider offering comprehensive coverage, such as AI-driven threat detection, 24/7 monitoring, incident response, and zero trust policies. The provider should offer customizable solutions tailored to your business needs and ensure regulatory compliance. Additionally, check for scalability and integration capabilities with your existing IT infrastructure.
4. Why is patch management critical for endpoint security, and how can it be automated?
Patch management is crucial because unpatched software is a major attack vector. Hackers often exploit vulnerabilities in outdated software to gain access. Automating patch management ensures that updates are applied as soon as they’re released, reducing the risk of security breaches and keeping your endpoints consistently protected without manual intervention.
5. How does endpoint encryption protect sensitive data on devices?
Endpoint encryption protects sensitive data by converting it into unreadable code, ensuring that even if a device is compromised, the data remains inaccessible. With full-disk or file-level encryption, your business ensures that valuable information is secure both in transit and at rest, safeguarding against data theft or unauthorized access.





