Compliance certifications aren’t just a regulatory requirement. They’re a business necessity. Yet, many organizations fail to achieve compliance due to avoidable mistakes, delaying certification and exposing themselves to security risks, penalties, and reputational damage.
From ISO 27001 and PCI DSS to HIPAA and GDPR, each standard comes with complex security requirements that businesses often misinterpret or overlook. The result? Audit failures, security gaps, and compliance roadblocks that slow down operations and increase risks.
Every failed attempt costs time, money, and credibility. Yet, the same compliance pitfalls keep surfacing. This article uncovers nine critical mistakes that prevent businesses from getting certified and how to fix them before they derail your certification process.
#1. Lack of Asset Visibility and Inventory Management
Most compliance failures start with a simple problem: you can’t secure what you don’t see. Businesses often assume they have full control over their IT environment, but without a complete asset inventory, critical systems go unnoticed.
Unmonitored devices, outdated applications, and shadow IT introduce vulnerabilities that slip past security teams and raise red flags during audits.
Regulatory frameworks like ISO 27001 and NIST require organizations to track all assets handling sensitive data. If auditors discover missing records or unaccounted systems, certifications can get delayed or denied.
Gaps in asset visibility also lead to poor risk assessments, making it impossible to implement the right security controls. A structured, automated asset discovery process can solve this problem. Tools like Qualys, Tenable, and Axonius continuously map IT assets, ensuring nothing slips through the cracks.

Further, keeping an updated Configuration Management Database, regularly validating assets, and aligning with compliance checklists can prevents blind spots that could cost businesses their certification.
Recommended Read: Want to gain complete visibility into your IT environment and eliminate security blind spots? Download our free eBook 10 Essential Use Cases for Attack Surface Management to learn how proactive asset discovery can prevent compliance failures.

#2. Prioritizing Vulnerabilities based on Risk
Not all security risks are equal, yet many businesses treat them that way. Compliance frameworks like PCI DSS, ISO 27001, and NIST require organizations to assess vulnerabilities based on real-world risk impact. But too often, teams either fix low-risk issues first or take a checklist approach that doesn’t address their biggest security gaps.
Ignoring high-risk vulnerabilities creates an illusion of compliance while leaving critical systems exposed. Attackers normally target high-severity flaws that provide the easiest access.
Certification auditors look for a structured approach to risk-based vulnerability management. If they find unaddressed critical vulnerabilities, compliance can be denied.
A smarter approach involves using tools like Tenable.io, Qualys VMDR, or Rapid7 InsightVM to continuously scan for vulnerabilities and rank them based on exploitability.
Further, prioritizing fixes based on CVSS scores, asset criticality, and real-time threat intelligence ensures that the most dangerous gaps are closed first.
Without a structured risk-based approach, compliance is just a checkbox that won’t hold up when a real attack happens.
#3. Weak Access Controls & Privileged Account Mismanagement
Access management is at the core of every compliance framework, yet businesses often fail to enforce strict access policies, leaving critical systems exposed.
Regulations like PCI DSS, HIPAA, and ISO 27001 mandate role-based access control (RBAC), multi-factor authentication (MFA), and least privilege policies, but many organizations still rely on default credentials, shared logins, or excessive admin privileges that create compliance risks.
Privileged accounts are the biggest target for attackers. If an auditor finds poor access governance, weak authentication controls, or inactive privileged accounts, certification can be delayed or revoked. Insider threats are also a major risk. When employees or contractors have unrestricted access to sensitive data, the chances of accidental or malicious misuse increase.
Fixing access control weaknesses starts with implementing Privileged Access Management (PAM) solutions like CyberArk, BeyondTrust, or HashiCorp Vault to enforce just-in-time access and strict credential rotation.
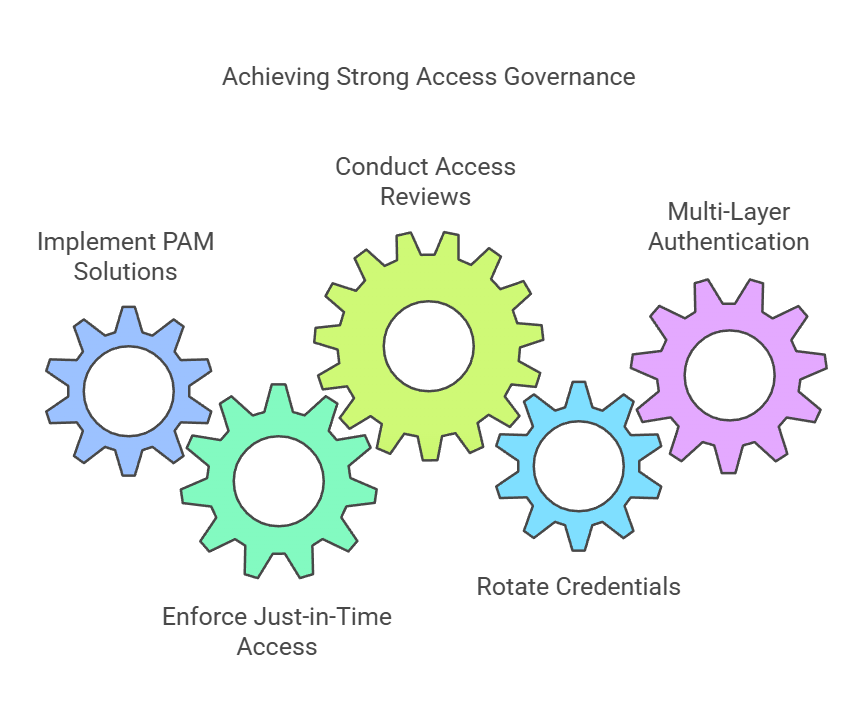
Organizations should also conduct regular access reviews, deprovision inactive accounts, and enforce multi-layer authentication to meet compliance standards. Without strong access governance, even the most secure systems remain vulnerable to breaches and compliance failures.
#4. Failure to Encrypt Sensitive Data
Encryption isn’t just a best practice – it’s a compliance mandate under PCI DSS, HIPAA, and GDPR. Yet, businesses still store sensitive data in plaintext, exposing it to unauthorized access and breaches.
Without end-to-end encryption, attackers can intercept payment details, patient records, and confidential business data, leading to compliance violations and hefty fines.
Regulations require encryption for data at rest and in transit, but many organizations fail to implement strong cryptographic controls. Weak or outdated encryption methods, missing encryption keys, and unsecured backups create gaps that auditors won’t overlook.
A compliance-ready approach includes using AES-256 encryption for stored data, TLS 1.3 for network security, and enterprise-grade key management solutions like AWS KMS, HashiCorp Vault, or Thales CipherTrust.
Encrypting data, at the end of the day, is not just about passing audits. It’s about keeping critical assets safe from real-world threats.
#5. Poor Incident Response and Lack of Security Monitoring
For most companies, a security breach is inevitable. Compliance frameworks like NIST, ISO 27001, and HIPAA require businesses to have a structured incident response plan, yet many organizations fail to detect and respond to threats in time.
Without continuous monitoring, attacks can go undetected for weeks, leading to data loss, regulatory penalties, and certification failures. Auditors look for real-time threat detection, automated alerting, and well-documented response plans.
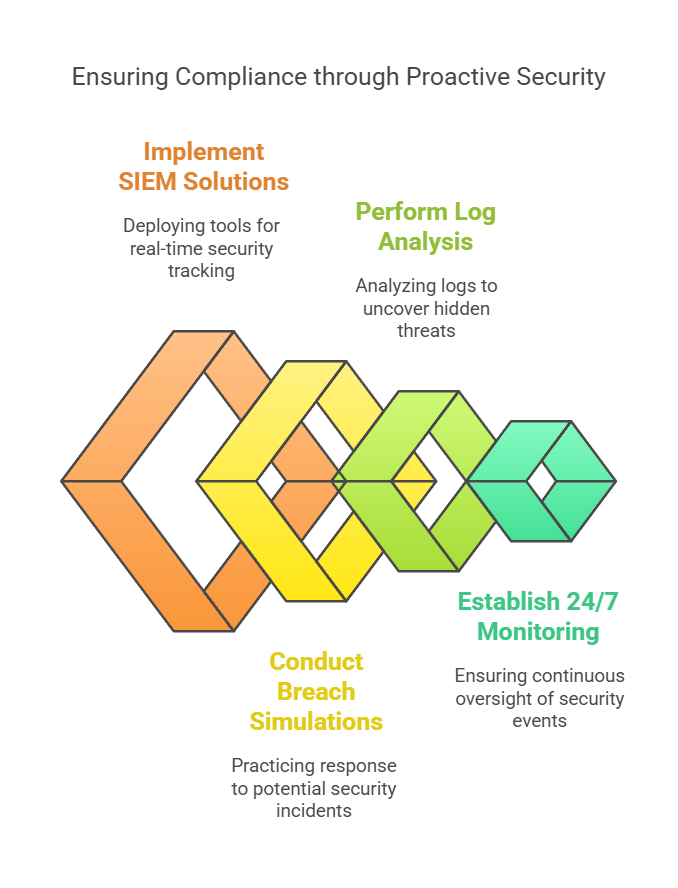
Companies that lack Security Information and Event Management (SIEM) systems, fail to conduct breach simulations, or ignore log analysis often fall short in compliance audits.
A proactive approach involves deploying SIEM solutions like Splunk, IBM QRadar, or Microsoft Sentinel to track security events in real time. Regular incident response drills and 24/7 monitoring further ensure that threats are detected and neutralized before they escalate into compliance disasters.
#6. Non-Compliance with Third-Party Vendor Security Requirements
Compliance doesn’t stop at internal security. Third-party vendors handling sensitive data must also meet regulatory standards. Frameworks like PCI DSS, GDPR, and NIST require businesses to assess vendor security, yet many companies fail to enforce strict controls. Weak vendor security can introduce data breaches, compliance violations, and legal liability.
Auditors look for documented vendor risk assessments, security audits, and compliance certifications. Companies that don’t vet third-party security policies or fail to include compliance clauses in vendor contracts risk failing audits.
A strong vendor compliance strategy includes risk management platforms like OneTrust or BitSight, regular third-party security assessments, and strict access controls for external partners. Without these safeguards, a vendor’s security lapse can become your compliance nightmare.
#7. Outdated or Missing Security Policies & Documentation
Compliance requires well-documented security policies that align with frameworks like ISO 27001, HIPAA, and GDPR. Yet, many businesses fail because their policies are outdated, incomplete, or missing altogether. Without clear guidelines, employees lack direction on data handling, access control, and incident response, increasing the risk of compliance violations.
Auditors expect policy-driven governance, meaning companies must regularly update security policies, document risk assessments, and maintain compliance records. Failing to do so can lead to certification delays, fines, or outright non-compliance.
A structured approach includes automating policy management with platforms like Confluence or Tugboat Logic, conducting annual policy reviews, and ensuring all employees are trained on updated security protocols. Compliance isn’t just about meeting technical standards. It’s about proving that security is an ongoing priority.
#8. Failure to Conduct Regular Security Awareness Training
Even the strongest security controls can fail if employees don’t understand compliance requirements. Regulations like NIST, ISO 27001, and HIPAA mandate ongoing security awareness training, yet many companies treat it as a one-time event—or skip it entirely. Without proper training, employees fall victim to phishing attacks, weak password practices, and data mishandling, leading to compliance violations.
Auditors look for proof of regular security training programs, phishing simulations, and employee compliance assessments. Organizations that can’t demonstrate consistent training efforts risk failing audits and exposing themselves to preventable security breaches.
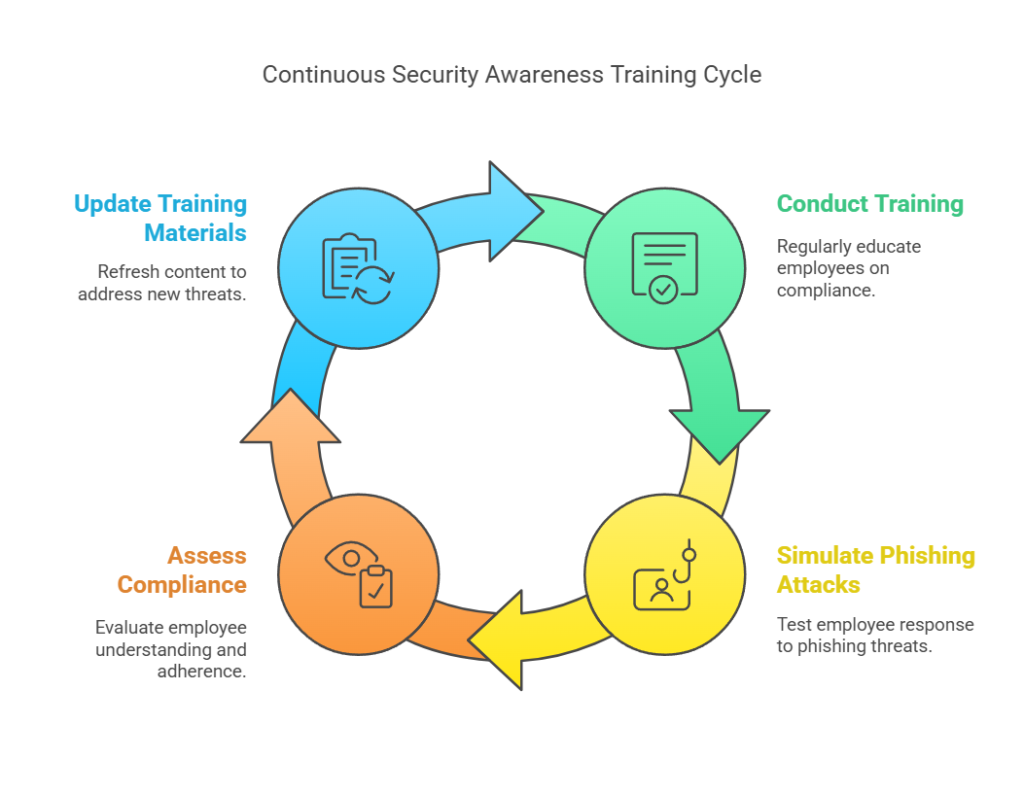
A proactive approach includes using training platforms like KnowBe4 or Cofense PhishMe to educate employees on real-world threats, secure data handling, and compliance best practices.
#9. Lack of Continuous Compliance Monitoring and Auditing
Many businesses treat compliance certification as a checkbox exercise, failing to implement continuous monitoring and regular audits. Regulations like PCI DSS, NIST, and ISO 27001 require organizations to track compliance in real time, but without automated systems, gaps go unnoticed until the next audit—often when it’s too late.
Auditors expect evidence of continuous security monitoring, internal audits, and compliance tracking. Businesses that rely on manual assessments or infrequent compliance checks risk missing critical security lapses that lead to failed certifications.
Using compliance automation tools like Drata, Secureframe, or Vanta ensures that security controls remain consistently enforced. Regular internal audits and real-time compliance dashboards help organizations stay ahead of evolving regulations, reducing the risk of last-minute compliance failures.
Get Compliance Right with Datacipher
Avoiding compliance pitfalls isn’t just about checking boxes. It’s about ensuring your business stays secure, audit-ready, and fully certified. However, getting compliance certified can be a tough nut to crack. But a proven compliance consulting partner that makes the process seamless.
Here’s why you should choose Datacipher for Compliance Consulting:
- Expertise across all Major Standards – Whether it’s PCI DSS, HIPAA, GDPR, ISO 27001, NIST, or CIS, our experts know exactly what it takes to pass audits.
- End-to-end certification support – We don’t just identify gaps, we fix them, guiding you from risk assessment to final certification.
- Custom compliance strategies – Every business is unique. We tailor our approach to fit your industry, infrastructure, and security needs.
- Continuous monitoring and Risk management – Compliance isn’t a one-time event. We help you maintain security standards year-round with automated audits and proactive risk assessments.
- Fast, hassle-free process – Say goodbye to compliance roadblocks. Our streamlined approach helps you get certified faster and with fewer complications.
Don’t leave compliance to chance. Partner with Datacipher and turn compliance from a burden into a competitive advantage. Schedule a consultation with our experts now.
Frequently Asked Questions about Compliance Consulting and Certification
#1. What does a compliance consulting firm do, and why do businesses need one?
A compliance consulting firm helps businesses navigate complex regulatory frameworks, ensuring they meet standards like PCI DSS, HIPAA, and ISO 27001. Without expert guidance, companies risk audit failures, legal penalties, and security breaches. A trusted compliance partner streamlines the process, helping businesses get certified faster and avoid costly mistakes.
#2. How does compliance advisory differ from compliance auditing?
Compliance advisory focuses on guidance, strategy, and implementation, helping businesses prepare for certification and build security frameworks. Auditing, on the other hand, is a formal evaluation of existing compliance efforts to determine gaps, risks, and violations. Advisory helps businesses achieve compliance, while auditing ensures they maintain it.
#3. What industries benefit the most from compliance consulting services?
Industries handling sensitive data need compliance consulting the most. This includes finance (PCI DSS), healthcare (HIPAA), SaaS & tech (ISO 27001), and government (NIST, CIS). Without expert guidance, businesses in these industries risk fines, lawsuits, and reputational damage due to non-compliance.
#4. What are the biggest challenges businesses face in achieving PCI DSS compliance?
The top challenges include complex security controls, strict access management, encryption requirements, and continuous monitoring. Many businesses also struggle with third-party security risks. Without a structured approach, PCI DSS compliance can be overwhelming. This can lead to audit failures, security gaps, and potential payment processing restrictions.
#5. How does ISO 27001 help businesses improve cybersecurity?
ISO 27001 provides a structured framework for managing information security risks. It ensures strong access controls, data encryption, risk assessments, and continuous monitoring, thus reducing the risk of breaches, insider threats, and regulatory fines. Beyond compliance, ISO 27001 certification enhances customer trust and strengthens business resilience.
#6. What are the steps to achieving ISO 27001 certification?
ISO 27001 certification involves risk assessment, security framework development, employee training, internal audits, and external certification audits. Businesses must implement an Information Security Management System (ISMS) to meet ISO standards. A compliance consulting firm streamlines the process—ensuring businesses pass audits efficiently and without costly missteps.





