For many security teams, the early signs of SOC strain don’t show up as red alerts. They show up in the gaps.
You’ve got tools. A few good people. Maybe you’re logging events, responding to the obvious stuff, and pulling reports when auditors ask. But threats are evolving. And quietly, so are the cracks.
Maybe you’re:
- Over-relying on analysts who double as architects and responders.
- Missing critical alerts during off-hours due to the lack of 24×7 coverage.
- Struggling to meet compliance or prove that you are.
- Facing board pressure to mature security without a clear path.
This is where the real decision surfaces: Build a full-fledged SOC or shift key functions to a managed partner?
We created this article for decision-makers sitting with the weight of that question. We’ll break down what building an in-house SOC really entails, what managed SOCs actually deliver, and why some organizations thrive with one model while others quietly struggle.
If you’re facing this fork in the road – whether due to scale, compliance, breach recovery, or sheer operational fatigue – this guide is designed to give you the clarity that surface-level conversations skip.
Let’s start with what it costs to build an in-house SOC.
What It Really Takes to Build an In-House SOC?
Once the decision to build a SOC comes up, many organizations assume it’s just about hiring a few analysts and deploying tools.
In reality, building a true in-house SOC means taking ownership of three interconnected pillars: people, process, and technology. Miss one, and the entire structure becomes fragile.
And while the idea of internal control sounds appealing, the real cost—financial, operational, and strategic—is often underestimated.
Here’s what it actually involves in 2025.
#1. People: The Most Expensive (and Volatile) Line Item
Staffing a functional SOC isn’t about headcount; it’s about coverage.
To maintain 24/7 operations, organizations typically require at least 12–15 full-time professionals, spanning Tier 1, Tier 2, incident response, threat intelligence, and management.
- The average salary for a Tier 1 security analyst is over $90,000/year in North America. In India, the salary for such roles averages around Rs. 600,000. Senior roles demand far more. Multiply that by shifts, overheads, and ongoing training, and costs quickly add up.
- Burnout is also a major concern. Reports cite that 71% of SOC analysts experience high stress, and 64% cite burnout as a reason to quit.
#2. Process: What Makes a SOC Operational, Not Just Present
Technology is only as effective as the processes behind it. An in-house SOC needs more than incident response checklists. It requires a culture of continuous improvement.
- You’ll need escalation matrices, reporting SLAs, threat hunting playbooks, and post-incident review cycles.
- Regulatory alignment is also an ongoing burden. In 2024, 89% of IT compliance teams reported unresolved audit issues tied to third-party or internal process gaps.
And that’s assuming your team has the time to keep tuning those processes. Most don’t have the luxury.
#3. Technology: The Stack isn’t Just Expensive, it’s a Maze.
Most companies start with a SIEM. But a mature SOC tech stack includes EDR, SOAR, NDR, TIP, UEBA, and integrations across cloud providers, firewalls, SaaS apps, and identity management tools.
- In 2024, 73% of SOCs reported using SIEMs, while 74% deployed NDR solutions, a sign of the expanding baseline.
- A full tech stack can cost $500K–$1.1M just to implement, before licenses, upgrades, and staffing.
And then there’s integration. Many tools don’t work together out of the box. That means custom engineering, not just clicking “next.”
#4. Time and Resource Commitment: It Doesn’t End at Launch
Even after the initial build, you’re only halfway there. Reaching a “steady state” SOC takes time, tuning, and executive patience.
- Most organizations report a 6–12 month ramp-up period before their SOC is even semi-reliable.
- During that window, you’re likely under-covered, over-alerted, and constantly justifying ROI.
#5. Strategic Fit: Not Can You Build, but Should You?
Even if you have the budget and ambition, the deeper question is whether you have the alignment. You need to answer these questions, too:
- Does your core business model justify this level of operational ownership?
- Can your team scale and maintain this complexity year over year?
- Will you be more secure or just more distracted?
This is why many enterprises start with a build mindset. But they later transition to managed or co-managed models once the realities set in.
Transitioning from the challenges of building an in-house SOC, many organizations are exploring Managed SOC solutions to address their security needs more effectively. Let’s look at the range of benefits managed SOCs offer that can alleviate the burdens faced by internal teams.
What Managed SOCs Actually Deliver?
Managed SOCs are not just “outsourced monitoring.” When done right, they offer mature, round-the-clock security operations backed by experienced analysts, proven playbooks, and modern detection technology.
They’re built to deliver consistency at scale. They do it without burning your team out or blowing up your budget.
In this section, we’ll break down exactly what Managed SOCs bring to the table. From 24/7 coverage and faster response to the tools and talent most internal teams can’t justify. Managed SOCs deliver maturity right from day one.
1. Comprehensive 24/7 Monitoring and Rapid Response
Managed SOCs provide around-the-clock surveillance of your IT environment, ensuring that threats are detected and addressed promptly. Continuous monitoring is crucial in reducing the average dwell time of attackers.
2. Access to Specialized Expertise
With the cybersecurity talent shortage affecting 70% of companies, the risks are mounting. Managed SOCs offer access to experienced security professionals who can handle complex threats and evolving compliance needs. This level of expertise is often difficult and expensive to maintain in-house.
3. Advanced Technology Stack Integration
Managed SOC providers invest in a wide range of cutting-edge technologies including SIEM, EDR, SOAR, NDR, UEBA, and threat intelligence platforms. This ensures clients benefit from deep visibility, faster detection, and automation without the capital expenditure required to build and maintain these tools in-house.
4. Cost Efficiency and Predictable Budgeting
Building and maintaining an in-house SOC can be financially demanding. Managed SOCs offer a more predictable and often lower-cost alternative, allowing organizations to allocate resources more efficiently.
5. Enhanced Compliance and Reporting
Managed SOCs assist in meeting regulatory requirements by providing detailed logs, reports, and audit-ready documentation. This level of support is essential for maintaining compliance with standards like HIPAA, PCI DSS, and GDPR. It helps organizations avoid costly penalties and maintain customer trust in the face of increasing scrutiny.
6. Scalability and Flexibility
As organizations grow or face changing security landscapes, Managed SOCs can scale services accordingly, offering flexibility that aligns with business needs without the delays associated with scaling internal teams.
This is what effective security operations look like; someone else is running them, but your business still stays in control.
Want to see how leading organizations transform their SOCs to meet today’s threat landscape? Check out the free eBook: Five Essential Steps to SOC Transformation. The ebook offers a practical roadmap for boosting efficiency, reducing analyst burnout, and integrating AI and automation for faster response.

In-House SOC vs Managed SOC: Five Strategic Lenses that Can Help You Decide
At this point, you’ve seen both sides: the effort required to build a SOC in-house, and what a Managed SOC can deliver from day one.
Now comes the real decision: What fits your organization’s needs, maturity, and priorities?
Here are five lenses that can help you evaluate the right path forward:
1. Speed to Maturity
If you need a fully operational SOC in weeks, not months or years, a Managed SOC will give you faster time to value.
In contrast, building internally may suit companies with longer timelines and dedicated in-house security architects.
2. Depth of Internal Capability
Do you already have a lean security team that knows your environment but needs help scaling?
A Managed SOC can provide that muscle, or even just Tier 1 and Tier 2 coverage, while your team owns response. Interestingly, that’s where co-managed SOCs often emerge: a hybrid model that extends what you already have, without handing everything off.
3. Control and Customization
Some sectors – especially in regulated industries – prefer tight control over response workflows and alert logic. If that’s you, make sure any Managed SOC (or co-managed setup) supports custom playbooks and escalation paths, not just out-of-the-box automation.
4. Budget Flexibility
Building a SOC is CapEx-heavy and front-loaded. Managed SOCs shift this into predictable OpEx, often making it easier to scale gradually. But cost should be tied to coverage: if your current exposure is global, cloud-first, or compliance-heavy, a stronger investment is non-negotiable.
5. Leadership Bandwidth
Perhaps the most underrated question is: Do you want your leadership team spending its time building a SOC or strengthening your business?
If you’re stretched thin, the value of a Managed SOC isn’t just tech or talent, it’s focus.
At the end of the day, it’s about finding the model that meets your needs now and evolves with you later. Whether it’s fully managed, hybrid, or something in between, the decision has to align with the realities of your risk, pace, and vision.
Choosing the Right SOC Model: A Side-by-Side Comparison
By this point, you’ve explored the full picture: what it takes to build internally, what Managed SOCs deliver, and how co-managed models fit in between.
However, when decisions reach the boardroom or budgeting phase, clarity becomes crucial.
This table provides a simplified, side-by-side comparison of the three primary SOC models—In-House, Managed, and Co-Managed. This can help you assess which one aligns with your technical capabilities, risk appetite, and resource availability.
Comparison Table: In-House vs. Managed vs. Co-Managed SOCs
| Factor | In-House SOC | Managed SOC | Co-Managed SOC |
| Initial Investment | High (CapEx-intensive: infrastructure, tools, staffing) | Lower (OpEx model with subscription-based services) | Moderate (shared investment in tools and resources) |
| Time to Maturity | 12–24 months to achieve full operational capability | Access to the provider’s expert team, reducing internal hiring pressures | 60–120 days, depending on existing infrastructure and collaboration level |
| Talent Dependency | Full responsibility for hiring, training, and retaining skilled personnel | Access to provider’s expert team, reducing internal hiring pressures | Shared responsibility; internal team augmented by provider’s expertise |
| 24×7 Coverage | Requires multiple shifts and significant staffing | Provided by the service provider as part of the package | Collaborative approach to ensure round-the-clock monitoring |
| Control Over Response | Full control over incident response protocols and decision-making | Provider-led response with predefined SLAs and protocols | Joint control; customized response strategies developed collaboratively |
| Technology Ownership | Complete ownership and maintenance of all security tools | Provider supplies and manages the technology stack | Hybrid model; some tools owned by the organization, others by the provider |
| Compliance Alignment | Internal team ensures adherence to compliance standards | Provider assists with compliance reporting and adherence | Shared efforts to meet and maintain compliance requirements |
| Scalability | Scaling requires significant internal resources and planning | Easily scalable through provider’s infrastructure and resources | Flexible scaling by leveraging both internal and provider capabilities |
| Best Suited For | Large enterprises with substantial resources and need for complete control | Small to medium-sized enterprises seeking quick deployment and cost efficiency | Medium to large enterprises desiring a balance between control and outsourced support |
Note: The timeframes and suitability may vary based on specific organizational needs, existing infrastructure, and the chosen service provider’s capabilities
How Datacipher Delivers SOC Maturity Without the Overhead?
When building or scaling a Security Operations Center, speed, visibility, and cost alignment matter.
That’s where Datacipher comes in. We offer Managed SOC services built for modern enterprises, across cloud-first, hybrid, and compliance-intensive environments.
With a focus on real-time threat detection, incident response, and compliance management, our solutions are tailored to meet the unique challenges faced by organizations in today’s digital landscape.
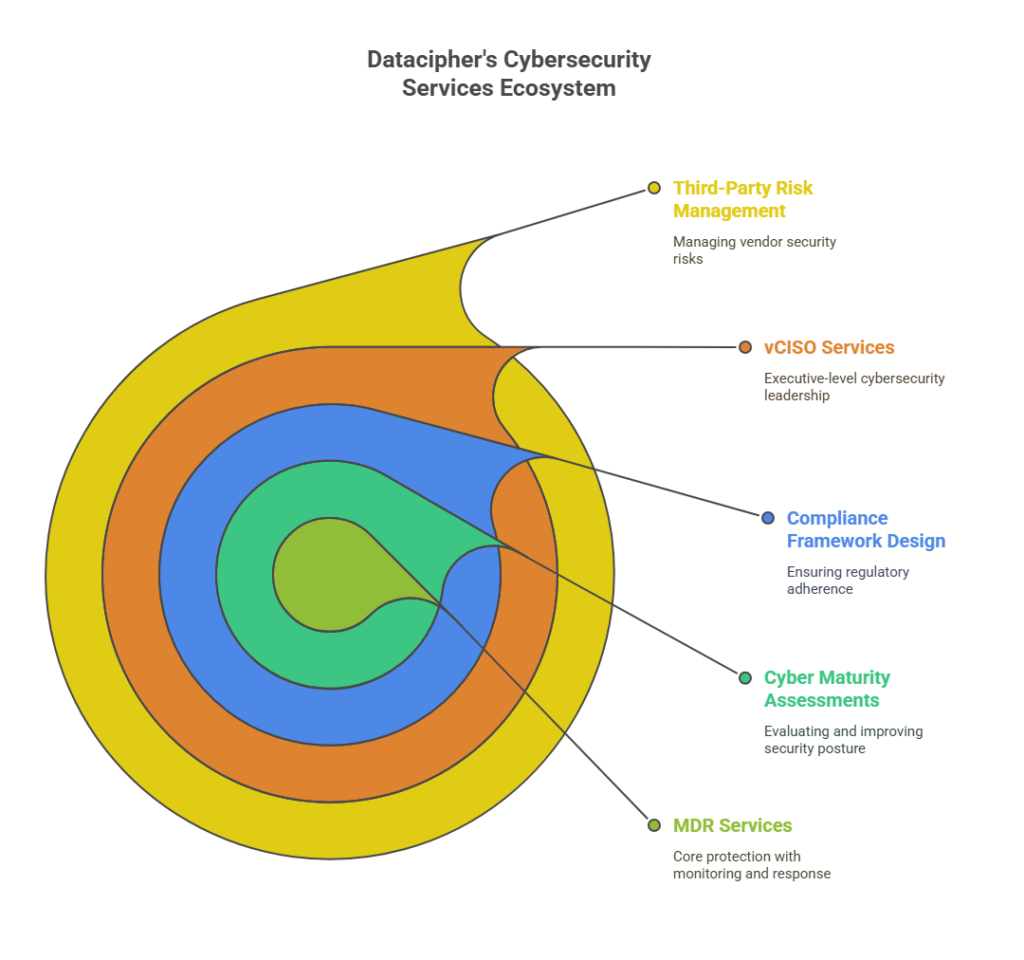
Source – Datacipher
Key Capabilities we offer include:
24×7 Managed Detection and Response
Our MDR services provide always-on monitoring and real-time threat detection across your entire IT and cloud environment. Our SOC analysts continuously triage alerts, escalate critical incidents, and guide containment and remediation. Whether it’s during business hours or at 3 a.m. We leverage advanced analytics, threat intelligence feeds, and attacker behavior models to reduce dwell time and improve response accuracy.
Cyber Maturity Assessments and Security Audits
Our cyber maturity assessments benchmark your security posture against frameworks like NIST CSF, ISO 27001, and CIS Controls. We identify technical gaps, policy weaknesses, and operational blind spots. We then map them to risk categories that are understandable across IT, GRC, and leadership. These insights support compliance, improve board reporting, and form the foundation for strategic roadmap planning.
Compliance-Ready Framework Design and Certification Support
Whether you’re preparing for ISO 27001, GDPR, or India’s DPDPA, we help design and implement right-sized security frameworks that fit your business model. Our consultants ensure that every control is both technically feasible and auditor-friendly, reducing delays during certification. From risk assessments and SoA development to internal audits and ongoing advisory, we support the full compliance lifecycle.
vCISO as a Service
Our Virtual CISO model gives you executive-level cybersecurity leadership without the cost of a full-time hire. The vCISO helps define your security vision, align controls with business risk, lead policy and strategy development, and present security metrics that resonate at the board level. This service is ideal for mid-sized firms scaling security maturity or enterprises that need dedicated leadership during transformation. For a detailed list of vCISO providers, for enterprises, this article can come in handy.
Third-Party Risk Management
We help you build and operate a structured third-party risk program, from onboarding assessments to continuous vendor monitoring. We evaluate supplier access, cloud integrations, contract risk clauses, and NIST 800-161-aligned controls to ensure vendors don’t introduce hidden exposure.
We also help you design governance workflows, scoring models, and response plans for critical suppliers and high-risk partnerships.
Cloud Security and Automation
We protect your SaaS, IaaS, and hybrid environments using automated guardrails, cloud-native controls, and identity-centric security models. Whether you’re running workloads in AWS, Azure, GCP, or containers in Kubernetes, we help you achieve visibility, compliance, and incident response readiness across platforms.
Our approach integrates with your CI/CD pipelines and DevSecOps workflows to make cloud security scalable, not manual.
Case in point – A regional engineering consultancy with over 2,000 employees and growing cloud dependencies was increasingly targeted by phishing campaigns and credential theft attempts. While the IT team had endpoint protection and a firewall in place, they lacked real-time threat visibility, centralized log analysis, and round-the-clock response capability.
After partnering with us for a fully managed SOC, the company gained 24/7 threat monitoring across endpoints, email, and cloud infrastructure. We deployed a customized detection stack with SIEM, EDR, and cloud log ingestion, while also delivering weekly threat reports and compliance-aligned incident tracking.
In less than four months, the firm reported:
- 45% reduction in time-to-detect phishing and access anomalies
- 100% coverage during nights and weekends
- And the successful mitigation of a credential-stuffing attack that would’ve otherwise gone undetected.
Do you also want to know where your SOC stands? Let’s assess your current coverage, identify blind spots, and develop a plan tailored to your operational model. Schedule a SOC Readiness call here.
Frequently Asked Questions
#1. What’s the difference between a Managed SOC and MDR?
Managed SOCs provide end-to-end security operations, including monitoring, triage, response, and compliance reporting. MDR focuses specifically on detection and response, often limited to endpoints or networks. While MDR is tactical, a Managed SOC offers full operational maturity with strategic oversight.
#2. Is it possible to transition from in-house to a Managed SOC without disrupting operations?
Yes. Most mature Managed SOC providers offer phased transitions. They work alongside your internal team to integrate toolsets, replicate playbooks, and take over monitoring in stages. This avoids operational gaps while maintaining incident coverage throughout the switch.
#3. Can a Managed SOC integrate with my existing security tools and platforms?
Absolutely. Good providers support integrations with leading SIEMs, firewalls, cloud platforms, and identity tools. Whether you’re using Microsoft Sentinel, Palo Alto Cortex, AWS CloudTrail, or Okta, the managed SOC provider can ingest logs and enrich detection without requiring a full rip-and-replace.
#4. Are Managed SOC services suitable for organizations in highly regulated industries like healthcare or finance?
Yes. In fact, they’re often ideal. Leading providers build compliance into their service from HIPAA and PCI DSS to GDPR and India’s DPDPA. They deliver audit-ready reports, custom workflows, and data residency assurances tailored to your regulatory obligations.





