Most enterprises do not fail because they lack good technology. They fail because their tools, processes, and security layers were never designed to work together at scale.
At some point, every infrastructure and security leader faces the same decision: Do we build integration capabilities ourselves or bring in outside expertise?
Both paths come with trade-offs. In-house teams offer control and continuity. External partners offer speed, specialization, and proven frameworks.
The dilemma is real. Choosing the wrong path can waste budgets, delay critical projects, and expose systems to long-term risk.
This guide breaks down the decision without bias. You will learn when it makes strategic sense to build internally, when to outsource integration, and what questions you need to ask before committing either way.
Because integration is not just about stitching systems together. It is about future-proofing how your enterprise operates, secures, and scales. Let’s get started.
Why Enterprises Struggle with System Integration Today?
System integration today is not a wiring project. It is a battle against complexity that touches every part of the enterprise. This includes security, infrastructure, compliance, and operations.
Here is where most teams start losing ground:
#1. Cloud Sprawl
Most enterprises no longer run in a single environment. Applications live across AWS, Azure, GCP, private clouds, and edge sites. Moreover, each has its access policies, telemetry standards, and integration quirks.
There is no default blueprint to tie them together. Every new workload multiplies the integration surface, while security visibility falls further behind.
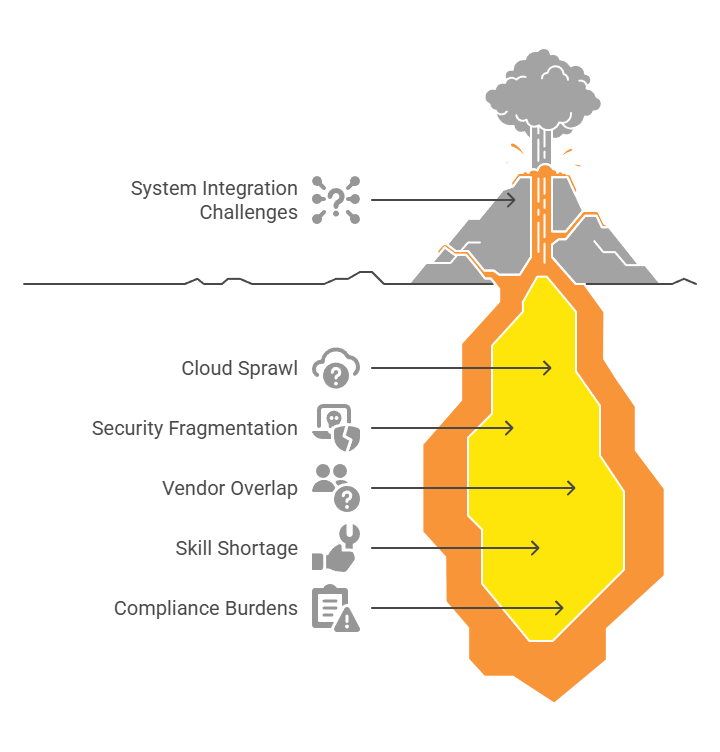
#2. Security Fragmentation
In most enterprises, identity lives in one platform. Threat detection in another. Audit logging in the third. When incidents happen, no single system can stitch the story end-to-end.
Without proactive integration, enterprises are blind at the worst possible moments. This could be during lateral movement, privilege escalation, or credential theft.
#3. Vendor Overlap
Point solutions pile up fast: firewalls, endpoints, ZTNA, CASBs, cloud gateways. Each vendor solves one problem but introduces new operational friction.
Teams end up toggling between consoles, reconciling duplicate alerts, and missing critical anomalies hidden between tool silos.
#4. Skill Shortage
Building integration today is not just networking or scripting. It takes architects who understand security models, automation specialists who can handle API orchestration, and cloud engineers who can span multi-cloud complexity. Very few internal teams have all these capabilities in one place, under one roof.
#5. Compliance Burdens
Regulations such as DPDPA, GDPR, and industry frameworks (e.g., HIPAA, PCI-DSS) require enterprises to demonstrate access control, incident response timelines, and auditability across fragmented systems.
Without integrated telemetry and identity mapping, even basic compliance reporting becomes an operational nightmare. And that’s a massive legal risk.
Internal IT teams were not built for this world. They were built to keep known systems running, not to orchestrate fragmented, fast-moving ecosystems under the pressure of regulatory and security concerns.
This is why choosing how to approach system integration today is not a cost decision. It is a resilience decision.
Why Modern System Integration Breaks Internal Teams?
Building integration sounds simple on paper. Until the environment starts growing faster than the team can control it. This is where it starts to break:
Cloud Sprawl Breaks Visibility
One cloud environment is manageable. Two are survivable. Three clouds, multiple regions, hybrid apps, and suddenly the security team cannot answer basic questions anymore: Who owns which workload? Where is policy enforced? Who has access?
Every new cloud link multiplies the attack surface and fragments monitoring.
Security Fragmentation Breaks Incident Response
Identity lives here. Logs live there. Threat detections trigger somewhere else. When an incident occurs, no system can cleanly stitch the attack path. Every minute lost to manually stitching logs is a minute that adversaries can use to move laterally. Blame games start. Postmortems get ugly.
Vendor Overlap Breaks Operational Flow
Firewalls here. EDR there. CASB somewhere else. Each tool solves one piece. None solving the whole flow. Teams spend hours pivoting across dashboards, reconciling events manually, missing real patterns hidden between silos.
Skill Shortage Breaks Project Execution
Good integration is not plug-and-play. It requires engineers who can orchestrate cloud APIs, identity federation, network segmentation, and telemetry pipelines simultaneously. Most teams have specialists.
But Integration needs system architects. Without them, integration turns into a firefighting effort.
Compliance Pressure Breaks the Audit Chain
Auditors are asking for proof of access trails, encrypted flows, and incident timelines across cloud, network, and endpoint. Without integrated telemetry and policy maps, reporting becomes a manual process. Deadlines slip. Confidence erodes.
Internal IT teams were not built for this battlefield. They were built to maintain systems that already worked. Today, those systems are dynamic, fragmented, and constantly changing under pressure.
Integration failure is no longer a technical problem. It is an existential risk to uptime, compliance, and trust.
Recommended Resource: For a deeper dive into how leading enterprises are modernizing their security operations, explore our Five Essential Steps to SOC Transformation guide. It provides practical strategies to consolidate operations, reduce tool sprawl, automate resilience, and future-proof your security landscape.

This is where experienced system integrators shift the dynamic. They are not just additional hands. They bring frameworks, multi-domain expertise, tested resilience patterns, and operational discipline that internal teams often struggle to build from scratch under pressure.
Outsourcing integration to the right partner helps enterprises:
- Rebuild visibility across fragmented environments.
- Embed security and compliance directly into integration points.
- Reduce dependency on narrow skill silos.
- Accelerate delivery without stacking operational debt.
- Standardize telemetry and reporting across ecosystems.
It does not erase the complexity. But it prevents complexity from collapsing the system.
Outsourcing can inject specialization, speed, and structure into a process that otherwise grinds internal teams down over time.
Still, outsourcing is not always the right answer. Neither is building everything in-house by default.
The right decision depends on your enterprise’s specific realities: your internal capabilities, your integration urgency, your risk exposure, and your growth horizon.
Let us break it down.
In-House vs Outsourced System Integration: How They Compare
Choosing between building integration internally or partnering with external specialists is not just a cost decision. It is a bet on what your enterprise can execute faster, deeper, and more securely under real-world pressure.
Both paths come with real strengths and real risks.
Here is how they truly compare when you break it down across the dimensions that matter most in modern environments:
| Factor | In-House Integration | Outsourced Integration Partner |
| Control | Full internal control over architecture, timeline, tooling, and standards. | Strategic control retained, but operational delivery is shared with the partner. |
| Speed of Execution | Slower unless internal teams have cross-domain integration expertise ready. | Faster due to existing playbooks, frameworks, and specialized deployment teams. |
| Expertise Depth | Dependent on internal team skills; often strong in some domains, weaker in others. | Access to full-stack expertise across network, cloud, security, automation, and compliance. |
| Cost Visibility | Lower short-term cost, but risks hidden costs from delays, scope creep, and failed rollouts. | Higher upfront cost, but stronger long-term predictability through scoped outcomes. |
| Risk Management | Higher risk if integration complexity, vendor coordination, or compliance impact is underestimated internally. | Shared risk. Partners operationalize complexity, handle vendor interoperability, and embed resilience upfront. |
| Scalability | Hard to scale rapidly without stretching internal teams thin or hiring new resources. | Easier to scale projects with modular external teams and flexible resource allocation. |
| Focus and Strategic Alignment | Diverts internal teams from long-term innovation and strategic programs. | Frees internal teams to focus on core enterprise priorities while integration is handled professionally. |
| Operational Resilience | Depends on internal monitoring, troubleshooting, and post-deployment maintenance capability. | Best partners design for operational resilience from day one, including failover handling and observability. |
No path is automatically better. It depends on where your enterprise is starting from and complexity, urgency, and operational risk you can afford to manage directly.
Understanding these real trade-offs is what separates integration projects that scale from those that stall.
When In-House Integration Makes Sense and When Outsourcing Wins?
As I mentioned earlier, the answer depends on your current environment, team capability, and business pressure. Here is when building integration internally makes sense:
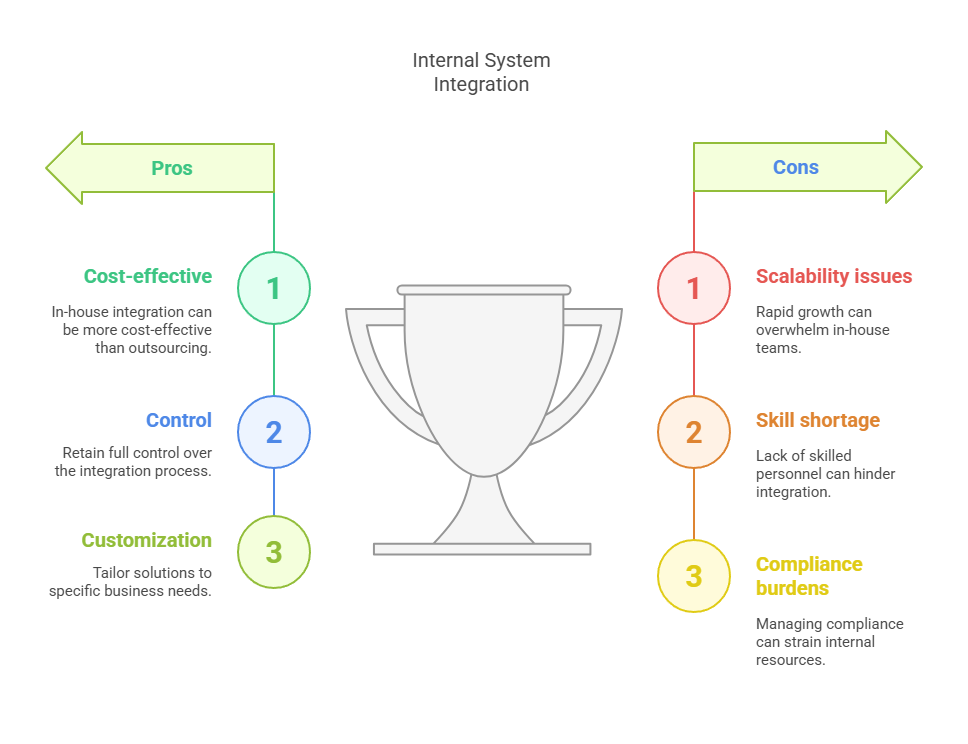
- You have deep, cross-domain internal expertise ready today: You have actual architects, security engineers, network specialists, and automation leads who have already built and operated complex multi-vendor environments.
- You can afford slower execution without risking business outcomes: In-house integration usually moves slower. If your projects can accommodate longer timelines without compromising security posture, compliance obligations, or go-to-market agility, internal execution may be suitable.
- You want total control over design and operational standards: If your enterprise has extremely custom security models, regulatory environments, or internal architectural standards that third parties would struggle to meet, keeping integration in-house protects consistency.
- You have leadership alignment to invest long-term: Integration skills are not one-time needs. They require continuous training, re-architecting, and expansion as systems evolve. If leadership commits not just to project budgets but to integration maturity as a strategic discipline, in-house teams can succeed.
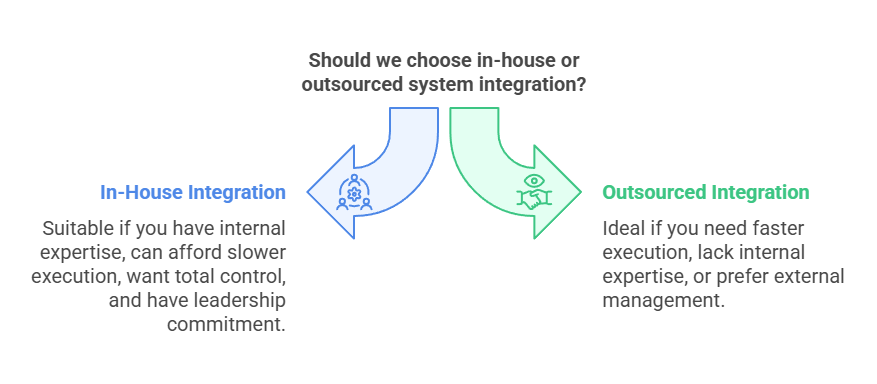
Outsourced Integration wins when:
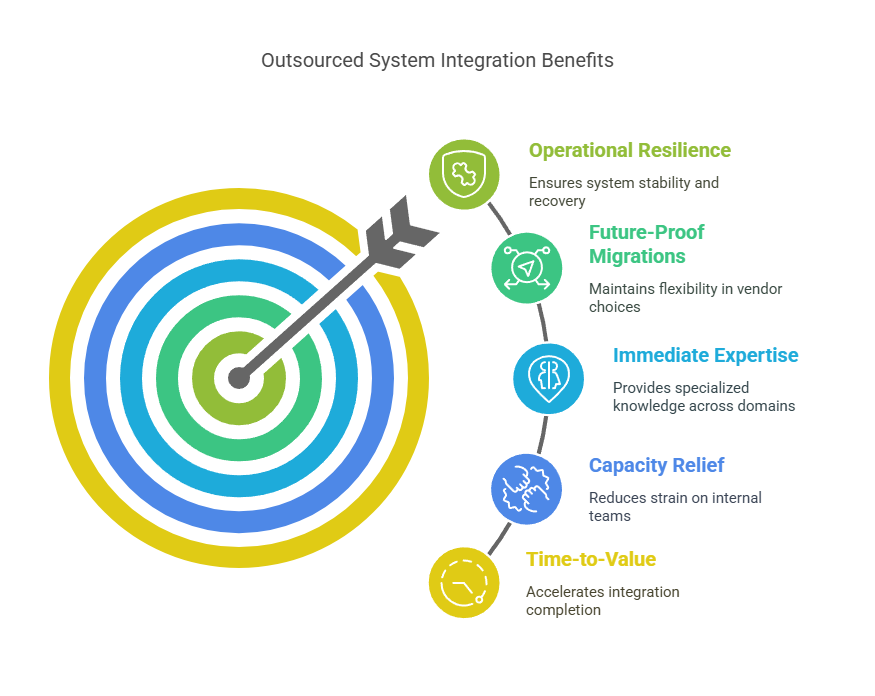
- Time-to-value is critical: If you need integration completed in quarters, not years, and cannot afford an internal “learning on the job” curve, partners with proven playbooks accelerate success.
- Internal teams are already stretched thin: Most enterprise IT and security teams today are overloaded with BAU (business-as-usual) operations. Adding full-scale integration projects often breaks existing support capacity and increases attrition risk.
- You need immediate cross-domain expertise: Few internal teams have simultaneous strength across networking, cloud orchestration, Zero Trust architecture, security telemetry integration, and compliance traceability. Good integrators bring modular teams ready for these intersections.
- Operational resilience cannot be compromised: Integration today is not about “make it work.” It is about making it observable, recoverable, and compliant under attack or outage. Partners who design for resilience from the outset significantly reduce operational risk later.
- You want to future-proof migrations: locking integrations to specific vendors, clouds, or toolchains can trap enterprises in the long term. Good integrators build vendor-neutral frameworks that keep migration options open as strategy evolves.
Building internally preserves control but demands depth, patience, and long-term investment. Outsourcing delivers acceleration, resilience, and scale. However, it requires trust, collaboration, and careful selection of partners.
There is no shortcut to good integration. Only the choice between building capabilities yourself or getting specialized teams that already have them.
We have seen where in-house integration struggles and where outsourcing can bring real advantages. The next follow-up question is: How to choose the right system integrator?
Because not all system integrators are created equal. Choosing poorly can leave you with more fragmentation, hidden risks, and larger operational gaps than you started with. Choosing well can turn integration from a bottleneck into a competitive advantage.
What to Look for in an Ideal System Integration Partner?
Choosing a system integrator is not about who can connect boxes faster. It is about who can engineer real outcomes in real-world complexity. They should be able to do this without cutting corners that can create problems later.
Here is what serious enterprises look for when trust, uptime, and security are on the line:
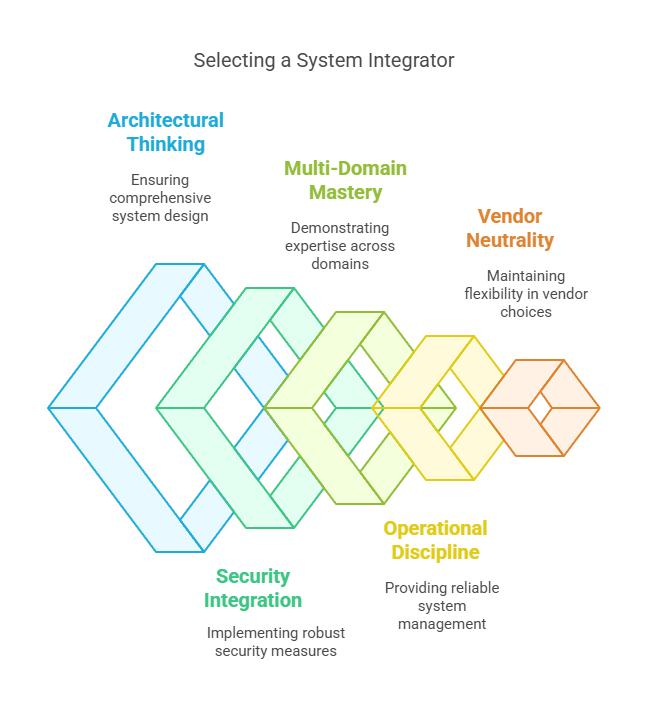
1. End-to-End Architectural Thinking
Good integrators do not just wire systems. They design for visibility, policy flow, resilience, and compliance from the first diagram to the last deployment step.
If a partner cannot show you architectural discipline, not just technical skills, they are not ready for real integration work.
2. Security Built from the Ground Up
Integration is where most breaches start. Not because teams ignored security, but because it was never designed in. The right partner enforces Zero Trust principles, encrypts every connection, builds strong authentication across layers, and audits everything they integrate.
3. Multi-Domain, Multi-Vendor Mastery
Real integration today cuts across networking, security, cloud orchestration, automation, and identity. It crosses AWS and Azure. Palo Alto and Cisco. Fortinet and VMware. The right partner can move across domains and vendors seamlessly without losing design clarity or operational resilience.
4. Proven Operational Discipline
Building the connection is only half the job. Running it, monitoring it, and recovering it under stress is what separates serious integrators from slide deck architects. One should look for partners who live inside incident response SLAs, who design for observability, and who can show you how systems behave under real pressure.
5. Vendor Neutrality and Migration Foresight
Good integrators build modular, standards-driven architectures that allow your enterprise to evolve without rewriting the foundations every time you change vendors or platforms.
A good integration today should never trap tomorrow’s strategy.
Choosing an integration partner is not about who promises the fastest go-live. It is about who engineers for resilience, security, and scale. And that’s the reason why enterprises today trust Datacipher solutions.
Why Enterprises Trust Datacipher for Complex System Integrations?
At Datacipher, we do not just connect systems. We build architectures that deliver visibility, resilience, security, and scale under real-world operational pressure.
Here is what sets us apart:
Source – Datacipher
Proven Track Record across Industries
With over 650 successful projects and a client base spanning telecom, ITES, manufacturing, education, and government. Datacipher has consistently delivered integration outcomes that withstand scale, audits, and live production demands.
Vendor-Neutral, Standards-Driven Engineering
We design integrations that fit your strategy, not lock you into a single vendor roadmap. Our solutions work seamlessly across AWS, Azure, GCP, private clouds, and hybrid environments future-proofing your architecture.
Security Embedded by Design
Security is not layered on later. Zero Trust principles, encrypted communications, role-based access, and compliance observability are embedded from the first connection to the last deployment.
Global Reach, Local Execution Strength
Operating across India, the US, UK, Australia, Europe, the Middle East, and Africa, Datacipher combines global best practices with local delivery expertise to meet the specific regulatory and operational needs of every enterprise we serve.
Recognized and Certified Expertise
Datacipher holds Elite Plus Partner status with Palo Alto Networks and Juniper Networks in India, alongside partnerships with leading security and networking vendors globally.
Our deployment-led focus ensures that what is designed, actually works, at scale, in production.
Case in Point: Mahindra & Mahindra
When Mahindra needed to modernize and integrate their core infrastructure, they trusted Datacipher to deliver. Our team engineered a future-ready, secure network foundation that unified hybrid cloud operations, improved security visibility, and simplified operational management.
You can watch the transformation story below:
If you are ready to stop managing system silos and start scaling a secure, visible, and resilient enterprise, we are here to help.
Contact our experts today to turn complexity into clarity and your architecture into advantage.
Frequently Asked Questions
#1. What are the hidden costs enterprises often overlook during in-house integration?
In-house integration often hides costs like talent burnout, project delays, duplicated tool investments, manual compliance reporting overhead, and expensive rework after security audits. The upfront project estimate rarely captures the long-term operational drag of incomplete, brittle, or non-resilient integrations that cannot scale cleanly.
#2. Can a system integrator customize solutions for highly regulated industries like BFSI or healthcare?
Yes. Specialist system integrators build industry-specific architectures that align with regulations like DPDPA, HIPAA, PCI-DSS, and GDPR. Customization includes encrypted workflows, compliant identity management, traceable telemetry, and audit-ready access logs—engineered directly into the integration blueprint, not added later as patches.
#3. What mistakes should enterprises avoid when outsourcing system integration?
The biggest mistakes are choosing on price alone, outsourcing without internal ownership, ignoring operational resilience, and failing to align business outcomes before kickoff. Without disciplined scoping, partner accountability, and visibility-first design, even external projects can stall or collapse.
#4. What is the difference between an IT services provider and a specialist system integrator?
An IT services provider focuses on staffing, maintenance, or break-fix support. A specialist system integrator engineers cohesive environments across network, security, cloud, and automation, embedding resilience, visibility, and compliance from day one.
#5. Does working with a system integrator mean losing control over architecture decisions?
Not with the right partner. Good system integrators work as extension teams, not as black boxes. You retain control over standards, policy decisions, and long-term architecture strategy.