Today, about 86% of organizations run multicloud environments. They juggle AWS, Azure, GCP, and sometimes even a few on-prem holdouts. This setup gives them flexibility, scale, and vendor leverage. But it also hands their security teams a new kind of challenge.
Each cloud provider brings its own architecture, tools, and identity systems. Each adds another layer to monitor. Another language to interpret. And another set of risks to manage. For security teams, that means more attack surfaces. More signals to sift through. And more chances for something critical to slip through the cracks.
This is where your Managed Security Services Provider is supposed to step in. But too many are still stuck in a single-cloud mindset. They collect alerts. Forward threats. And send the same templated PDF at the end of the month.
What you need is unified visibility. You need response orchestration across platforms. A partner that understands how to secure the space between the clouds.
So, how do you know if your MSSP is truly built for multicloud? Or just pretending to be?
In this article, we’ll break down what real multicloud readiness looks like in a security partner. We’ll also explore why most providers fall short and what to demand if you want visibility, control, and protection in 2025 and beyond.
What to Expect from an MSSP in a Multicloud World?
The average organization has 351 exploitable attack paths spread across its multicloud environment. That’s a reality most security teams are quietly drowning in.
One path might begin with a misconfigured storage bucket in AWS. Another, with an over-permissioned workload identity in Azure. Yet another slips in through a forgotten container running on GCP. None of them looks critical in isolation. But together, they map a highway straight to your most valuable assets.
And most MSSPs don’t see the full map. They treat each cloud like a silo. They surface isolated alerts but never connect the dots. In a multicloud world, that’s not just outdated. It’s dangerous.
True multicloud security demands more than log forwarding and monthly reports. It demands a partner who can correlate, prioritize, and act across a fragmented, fast-changing threat surface.
So, what should you expect from a Managed Security Services Provider that claims to be multicloud-ready?
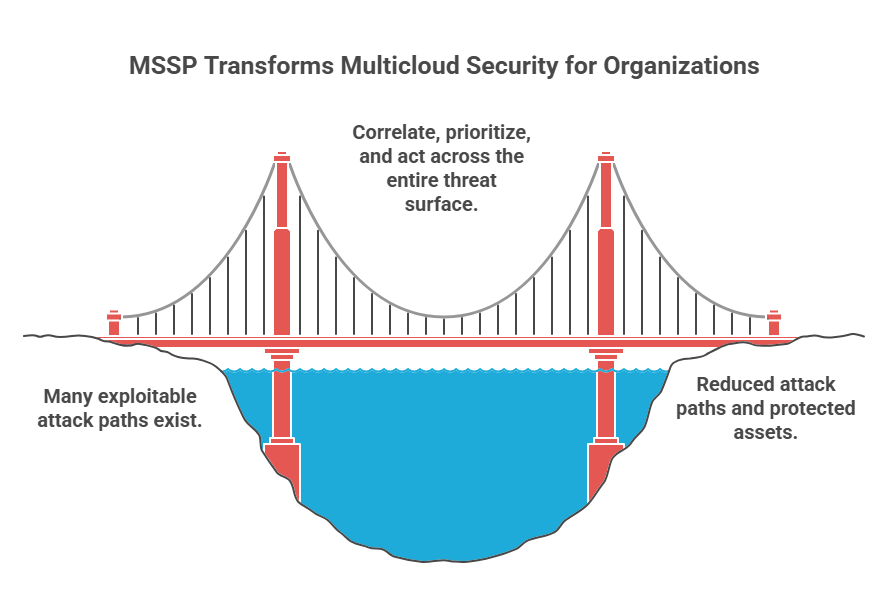
Here’s the benchmark.
Six Capabilities Every Multicloud MSSP Must Deliver
Not all MSSPs offer the same depth of capability. Many can manage perimeter security. Fewer can handle cloud workloads. And only a handful are truly built to secure fragmented, fast-moving multicloud environments.
Before signing with a provider, these six capabilities should be non-negotiable. If they’re missing even one, you risk having blind spots in your security coverage.
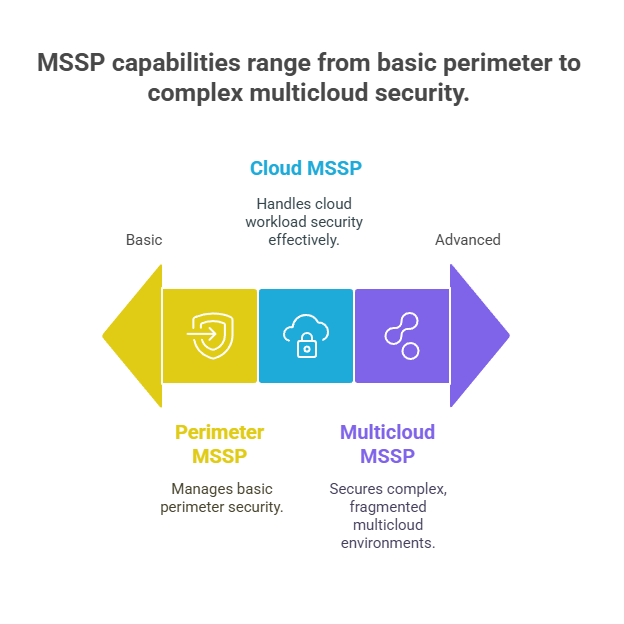
#1. Cloud-Native Tool Integration
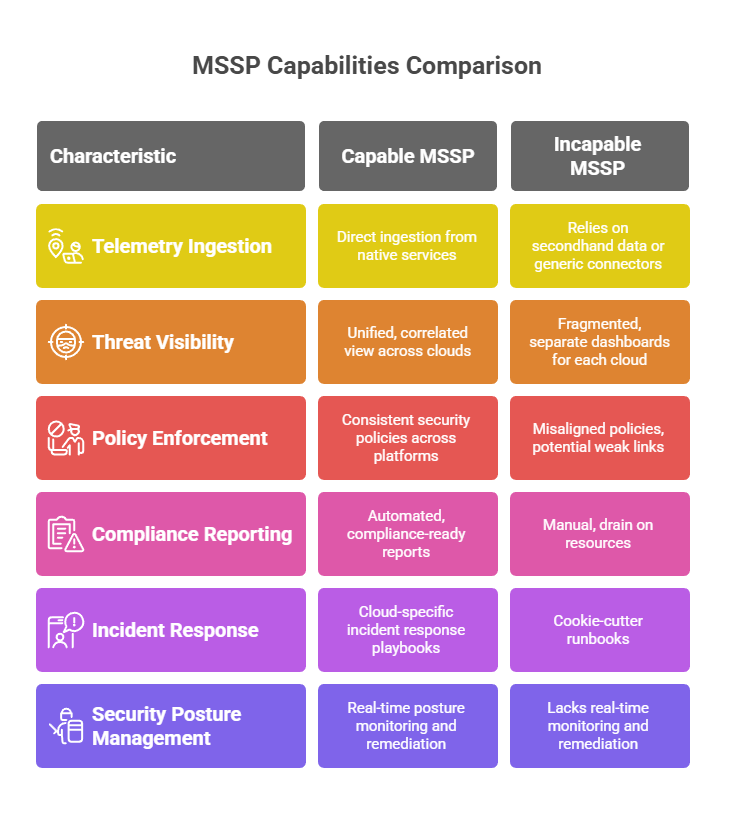
A capable MSSP doesn’t just monitor alerts. It connects directly to native services like AWS CloudTrail, Azure Monitor, and GCP Logging to ingest telemetry at the source.
These native logs reveal who did what, when, and where, across identities, workloads, and configurations. If your MSSP isn’t using native integrations, they’re relying on secondhand data or generic connectors.
That could lead to slower detection, limited context, and blind spots.
When choosing an MSSP, ask them: How do you collect and normalize telemetry across all my cloud environments?
#2. Unified Threat Visibility
Fragmented visibility is the enemy of speed. If your MSSP relies on separate dashboards or separate teams to investigate incidents in each cloud, detection and response will always lag behind.
A truly multicloud-ready MSSP delivers a single, correlated view. It brings together signals from AWS, Azure, GCP, and on-prem systems into one unified threat graph. That level of integration enables faster triage and real-time risk prioritization.
#3. Cross-Cloud Policy Enforcement
Misaligned policies are the silent killers in multicloud environments. One cloud might block lateral movement. Another could allow it because of legacy rules left untouched.
A capable MSSP helps you design and enforce consistent security policies across platforms. This includes IAM, network segmentation, data access, and encryption. When policies are aligned, attackers don’t find weak links between clouds. This isn’t just operational hygiene. It’s a critical layer of breach prevention.
#4. Automated Compliance Reporting
Regulations don’t care where your data is stored. They only care that it’s protected.
Whether you fall under DPDPA in India, GDPR in Europe, or HIPAA in the US, your MSSP should map controls across your entire cloud stack.
They should also automate reporting wherever possible. Without this, every audit cycle becomes a manual drain, and a growing liability. Ask the MSS provider: Can you generate compliance-ready reports that cover all our environments in a single view?
#5. Cloud-Specific Incident Response Playbooks
An S3 data exfiltration attack behaves very differently from a lateral movement attempt through Azure AD. Each cloud platform has its own signals, response timelines, and escalation triggers during a breach.
That’s why your MSSP must offer platform-specific incident response playbooks. These should be pre-built, thoroughly tested, and ready to deploy under pressure. Cookie-cutter runbooks are a liability. You need response protocols that align with the cloud you are in, the threat you face, and the scale of potential damage.
#6. Cloud Security Posture Management
Misconfigurations remain one of the leading causes of cloud breaches.
A capable multicloud MSSP should offer real-time posture monitoring and proactive remediation. This includes scanning for risky settings, flagging over-permissioned identities, and closing gaps before attackers exploit them.
Advanced providers go further with attack path analysis. That helps security teams understand how small missteps can create large-scale exposure.
Recommended Read: Want to see how leading organizations eliminate misconfigurations and reduce attack surface risk? Explore these 10 essential use cases for attack surface management in this practical eBook from Palo Alto Networks. It highlights real-world scenarios and proactive strategies for cloud security posture management.

Beyond Multicloud: The Real-World Demands on Enterprise MSSPs
For most enterprises, cloud security isn’t just about managing AWS or Azure. It’s about securing everything from legacy on-prem apps to public cloud workloads to modern SaaS integrations. That’s the reality of hybrid cloud.
Now add the growing pressure of compliance. Whether it’s DPDPA, GDPR, HIPAA, or PCI-DSS, the stakes are higher than ever. Security teams are expected to enforce controls across environments. They must maintain audit readiness and respond to threats in real time.
This is where a capable MSSP steps in. But not every provider is equipped to support hybrid and multicloud realities. And fewer make compliance easier instead of adding more complexity.
So before you move forward, make sure your MSSP is not just multicloud-fluent, but enterprise-ready.
Here’s what you should ask before making that call.
CISO Checklist: What to Ask Before You Choose an MSSP?
The multicloud landscape is complicated. Your MSSP should make it easy for you.
Before you commit, ask these seven questions. They reveal how well the provider can protect your enterprise across every layer of your cloud and hybrid environments
#1. Can you provide unified threat visibility across all our cloud environments? For instance, AWS, Azure, GCP, and on-prem environments.
If their answer involves multiple dashboards or manual log stitching, that’s a red flag.
#2. Do you natively ingest telemetry from each cloud provider’s tools, or do you rely on third-party connectors?
Native integrations mean faster detection and richer context. Anything less creates delays and blind spots.
#3. How do you enforce security policies consistently across platforms?
A real MSSP should help you apply and manage IAM, encryption, and network policies in a uniform way. They should not leave gaps between clouds.
#4. What does your incident response process look like for each cloud platform?
If the same playbook is used for different cloud providers, they’re not prepared for the nuances of a real breach.
#5. Do you offer proactive cloud posture management or just reactive alerting?
Misconfigurations cause most cloud breaches. You need continuous scanning, auto-remediation, and attack path insights.
#6. How do you help us stay compliant with regulations like DPDPA, GDPR, or HIPAA?
The right MSSP should automate control mapping, generate audit-ready reports, and simplify governance across all environments.
#7. What SLAs and escalation paths do you offer for multicloud incident response?
Vague or generic answers here mean limited accountability. You want guarantees that reflect your business-critical risk exposure.
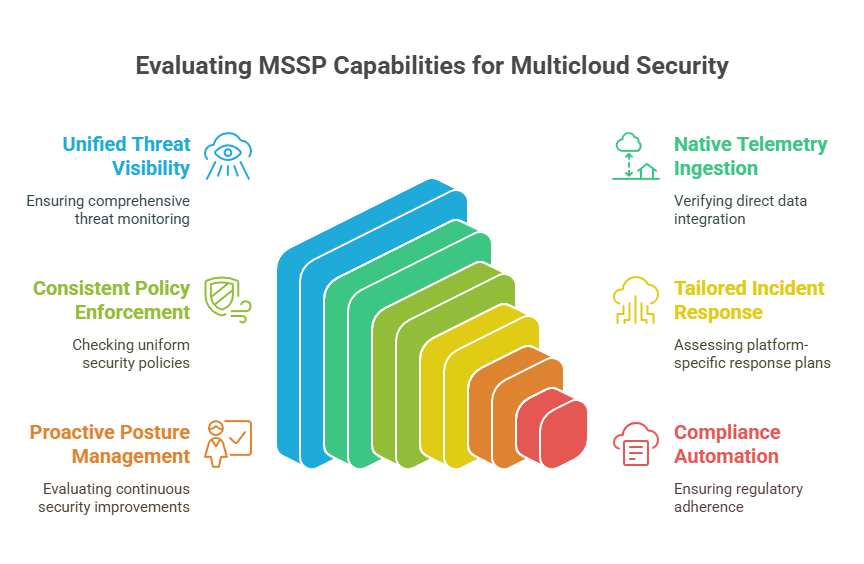
There’s no shortage of MSSPs in the market. But the reality is, very few are equipped to handle the layered complexity of multicloud and hybrid environments. This becomes especially clear when it comes to proactive posture management, cloud native response, and real compliance alignment.
The good news is that Datacipher is one of the few providers that checks every box. And in many cases, goes even further.
Let us show you how.
Why Datacipher is the MSSP built for Multicloud and Hybrid Complexity?
Datacipher isn’t just another MSSP. We specialize in securing complex, fragmented environments where cloud, on-prem, and legacy systems intersect. Our managed security services are engineered to give enterprises full-spectrum visibility, proactive control, and real-time protection. Irrespective of the number of platforms you run.
Here’s how we help you stay ahead:
#1. Comprehensive Security across Diverse Cloud and On-Premises Environments
Datacipher delivers integrated security solutions that span a wide array of cloud platforms—including public, private, and hybrid clouds—as well as on-premises infrastructures.
By leveraging native integrations and centralized management, we provide a unified view of your entire threat landscape. This eliminates silos and ensures that no threat goes undetected, regardless of where it originates.
#2. Consistent Policy Enforcement across Environments
Our approach ensures that security policies are uniformly applied across all platforms. This consistency reduces the risk of misconfigurations and ensures that your security posture remains robust, even as your infrastructure evolves.
#3. Automated Compliance Reporting
We automate the mapping of controls and generate audit-ready reports that reduce compliance overhead for your teams. This proactive approach ensures that you stay ahead of regulatory requirements without the manual burden.
#4. Tailored Incident Response Playbooks
Our cloud-specific incident response plans ensure faster containment, lower risk, and smoother recovery, no matter where the threat appears. We understand the nuances of each platform and tailor our response accordingly.
#5. Proactive Cloud Posture Management
We provide continuous scanning, auto-remediation, and attack path insights to prevent vulnerabilities before they can be exploited.
#6. 24/7 Managed Detection and Response
Our Security Operations Center operates around the clock, providing real-time monitoring, threat hunting, and rapid response to incidents. This ensures that threats are identified and mitigated promptly.
#7. Expertise in Hybrid Cloud Environments
We have extensive experience in managing and securing hybrid cloud environments. We can ensure seamless integration and consistent security across both cloud and on-premises systems.
Earlier this year, a regional telecom provider approached us with workloads spread across Azure and GCP, alongside legacy billing systems running on-premises. Their previous MSSP struggled with siloed log handling, which led to missed threats.
We implemented a unified threat graph, automated posture alerts, and compliance-ready reporting, reducing their incident response time by over 40%.
Are you still stitching together security across cloud providers or frustrated with a hands-off MSSP? Our experts can help unify your environments and get your security posture back on track. Schedule a consultation with our multicloud experts here.
Frequently Asked Questions
#1. What’s the difference between a traditional MSSP and a multicloud-capable MSSP?
A traditional MSSP may monitor firewalls and forward alerts. A multicloud-capable MSSP integrates directly with native cloud tools, correlates cross-platform data, and enforces unified policies. These MSSPs don’t just detect threats but understands them in the context of complex cloud environments.
#2. Can an MSSP really help with compliance, or do I still need separate tools?
Yes. A good MSSP automates control mapping, generates audit-ready reports, and helps you stay compliant with regulations like DPDPA, GDPR, and HIPAA. With a good MSSP, you won’t need a patchwork of compliance tools. But a partner who covers security and governance together.
#3. What if we already have in-house SecOps? Do we still need an MSSP?
Absolutely. MSSPs complement internal teams with 24/7 monitoring, advanced threat intelligence, and multicloud expertise. They reduce alert fatigue, accelerate incident response, and let your team focus on strategic tasks. If you want a broader view of when outsourcing MSS makes sense or doesn’t, this guide breaks it all down. It talks about seven key outsourcing scenarios and 3 where keeping it in-house is the smarter move.
#4. How fast should an MSSP detect and respond to incidents in a multicloud setup?
Leading MSSPs should detect threats within minutes and initiate response actions based on pre-approved playbooks. Look for providers that offer SLA-backed response times, real-time correlation, and cloud-specific escalation paths.
#5. How does an MSSP handle cloud identity misconfigurations or over-permissioned accounts?
A multicloud MSSP continuously scans for identity risks, flags over-permissioned roles, and recommends least-privilege adjustments. Advanced providers also integrate with IAM tools to auto-remediate misconfigurations in real time.





