You upgraded to a Next-Generation Firewall expecting better security, deeper network visibility, and an easier time managing threats. But now, instead of peace of mind, you’re facing frustration.
The network isn’t as fast as you thought it would be. Your team keeps running into false positives that disrupt operations. Every new security update requires reconfigurations that take hours, and you’re still not sure if you’re fully protected.
You’re not alone. Most security professionals struggle with firewall complexity, and misconfigurations remain one of the leading causes of breaches.
NGFWs solve many of the traditional firewalls’ blind spots, but they introduce their own set of challenges. Ones that most businesses aren’t fully prepared for.
So, what’s going wrong? And more importantly, how do you fix it?
In this article, we break down five of the biggest NGFW challenges companies face and offer practical solutions to overcome them.
Source: Datacipher
Let’s dive into it.
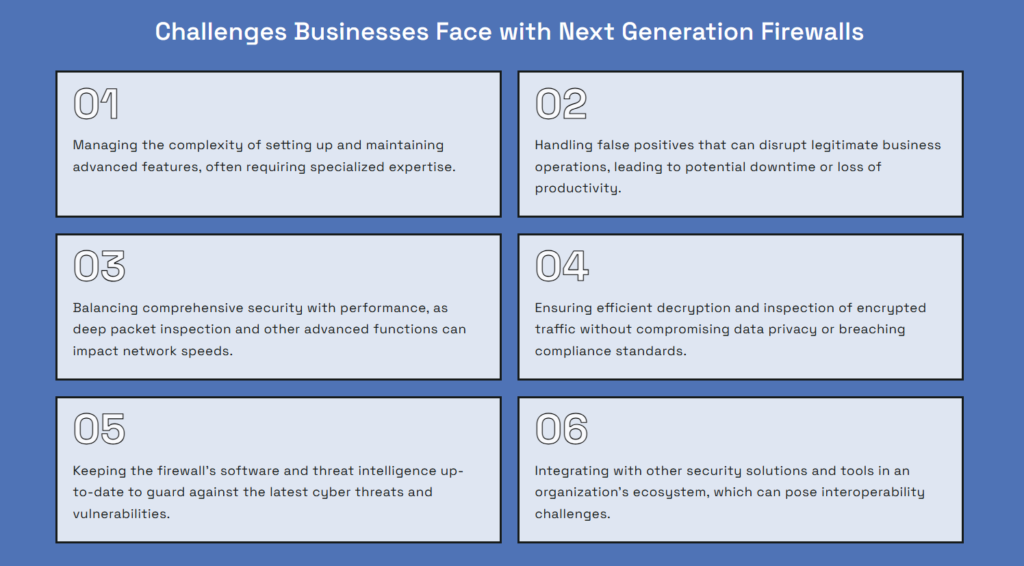
Challenge #1: Complexity of Setup & Configuration
Next-Generation Firewalls (NGFWs) are powerful, but setting them up correctly is where most businesses struggle. Unlike traditional firewalls, NGFWs offer deep packet inspection, intrusion prevention, identity-based policies, and SSL decryption, all of which need precise tuning. One wrong rule, and you’re either blocking legitimate traffic or leaving security gaps wide open.
Common pitfalls include:
#1. Overly strict policies that block legitimate traffic and slow down productivity.
#2. Loosely defined rules that create blind spots for cyber threats.
#3. Poor SSL inspection setup that slows down networks or violates compliance.
#4. Inconsistent policies across cloud, branch offices, and remote users.
To avoid these issues, organizations should:
a) Define a least-privilege policy – block all by default, allow only necessary traffic.
b) Use identity-based access controls instead of outdated IP-based rules.
c) Enable SSL decryption selectively, inspecting high-risk categories while excluding sensitive data.
d) Schedule policy reviews every six months to remove outdated rules and tighten security.
For simple setups, IT teams can handle this in-house. But in multi-site, high-traffic environments, we recommend availing the services of an expert to ensure consistent configurations, real-time threat intelligence, and seamless performance tuning.
Challenge #2: Performance Bottlenecks & Network Slowdowns
A Next-Generation Firewall is supposed to protect your network, not slow it down. But many businesses experience latency issues, sluggish applications, and bandwidth bottlenecks after deploying one.
Unlike traditional firewalls, NGFWs perform deep packet inspection, SSL decryption, intrusion prevention, and content filtering in real-time. If not properly optimized, these security processes can overwhelm network resources, causing frustrating slowdowns.
To maintain both security and speed, businesses should:
a) Use application-aware rules to inspect only necessary traffic instead of scanning everything.
b) Optimize SSL decryption by excluding low-risk traffic like trusted internal communications.
c) Implement Quality of Service policies to prioritize critical business applications.
d) Ensure hardware scalability – NGFW resources must match growing network demands.
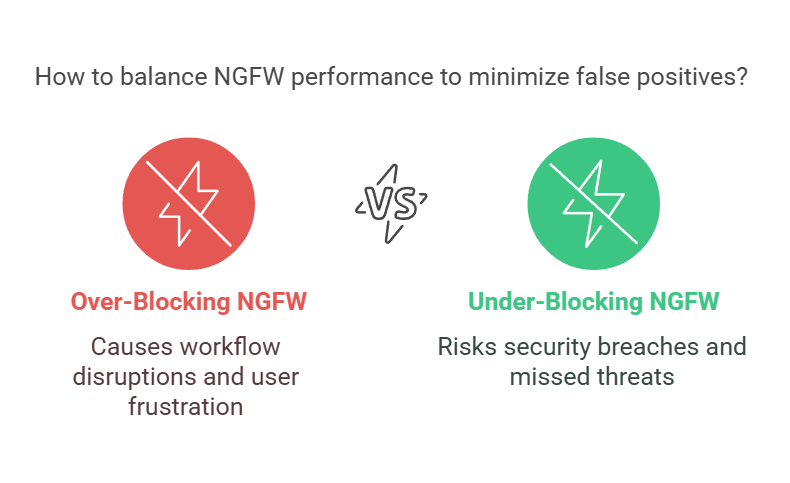
Challenge #3: Managing False Positives without Compromising Security
A firewall that blocks too much is just as bad as one that doesn’t block enough. One of the most frustrating issues with NGFWs is false positives – legitimate traffic mistakenly flagged as a threat.
Professionals end up dealing with disrupted workflows, frustrated users, and wasted time manually approving safe connections.
Why does this happen? NGFWs rely on intrusion prevention systems(IPS), behavior-based detection, and automated threat intelligence. While these tools are great at catching advanced threats, they also have a tendency to misclassify normal activity. Some common causes include:
#1. Overly aggressive IPS rules that treat routine traffic as suspicious.
#2. Outdated or overly broad threat intelligence feeds that lack refinement.
#3. Application misidentification – certain tools get flagged as high-risk incorrectly.
#4. Unoptimized firewall policies that don’t align with business operations.
Fixing this requires fine-tuning security rules rather than disabling protections altogether. This can be done by:
a) Adjusting IPS thresholds to minimize excessive blocking while maintaining security.
b) Regularly updating and refining threat intelligence feeds to reduce unnecessary alerts.
c) Using allow-lists for trusted applications to prevent constant misclassification.
d) Continuously monitoring firewall logs to identify patterns and adjusting rules accordingly.
For businesses with high-security environments or complex infrastructures, manual tuning may not be enough. Advanced machine learning-driven detection, SIEM integration, and managed security services can help reduce false positives without weakening security.
When too many alerts overwhelm internal teams, a security provider can fine-tune NGFW rules, adjust IPS thresholds, and refine threat intelligence feeds to minimize false positives without weakening security.
Their expertise can ensure that legitimate traffic flows smoothly while real threats get flagged without constant manual intervention. This level of precision is difficult to maintain in-house, making expert intervention critical for businesses handling high volumes of alerts. Looking for expert intervention? This should help.
Challenge #4: Keeping NGFWs updated with the Latest Threat Intelligence
A firewall is only as strong as its last update. Cyber threats evolve daily, and an outdated next-generation firewall can quickly become a security liability. Without continuous updates, businesses risk missing zero-day attacks, malware hidden in encrypted traffic, and phishing tactics designed to bypass traditional defenses.
Some common reasons NGFWs fall behind on updates include:
#1. Lack of automated threat intelligence integration, leading to delayed responses.
#2. Failure to regularly update security signatures and IPS rules.
#3. Inconsistent patch management, leaving vulnerabilities unaddressed.
#4. Overreliance on default settings, missing advanced configurations that improve threat detection.
To stay ahead, businesses should:
a) Enable real-time threat intelligence feeds to detect and block emerging threats.
b) Regularly update IPS rules and security signatures to cover new attack vectors.
c) Automate patch management to ensure firmware and policies stay current.
d) Conduct security audits to fine-tune detection settings and eliminate blind spots.
For businesses with complex security environments or limited in-house expertise, maintaining continuous threat intelligence updates can be overwhelming. In such cases, expert-managed services can ensure firewalls remain fully optimized against the latest threats.
Want to simplify NGFW updates with automation? Our eBook, “A Practical Guide to Deploying SecOps Automation,” breaks down how businesses can integrate automation into their security operations, enhancing firewall efficiency and real-time threat response. Download below.

Challenge #5: Integration Challenges with Existing Security Infrastructure
Firewalls don’t work in isolation. It needs to work seamlessly with endpoint security, SIEM systems, cloud security solutions, and identity management platforms.
But many businesses find that their NGFWs doesn’t integrate smoothly with their existing security stack, leading to visibility gaps, inefficiencies, and even security blind spots.
Some of the most common integration challenges include:
#1. Compatibility issues between NGFWs and legacy security tools.
#2. Fragmented security policies across on-prem, cloud, and hybrid environments.
#3. Delayed or incomplete threat intelligence sharing between security platforms.
#4. Operational inefficiencies due to siloed security management interfaces.
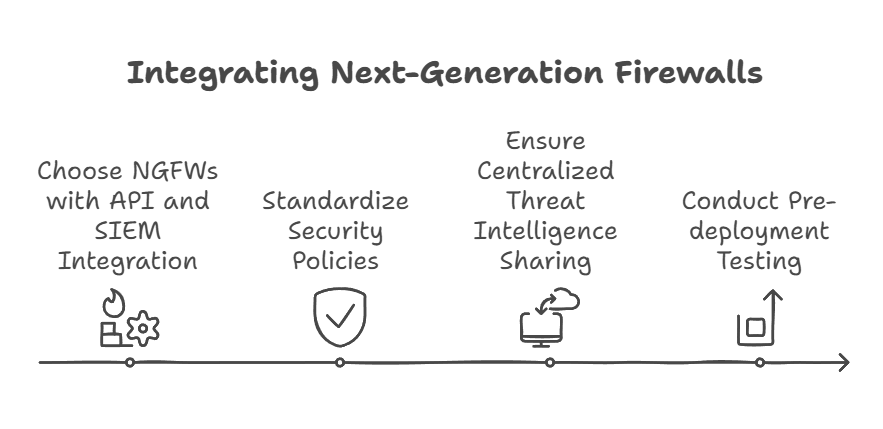
To ensure smooth integration, businesses should:
a) Choose NGFWs with strong API and SIEM integration capabilities.
b) Standardize security policies across all environments for consistent enforcement.
c) Ensure centralized threat intelligence sharing to avoid detection delays.
d) Conduct pre-deployment testing to identify and resolve integration conflicts early.
For businesses with multiple security tools and hybrid environments, ensuring seamless NGFW integration is crucial to maintaining a unified defense strategy. Without proper integration, even the best firewall can leave gaps that attackers exploit.
Turning NGFW Challenges into Strengths
Next-Generation Firewalls are a crucial line of defense, but as we’ve seen, they come with their own set of challenges.
Misconfigurations can leave security gaps. Poor performance tuning can slow down operations. False positives can overwhelm IT teams. Outdated policies can let emerging threats slip through. And without proper integration, even the most advanced firewall can become a blind spot in your security ecosystem.
The key isn’t just deploying an NGFW. It’s fine-tuning it for your business needs, continuously updating threat intelligence, and ensuring seamless performance. When done right, a next-generation firewall becomes a true security asset, defending against evolving cyber threats without disrupting business operations.
Solve Next-Generation Firewall Problems with Datacipher Solutions
A firewall should be a strength, not a struggle. Businesses need next-generation protection without performance trade-offs, security gaps, or operational headaches. This is where Datacipher’s NGFW solutions make the difference.
Source: Datacipher
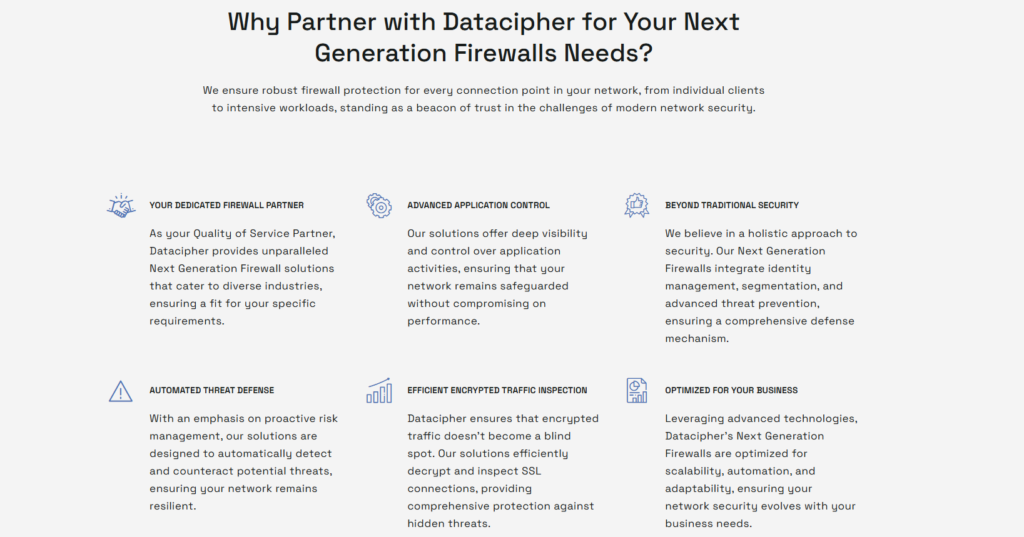
Datacipher ensures your firewalls are optimized for real-world security challenges. Here’s how Datacipher helps businesses take control of their network security:
#1. Seamless configuration & policy management – Expert-led setup that eliminates misconfigurations and ensures security policies align with business needs.
#2. Advanced threat prevention – Continuous monitoring, real-time intelligence feeds, and proactive risk management to guard against evolving cyber threats.
#3. Performance optimization – Deep packet inspection, SSL decryption, and security policies fine-tuned for maximum efficiency without slowing down operations.
#4. False positive reduction – AI-driven analysis and customized IPS tuning to prevent unnecessary alerts while keeping real threats in focus.
#5. Up-to-date security intelligence – Automated updates, regular firewall policy reviews, and seamless patch management to stay ahead of emerging threats.
#6. Enterprise-grade integration – NGFWs configured to work smoothly with SIEMs, endpoint security, cloud environments, and identity management platforms.
With Datacipher, businesses get more than just a firewall – they get a fully optimized security strategy that ensures robust protection without disrupting daily operations.
Take the next step in securing your network. Connect with Datacipher today and ensure your NGFW is working for you, not against you.
Frequently Asked Questions
#1. What is a Next-Generation Firewall?
A Next-Generation Firewall (NGFW) is an advanced security solution that goes beyond traditional firewalls by offering deep packet inspection, application control, intrusion prevention, and identity-based policies. It protects networks from modern cyber threats by combining real-time threat intelligence with granular traffic visibility and enforcement.
#2. How does UTM differ from Next-Generation Firewalls?
A Unified Threat Management (UTM) device is an all-in-one security solution that bundles firewall, antivirus, VPN, web filtering, and intrusion prevention into a single appliance – ideal for small to mid-sized businesses. In contrast, an NGFW focuses on advanced traffic analysis, application-layer security, and deep threat prevention, making it more suitable for enterprises requiring high-performance security.
#3. How often should Next-Generation Firewalls be updated?
NGFWs should be updated timely to stay ahead of evolving threats. Best practices include:
- Daily or real-time updates for threat intelligence feeds.
- Monthly or quarterly firmware and IPS rule updates to patch vulnerabilities.
- Biannual policy audits to remove outdated rules and optimize security.
- Immediate emergency updates when critical exploits emerge.





