Every second, eleven new cyber threats emerge somewhere in India. According to the India Cyber Threat Report 2025, over 369 million security incidents were detected across 8.44 million endpoints in 2024
But volume is not the only issue. Indian enterprises are under siege not just from malware but from misalignment, integration debt, and invisible weak spots created by years of security tool sprawl.
This article is for the CISO who sees the silos, the head of infra who’s fighting vendor sprawl, and the security architect who’s tired of band-aid integrations.
We will unpack the eight most painful system integration challenges faced by Indian enterprises. These are the bottlenecks that slow down detection, delay response, and overwhelm security operations.
We will also show you what the fix looks like. This is not another rip-and-replace strategy. It is an engineer-led approach to integration, built for India’s infrastructure, organizational structures, and security reality.
If you are tired of vendors who oversell and underdeliver, this one is for you.
System Integration Challenge 1: The Frankenstein Problem
Indian enterprises today operate with an uneven stack. They have firewalls from one vendor, cloud workloads on another platform, and legacy endpoints patched onto modern apps. According to the India Cyber Threat Report 2025, 702 threats were detected every minute. But many of these threats are detected in isolation, because systems don’t talk to each other.
This challenge is common in sectors like BFSI and telecom, where tools are acquired reactively, based on compliance checklists or procurement cycles. There’s no unified architecture. Each team manages its own stack. Security alerts stay in silos. Policies overlap or contradict each other. The result is noise, missed detections, and slower incident response.

Solution: Start With Architectural Visibility
Fixing this starts with a clear understanding of your current architecture. Begin by mapping out the systems already in place: what tools are active, where security policies are being applied, and how telemetry is being collected.
You do not need to replace everything to make progress. Even simple steps—like aligning log formats, setting up shared alert routing, or drafting a unified response playbook—can help teams move from silos to shared context.
Working with a system integrator can accelerate this process. They often bring proven templates, policy alignment frameworks, and a top-down view of how security and infrastructure should fit together. But even without one, teams can begin solving this by thinking system-first, not tool-first.
System Integration Challenge 2: Legacy Systems That Refuse to Die
Across sectors like insurance, telecom, and logistics, core business functions still run on systems built more than a decade ago. Many of these are custom applications hosted on physical servers, written in outdated languages, with little to no documentation. They handle critical workflows, and no one wants to risk disrupting them.
When it is time to modernize or integrate new security layers, these systems become bottlenecks. They cannot support APIs. They do not log in standard formats. And any update feels like it could break something downstream. So they stay untouched, while the rest of the stack moves forward.
Solution: Extend Without Disrupting
You can start by identifying how these systems interact with others. Look at data flows, access patterns, and security gaps. In many cases, lightweight adapters, proxies, or brokers can make legacy systems more visible without needing to rebuild them. This enables teams to safely extend security controls and monitoring tools to legacy environments.
System integrators, such as Datacipher, are especially effective in this regard. We use modular abstraction frameworks, virtual network overlays, and role-based access enforcement to secure legacy systems, without forcing a full-scale migration. But even internally, teams can begin by isolating legacy workloads, documenting dependencies, and exposing only what is necessary.
System Integration Challenge 3: Security is an Afterthought, Until It’s a Disaster
In many Indian enterprises, system integration projects prioritize performance and uptime, often sidelining security considerations. This oversight can lead to vulnerabilities, especially in rapidly expanding digital infrastructures.
The India Cyber Threat Report 2025 highlights a significant rise in cloud-based detections, accounting for 62% of all detections, reflecting the broader digital transformation across Indian businesses.
Similarly, the Karnataka Cyber Threat Report 2025 underscores the growing threat posed by API vulnerabilities, noting that attackers increasingly exploit misconfigured endpoints to access sensitive data, making API security a critical focus area for telecom providers.
These findings illustrate that security misconfigurations and exposed interfaces are not just theoretical risks but active threats exploited by malicious actors.
Solution: Integrate Security from Day Zero
To mitigate these risks, it’s essential to embed security considerations from the outset of any integration project. This involves aligning on identity controls, segmenting network traffic, and validating every exposed service or API.
By involving security teams at the architecture stage, organizations can ensure that integration success encompasses both performance and robust security measures.
System Integration Challenge 4: Real-Time? Forget It. Batch Jobs Rule the Day
In many Indian enterprises, data still moves in nightly syncs. Security logs, authentication events, and user activity often flow in 12-to-24-hour windows. This delay turns routine visibility into post-incident forensics. By the time a threat is spotted, it is already too late to contain.
This is not just a legacy issue; it is a structural one. According to the India Cyber Threat Report 2025, cloud workloads now generate over 62% of all detections, requiring more responsive telemetry and incident resolution timelines. But most Indian setups still rely on batch pipelines between cloud, on-prem, and analytics tools.
This gap is particularly detrimental in sectors such as fintech, logistics, and retail, where real-time context is crucial for preventing fraud, monitoring service-level agreements (SLAs), and responding to threats.
Solution: Move from Sync to Stream
The fix does not require a full platform overhaul. Enterprises can begin by identifying where real-time flow matters—security, identity, and fraud—and pilot event-driven flows in those areas. Even simple additions, like webhook-driven alerts or direct cloud-to-SIEM feeds, can reduce detection time drastically.
Teams should separate “hot data” from historical logs, so time-sensitive decisions are powered by live inputs, not yesterday’s summaries.
System Integration Challenge 5: No One Owns the Problem
In many Indian enterprises, when something breaks, it is rarely clear who is responsible. Is it a misconfigured firewall? A broken API? A sync delay from a third-party tool? Every team owns a piece, but no one owns the full picture.
This problem is not about blame. It is about design. Security, infrastructure, and application teams all operate on different tools, alerts, and escalation workflows. Without shared visibility, even small incidents become extended investigations.
The India Cyber Threat Report 2025 highlights that while incident response frameworks are improving, many enterprises still lack cross-functional coordination and centralized observability. During real-world attacks, this slows down root cause discovery and impacts response timelines.
To build a more unified, resilient security operations capability, many enterprises are undergoing SOC transformations. If you’re exploring how to modernize your SOC to improve visibility, reduce burnout, and accelerate threat response, we recommend reading the eBook Five Essential Steps to SOC Transformation. It offers practical frameworks to help Indian enterprises align technology, people, and processes for a future-ready SOC.

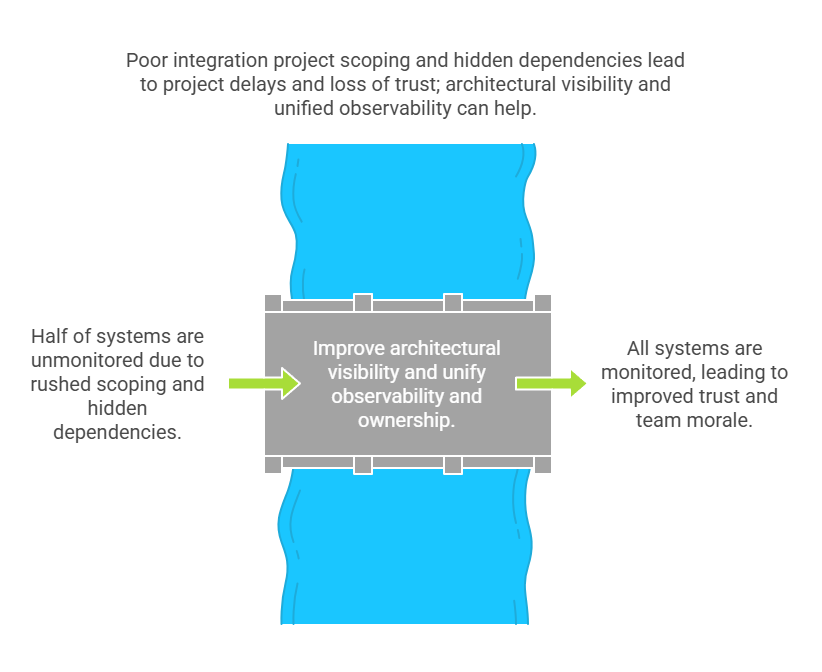
Solution: Unify Observability and Ownership
Solving this starts with a shared source of truth. Connect logs, alerts, and metrics across systems. Use a centralized SIEM or federated dashboarding to ensure all teams can see the same data.
Even without new tools, enterprises can align by building joint runbooks, mapping system dependencies, and reviewing past incidents together. That is how you move from confusion to accountability.
System Integration Challenge 6: Locked Into a Platform You Can’t Easily Leave
Enterprises often invest heavily in a cloud or infrastructure platform only to realize later that flexibility was never part of the deal. Licensing terms, proprietary APIs, and vendor-specific workflows make it easy to get started, but difficult to pivot or scale on your terms.
This issue is particularly visible in industries with long procurement cycles or complex compliance requirements. A decision made five years ago has become a bottleneck today. Teams want to migrate workloads, redesign security posture, or move to multi-cloud, but the system fights back.
Integration becomes harder. Policy control becomes fragmented. And the cost of change grows with every new dependency.
Solution: Design for Flexibility, Not Just Function
It is not about avoiding vendors. It is about avoiding architectural traps. Start by identifying where you’re most tightly coupled. Are your policies locked into a specific cloud dashboard? Are your integrations dependent on proprietary plugins?
Even without migrating, you can start decoupling parts of your system. You can begin by moving workloads into containers, separating identity from infrastructure, and keeping data flows portable.
Datacipher helps enterprises design around this reality. Our integration frameworks prioritize modularity and policy portability, giving you room to evolve, even if your platforms change later. It is about future-proofing, not just getting the job done today.
System Integration Challenge 7: Resistance from Within
New systems do not fail because the architecture is flawed. They fail because the people expected to run them do not trust them.
In many Indian enterprises—especially in sectors like BFSI, manufacturing, and logistics—teams have worked with the same systems for years. So when a new tool, integration, or workflow is introduced, it is natural for teams to question how it will affect their day-to-day operations.
Sometimes that hesitation is technical: “This might disrupt something that works.” Other times, it is about comfort and continuity: “Will this change how we’re measured? Who will support it?”
This kind of quiet resistance does not show up on dashboards, but it often slows down adoption. Even with well-designed integrations, systems go unused or underutilized because the rollout did not bring people along.
The India Cyber Threat Report 2025 notes that 57% of organizations lack basic cyber hygiene, and 73% remain unaware of ongoing breaches. These gaps often stem not from a lack of tools, but from inconsistent use and low engagement.
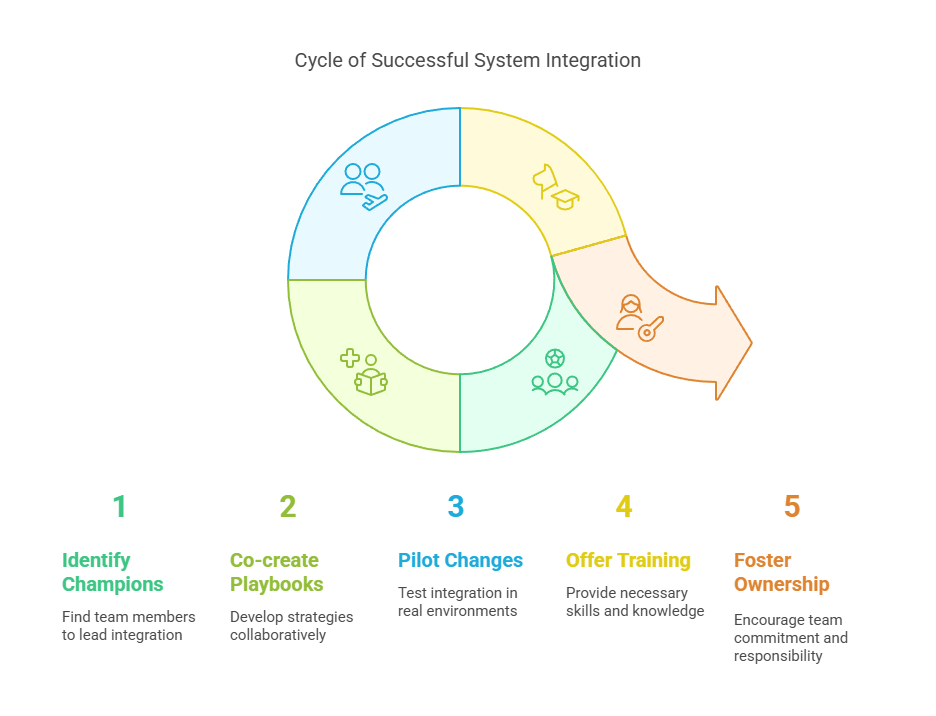
Solution: Integrate Mindsets Before Systems
Do not launch integrations from the top down. Start with champions inside your teams—engineers, admins, analysts—who can shape the rollout from within. Co-create playbooks. Pilot changes in live environments with real users. Offer training, not just deployment guides.
Security and integration are only as strong as the people behind them. If your ops and infra teams do not believe in the system, they will bypass it. If they co-build it, they will own it.
At Datacipher, we approach integration as part technical, part cultural. We embed with teams during pilots, facilitate workshops that uncover hidden friction, and help security, infra, and ops align before the tooling even ships. Because successful integration is not about control, but about trust.
System Integration Challenge 8: Integration Projects That Spiral Out of Scope, Budget, and Time
In theory, the plan was solid: new IAM rollout, unified logging, zero-trust enforcement. All done in six weeks. However, six months later, the dashboard still shows that half of the systems are unmonitored.
In reality, integration projects inside Indian enterprises often get stuck. Why? Because scoping is rushed. Dependencies are hidden. Specs change midstream. And no one wants to be the person who says, “We did not account for that.”
This challenge cuts across sectors. In telecom, dependencies span hybrid clouds. In BFSI, the security review process can take weeks. In government rollouts, vendor onboarding can take a quarter on its own.
Delays hurt more than timelines. They break trust. Teams lose morale. Leadership starts questioning the value of the integration. The deeper issue is a lack of discipline in execution. Big-ticket transformation projects collapse not because of bad intent. They collapse because complexity meets poor visibility.
Solution: Scope Realistically. Build Transparently. Adapt Fast.
The first step is scoping, which includes reality, not just aspirations. That means surfacing shadow dependencies, building in review cycles, and defining “done” in a way that all teams understand.
Once live, integration projects should run on feedback loops. Not waterfall silence. Weekly demos. Early validation. Transparent status dashboards.
To be honest, when integration projects start slipping, it is often because no one is accountable for making the entire system work together.
That is where a skilled system integrator makes a difference.
Instead of treating networking, security, and infrastructure as separate tracks, system integrators work across layers. They anticipate roadblocks, align stakeholders, and engineer the system as a whole. And when done right, that kind of alignment does not just prevent overruns. It reduces the total cost of execution.
Want to understand when it makes sense to bring one in? See our companion guide: In-House vs. Outsourced System Integration: What’s Right for You?
How Datacipher Tackles System Integration Challenges At Scale?
The challenges we covered in this article are just the visible symptoms.
Behind them are dozens of underlying problems: misaligned control planes, disconnected policy layers, reactive deployments, compliance overhead, and skill gaps.
At Datacipher, we don’t just solve the visible pain points. We address the entire system.
With expertise spanning security, networking, automation, and infrastructure, we help enterprises regain control of complex, disjointed environments. The result is a fully integrated, secure architecture built for real-world performance.
Here’s how:
- Full-Stack Visibility and Control: From cloud to endpoint to network edge, we map your environment and create integration blueprints that bring order to fragmented systems.
- Modular, Vendor-Neutral Architecture: Our integrations are built to flex. No lock-ins, no one-size-fits-all templates. We offer clean, scalable engineering that fits your environment.
- Deployment-Led Execution: We don’t stop at design. Certified engineers lead on-ground deployments across India and APAC, closing the gap between planning and production.
- Beyond the Eight: Whether it is compliance-driven segmentation, automation frameworks, remote access design, or post-deployment skill training, our team handles it best.
Whether you are dealing with scattered tools, legacy constraints, or stalled rollouts, we can help you bring it all together.
For instance, when Mahindra & Mahindra faced persistent Wi-Fi and network performance issues, Datacipher deployed Juniper Mist Wi-Fi solutions with AI-driven automation and analytics. The result: an 80% reduction in connectivity issues, faster average throughput, and a significant drop in user-reported problems. Watch the difference here.
To take the next step toward effectively solving your system integration challenges, contact our experts today.
Frequently Asked Questions around System Integration Challenges and Solutions
#1. What are the biggest risks of poor system integration in enterprises?
Poor system integration leads to fragmented visibility, slower incident response, inconsistent security enforcement, and spiraling operational costs. It also creates hidden vulnerabilities that attackers can exploit. This makes scaling infrastructure much harder when growth accelerates.
#2. How do I know if my organization needs a system integrator?
If you are juggling disconnected tools, struggling with real-time visibility, facing project delays, or simply unsure where your security boundaries end, it is time to consider a system integrator. Early intervention often saves far more cost and complexity than late-stage firefighting.
#3. How long does a typical system integration project take?
It varies based on scope. Small integrations can take a few weeks. Enterprise-grade multi-stack projects may run several months. What matters most is tight scoping, real-time feedback loops, and having the right technical partner who aligns milestones to your infrastructure realities.
#4. How does system integration improve cybersecurity posture?
Good integration eliminates blind spots. It connects endpoints, networks, and cloud telemetry into unified visibility. It enforces security policies consistently across platforms. And it strengthens threat detection, identity management, and incident response by removing gaps that attackers love to exploit.
#5. Is system integration a one-time project or an ongoing process?
True integration is never static. As environments evolve—cloud expansions, new compliance requirements, infrastructure upgrades—your integrations must adapt too. System integration is an ongoing process of aligning technology, security, and operations to where your business is heading next.
#6. What should I look for when choosing a system integration partner?
The right integration partner brings deep technical skill across networking, cloud, and security and approaches projects with an engineering-first mindset. Proven experience, real-world case studies, and client references matter far more than slide decks. You should choose a partner who builds systems for how you work, not just how they sell.





