Choosing an EDR solution isn’t hard. Choosing the right one is. If you’re a CIO or CSO today, you’re not asking whether EDR is important. You already know endpoints are the most targeted layer of your environment.
The real question is: Which EDR fits your environment, your team, and your threat model?
Do you need cross-platform visibility? Deep forensics? Seamless cloud integration?
Every EDR vendor claims AI, automation, and real-time protection. But what actually separates them in practice?
At Datacipher, we’ve helped large enterprises across telecom, BFSI, healthcare, and SaaS select, deploy, and operationalize Endpoint Security platforms that fit.
In this guide, we break down 7 leading EDR tools from Cortex XDR to CrowdStrike Falcon not just by features, but by real-world fit. We will cover:
#1 What use cases they shine in
#2 What integration paths are smoothest
#3 What kind of security team they’re best suited for
Whether you’re modernizing your endpoint defense, replacing a legacy AV, or rolling out XDR across your stack, this article will help you make a decision you won’t regret.
Why Enterprises Need Advanced EDR Solutions?
Cyberattacks aren’t slowing down. Endpoints are now the favorite targets for attackers because they’re everywhere, often unmonitored, and easy to exploit.
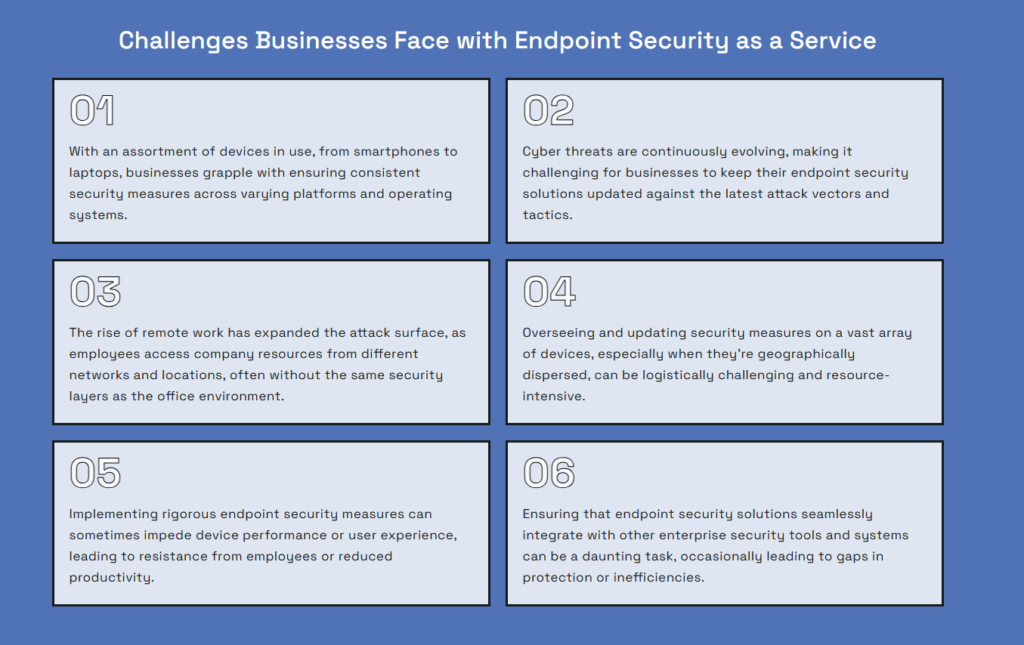
For IT and security leaders, the challenges have grown multifold. They have to deal with:
- Ransomware outbreaks that lock systems and halt business operations.
- Zero-day exploits that bypass traditional antivirus solutions.
- Alert fatigue caused by floods of false positives.
- Visibility gaps across endpoints, networks, and the cloud.
And traditional antivirus tools simply aren’t enough.
EDR steps in with:
- Real-time threat detection and automated response.
- Deep visibility to investigate incidents quickly and accurately.
- Proactive defense to stop threats before they spread.
The result? Faster protection, fewer disruptions, and more time for your team to focus on strategic goals.
Key Features to Look for in an EDR Solution
When evaluating EDR solutions, focus on the features that solve your team’s biggest challenges.
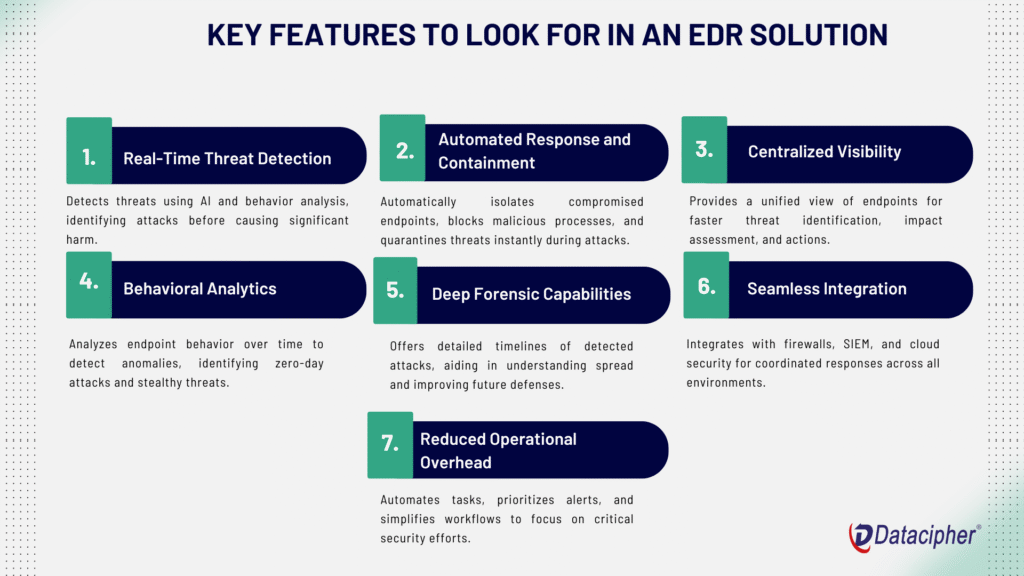
#1. Real-Time Threat Detection
The right EDR solution doesn’t just look for known malware signatures; it uses AI and behavioral analytics to detect threats based on unusual patterns.
For instance, it can identify fileless attacks, ransomware attempts, or suspicious processes before they cause harm.
#2. Automated Response and Containment
Manually isolating infected endpoints or stopping malicious processes wastes critical time during an attack.
Advanced EDR tools automate these responses, shutting down compromised endpoints, blocking processes, or quarantining files instantly.
#3. Centralized Visibility
Modern EDR platforms offer a single-pane-of-glass view of all endpoints—on-premises or remote.
This unified view helps security teams quickly identify threats, assess their impact, and take action.
#4. Behavioral Analytics
EDR tools use machine learning to analyze endpoint activity over time, flagging anything that deviates from normal behavior.
This is critical for identifying zero-day attacks or threats that don’t rely on traditional malware files.
#5. Deep Forensic Capabilities
Once a threat is detected, forensic analysis becomes vital. Good EDR solutions provide detailed attack timelines, showing where the attack started, how it spread, and what systems were impacted, so that IT teams can strengthen defenses.
#6. Seamless Integration
EDR doesn’t work in isolation. The best solutions integrate with other tools like firewalls, SIEM platforms, and cloud security to deliver complete visibility and coordinated responses across the environment.
#7. Reduced Operational Overhead
By automating manual tasks, prioritizing alerts, and streamlining workflows, a robust EDR solution enables your team to focus on high-value security initiatives.
Editor’s Note: Want the expert take before you dive into the details? In this video, we walk through the top EDR solutions for 2025, explain what sets them apart, and help you decide which one actually fits your environment. If you’re short on time, start here.
Now, let’s look at the Top 7 EDR solutions to protect your business in 2025.
1. Palo Alto Networks Cortex XDR
Cortex XDR is Palo Alto Networks’ flagship detection and response platform and the first in the industry to unify EDR, NDR, and cloud telemetry into a single XDR engine. It was built for large-scale environments that need speed, scale, and centralized visibility across attack surfaces.
What makes it different from traditional EDR? It doesn’t just monitor endpoints; it stitches together behavioral data from firewalls, cloud workloads, identity events, and network traffic for a complete threat picture.

Source – Palo Alto
Benefits
Cross-Surface Correlation: Cortex XDR automatically correlates alerts from endpoints, firewalls (like Palo Alto NGFW), cloud workloads (via Prisma), and identity providers. This reduces alert fatigue and shortens dwell time.
AI-Powered Detection: Machine learning models trained on global threat intel from WildFire, Palo Alto’s threat analysis engine, allow it to detect both malware and “living off the land” techniques that evade AVs.
Precision Response Playbooks: You can trigger automatic responses, like quarantining endpoints or disabling user accounts, based on custom conditions. It’s also tightly integrated with Cortex XSOAR for full workflow automation.
Root Cause Analysis: Every alert includes a visual timeline showing the attack path, initial exploit, lateral movement, and affected assets, which is critical for forensic teams.
Behavior-Based Analytics: Instead of relying on IOCs alone, Cortex XDR uses behavioral baselining to flag anomalies across multiple data sources—not just endpoints.
Suitable For
Large enterprises or SOCs looking for XDR-grade detection across endpoints, networks, and cloud. Especially effective in environments with existing Palo Alto infrastructure or high compliance needs (e.g., finance, healthcare, telecom).
Pricing
Custom enterprise pricing. Generally sold via Cortex bundles or through MSSP partners like Datacipher.
2. CrowdStrike Falcon
CrowdStrike Falcon is a cloud-native endpoint protection platform that combines EDR, next-gen antivirus (NGAV), and threat intelligence into one lightweight agent. Designed for speed and scale, Falcon is widely adopted by enterprises seeking rapid deployment and global visibility across distributed environments.
Source – Crowdstrike
Benefits
Lightweight Agent: Uses minimal system resources, making it ideal for performance-sensitive environments like financial services or healthcare.
Behavioral-Based Detection: Leverages machine learning and IOA (Indicators of Attack) to detect fileless, zero-day, and hands-on-keyboard threats.
Real-Time Threat Intelligence: Integrated with Falcon X to enrich alerts with adversary context, TTPs, and attribution.
Instant Response: Supports real-time endpoint isolation, remote shell access, and script execution for rapid containment.
Scalability: Proven to support hundreds of thousands of endpoints without infrastructure burden, thanks to its SaaS-based architecture.
Suitable For
Enterprises with remote or globally distributed teams that require cloud-first, real-time protection with minimal endpoint drag. A top choice for businesses with lean security teams who rely on automation and managed threat intel.
Pricing
Tiered pricing based on modules (e.g., Falcon Prevent, Insight, Overwatch). Requires a custom quote for enterprise deployment.
Recommended Read: Strengthening your organization’s endpoint security? Don’t forget to add this endpoint security checklist to your arsenal. Read more here.
3. Microsoft Defender for Endpoint
Microsoft Defender for Endpoint is a cloud-powered EDR solution that leverages native integration with Microsoft 365, Azure Active Directory, and Intune to deliver endpoint protection at scale. It’s built into Windows 10/11 and uses a combination of behavioral sensors, threat intelligence, and cloud security analytics to prevent, detect, and respond to advanced attacks.
Source – Microsoft Learn
Benefits
AI-Driven Threat Detection: Uses machine learning, behavior-based rules, and Microsoft’s massive threat graph to uncover attacks before they spread.
Seamless Integration: Deeply embedded in the Microsoft ecosystem, it shares signals with Office 365, Azure, and Defender for Identity to enrich detection accuracy.
Automated Investigation & Remediation: Leverages automated playbooks to investigate alerts and take remediation steps, reducing analyst workload.
Attack Surface Reduction (ASR): Proactively blocks risky behaviors like script-based attacks or known exploit techniques before they trigger.
Endpoint Vulnerability Management: Built-in dashboard shows unpatched applications and configurations across endpoints, helping reduce attack paths.
Suitable For
Organizations heavily invested in the Microsoft ecosystem, that are looking for tight endpoint protection with native integration. It is ideal for enterprises using Microsoft 365 E5 licenses or Azure-native workloads.
Pricing
Included in Microsoft 365 E5 and Microsoft Defender for Endpoint Plan 2. Separate SKUs are available for non-E5 customers. It requires licensing through Microsoft or authorized partners.
4. SentinelOne Singularity
SentinelOne Singularity is an autonomous, AI-driven EDR solution designed to detect, respond to, and remediate endpoint threats without human intervention. Built on a single-agent architecture, it combines EPP (endpoint protection), EDR, and ActiveEDR to give security teams full visibility and real-time protection across all endpoint activity.
Source – SentinelOne
Benefits
Real-Time Threat Detection: Uses patented behavioral AI to detect malware, ransomware, and in-memory exploits at machine speed.
Autonomous Response & Rollback: Automatically kills malicious processes, quarantines files, and rolls back endpoints to pre-attack states, even for ransomware.
Storyline™ Technology: Tracks and visualizes the full scope of an attack using a process tree, helping teams investigate without pivoting across logs.
Cloud Workload Protection: Extends detection and response to containerized workloads and virtual machines across hybrid environments.
One Agent, One Console: Eliminates the need for multiple agents or tools by combining prevention, detection, and remediation into a single pane of glass.
Suitable For
Enterprises seeking fully autonomous endpoint security, especially those with lean security teams or requiring rapid remediation. Particularly effective in high-risk sectors like finance, healthcare, and government.
Pricing
Subscription-based pricing with tiers (Core, Control, Complete). Enterprise pricing is available through SentinelOne partners.
5. Trend Micro Vision One
Trend Micro Vision One is an extended detection and response platform that consolidates threat data across endpoints, email, servers, and cloud workloads. It builds on Trend Micro’s deep security portfolio to provide integrated EDR capabilities, threat correlation, and root cause analysis—aimed at simplifying investigations and improving detection accuracy.
Source – Trend Micro
Benefits
Cross-Layer Detection: Correlates telemetry from email, endpoints, servers, and cloud to uncover threats that siloed EDR tools might miss.
Integrated Analytics: Uses MITRE ATT&CK mapping and behavioral analysis to detect suspicious activity with high precision.
Threat Intelligence Enrichment: Leverages Trend Micro’s global threat research to enhance detection and contextualize alerts.
Unified Console: Centralized dashboard allows security teams to manage alerts, automate responses, and orchestrate workflows from a single interface.
Built-In Playbooks: Pre-defined automated response actions help reduce time-to-containment and streamline common remediation tasks.
Suitable For
Mid-sized enterprises or regulated industries looking for consolidated protection across multiple attack surfaces; especially if already using Trend Micro tools for endpoint or email security.
Pricing
Modular pricing based on deployed sensors (endpoint, email, server, etc.). Available through Trend Micro partners with tiered enterprise options.
6. Carbon Black
Carbon Black is a behavioral-based EDR platform that detects, investigates, and responds to advanced threats across endpoints and workloads. Now part of Broadcom’s enterprise security portfolio, it delivers real-time telemetry, continuous recording, and deep visibility into attack chains. This makes it a strong fit for forensic investigations and proactive threat hunting.

Source – Broadcom
Benefits
Continuous Endpoint Monitoring: Records endpoint activity to build a timeline of events, even before an alert is triggered is vital for retrospective investigations.
Behavioral Threat Detection: Uses behavioral patterns instead of static signatures to detect unknown threats and attacker TTPs (tactics, techniques, procedures).
Real-Time Threat Hunting: Supports advanced queries using Carbon Black’s proprietary query language to search for indicators of compromise.
Lightweight Sensor: Deployed as a single lightweight agent that minimizes performance overhead on endpoints.
Cloud-Native Console: Centralized management with customizable dashboards, workflows, and integrations with SIEM and SOAR platforms.
Suitable For
Organizations that require deep forensics, real-time telemetry, and advanced threat hunting. This is especially true in sectors like defense, manufacturing, and finance, where visibility and compliance are critical.
Pricing
Tiered pricing based on modules (e.g., Cloud Endpoint Standard, Advanced, Enterprise). Available through VMware resellers and MSSP partners.
7. Cisco Secure Endpoint
Cisco Secure Endpoint (formerly AMP for Endpoints) is an enterprise-grade EDR solution that integrates advanced malware protection with real-time detection, response, and analytics. Built to work seamlessly within Cisco’s broader security ecosystem, it combines endpoint telemetry with threat intelligence from Cisco Talos. The latter is one of the largest commercial threat intelligence teams in the world.

Source – Cisco
Benefits
Global Threat Intelligence: Leverages Cisco Talos to detect and prevent emerging threats using up-to-the-minute indicators and behavioral analytics.
Automated Response & Containment: Automatically isolates compromised endpoints, kills malicious processes, and enforces custom response actions.
Retrospective Detection: Continuously records endpoint activity, allowing it to retrospectively flag threats even after initial execution.
Centralized Management: A cloud-native console delivers full visibility and control across distributed environments, including roaming devices.
Ecosystem Integration: Tight integrations with Cisco SecureX, Umbrella, Secure Firewall, and Identity Services Engine (ISE) enable coordinated, cross-domain response.
Suitable For
Enterprises already using Cisco’s security and networking stack—including SecureX, AnyConnect, or Cisco Umbrella—and looking for centralized endpoint protection within a unified architecture.
Pricing
Subscription-based pricing available in three tiers: Essentials, Advantage, and Premier. Discounts are available via Cisco security bundles or partner MSSP offerings.
Editor’s Note: Choosing the right EDR tool is just one part of the puzzle. To cover all bases, from device hardening to incident response, use our Endpoint Security Checklist. It’s a practical guide to help IT and security teams lock down every endpoint.
Top EDR Solutions Showdown: Which Solution Fits Your Security Needs Best?
| Tool | AI Detection & Analytics | Automated Response | Cross-Platform Visibility | Best For | Deployment Model |
| Cortex XDR | Advanced ML, Behavioral AI | Yes | Endpoint, network, cloud | Enterprises using Palo Alto stack or needing XDR-level visibility | Cloud-delivered |
| CrowdStrike Falcon | IOA-based ML, Threat Intel | Yes | Global, cloud-native | Fast deployment, remote workforces, minimal endpoint impact | Cloud-native |
| Microsoft Defender | Microsoft Threat Graph, AI | Yes | Microsoft 365, Azure, OS | Microsoft 365 or Azure-native environments | Integrated with OS |
| SentinelOne | Patented behavioral AI | Yes with rollback | Endpoints, cloud VMs | Teams needing autonomous protection with minimal manual effort | Cloud-first |
| Trend Micro Vision One | Cross-vector analytics | Yes with playbooks | Email, endpoint, server | Mid-sized orgs needing multiple vector protection | Hybrid |
| Carbon Black | Behavioral analytics, live queries | Yes with investigation | Real-time endpoint telemetry | Teams focused on forensics, threat hunting, and compliance | Cloud-native |
| Cisco Secure Endpoint | Talos-powered intelligence | Yes | Endpoints + Cisco ecosystem | Enterprises using Cisco SecureX or Umbrella | Cloud-based |
Now that you’ve seen how the top EDR solutions stack up, one thing becomes clear: even the most advanced platform needs expert implementation to deliver real security outcomes.
That’s where Datacipher comes in.
How Datacipher Solutions Maximizes Cortex XDR?
Among the top EDR solutions we’ve explored, Palo Alto Networks Cortex XDR stands out for its unified visibility, powerful automation, and AI-driven threat detection. But even the most advanced platform needs the right hands to deliver real results.
That’s where Datacipher Solutions comes in.
We don’t just deploy Cortex XDR. We tailor it to your business, integrate it with your ecosystem, and continuously optimize it to keep pace with evolving threats.
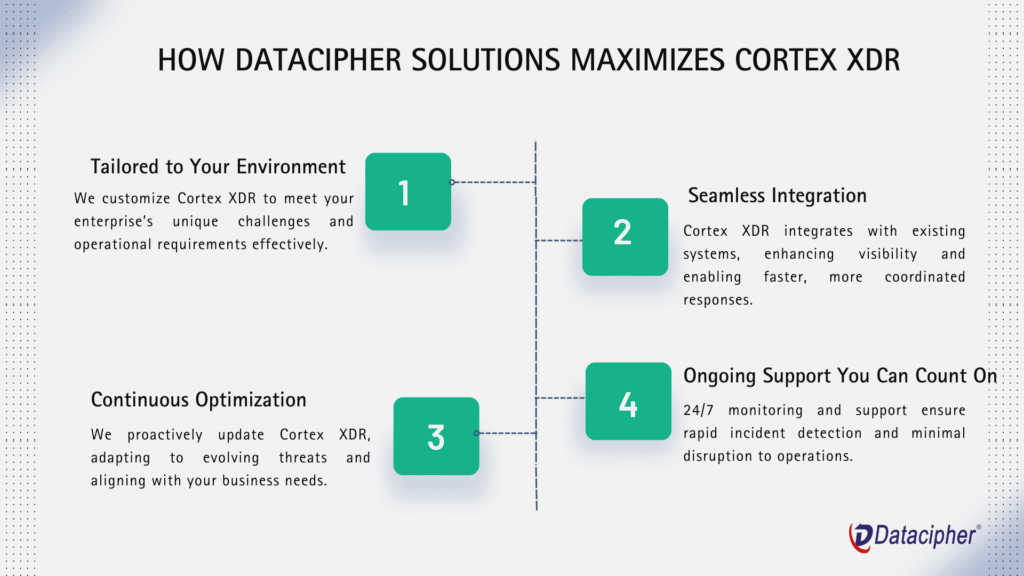
Tailored to Your Environment
Every organization has unique needs. Whether you’re managing a remote workforce, branch networks, or high-security workloads, we design and implement Cortex XDR to align with your specific security objectives and infrastructure.
Seamless Integration
We ensure Cortex XDR connects effortlessly with your existing tools—Palo Alto firewalls, SIEMs, cloud environments—creating a unified defense that strengthens every layer of your security posture.
Continuous Optimization
Cyber threats evolve every day. Our team proactively fine-tunes Cortex XDR, ensuring your policies and workflows stay aligned with emerging risks and your evolving business needs.
Ongoing Support You Can Count On
Security doesn’t sleep, and neither do we. With 24/7 support and monitoring, we ensure incidents are detected and addressed quickly, minimizing disruption to your business.
Empowering Your Team with Top EDR Solutions

We don’t just install Cortex XDR. We equip your teams with the training, playbooks, and forensic guidance they need to use it effectively and confidently in real-world scenarios.
At Datacipher Solutions, we combine deep technical knowledge with a business-first mindset to help you secure your endpoints, simplify your operations, and stay ahead of threats, so you can focus on scaling your business with confidence.
Are you ready to get the most out of Cortex XDR? Consult our experts to get started with deploying, integrating, and optimizing it for your business.
Recommended Read: Looking for an affordable way to strengthen your business security? Download our free guide: The SMB Guide to Affordable, Enterprise-Grade Security to explore cost-effective strategies.

Frequently Asked Questions about Top EDR Solutions
1. What is endpoint security?
Endpoint security is a strategy to protect devices like laptops, desktops, and servers from cyber threats. It includes antivirus, EDR, encryption, and access controls—all designed to prevent, detect, and respond to attacks targeting individual devices.
2. What is an EDR solution?
EDR (Endpoint Detection and Response) is a cybersecurity tool that monitors, detects, and responds to threats on endpoint devices like laptops and servers. It provides real-time visibility, automated response actions, and forensic insights to help security teams stop advanced attacks before they spread.
3. How is EDR different from traditional antivirus software?
Traditional antivirus relies on known threat signatures. EDR uses behavioral analysis and machine learning to detect unknown or fileless threats. It also includes response capabilities, attack timelines, and threat hunting. These are the things antivirus alone can’t do.
4. What’s the difference between EDR and XDR?
EDR focuses on protecting endpoints. XDR (Extended Detection and Response) goes further, correlating data across endpoints, networks, email, and cloud. XDR gives security teams a unified view of attacks across multiple systems, not just endpoint devices.
Editor’s Note: Want to know how EDR differs from MDR, SIEM from SOAR, EDR vs. SIAM, and more such questions? This beautifully crafted and detailed guide will answer all your questions – EDR vs MDR vs XDR vs SIEM vs SOAR vs Antivirus: Which Cybersecurity Solution Fits Your Organization’s Needs?
5. Can EDR tools detect insider threats?
Yes. EDR platforms use behavioral baselining to flag unusual activity from trusted users like unauthorized access or data exfiltration. They help detect insider threats that traditional tools might miss.





