Cybersecurity is full of technical jargon, evolving threats, and endless security recommendations. Businesses know they need to protect their systems, but when it comes to vulnerability assessments and penetration testing, most find themselves asking: What’s the difference? Which one do we actually need?
A quick online search only adds to the confusion – overloaded with complex explanations and conflicting opinions. That’s why we created this no-nonsense, expert-backed FAQ guide to break down the most frequently asked questions in a way that’s clear, actionable, and easy to understand.
Whether you’re wondering how a vulnerability assessment works, why penetration testing is necessary, or how much it costs, this guide has the answers—straight from cybersecurity experts, explained in simple terms.
Let’s dive in, starting with the most-asked question on the subject.
#1. What is the Difference between Vulnerability Assessment and Penetration Testing?
A vulnerability assessment systematically scans and identifies security weaknesses in an organization’s IT infrastructure, applications, and networks. It focuses on risk identification and prioritization using automated tools and manual analysis, without actively exploiting vulnerabilities.
A penetration test, on the other hand, simulates real-world attacks to exploit security gaps and determine how deep an attacker could penetrate the system. It goes beyond detection. It tests actual security defenses, mimicking hacker techniques. Below, we have listed the key differences in scope between vulnerability assessment and penetration testing.
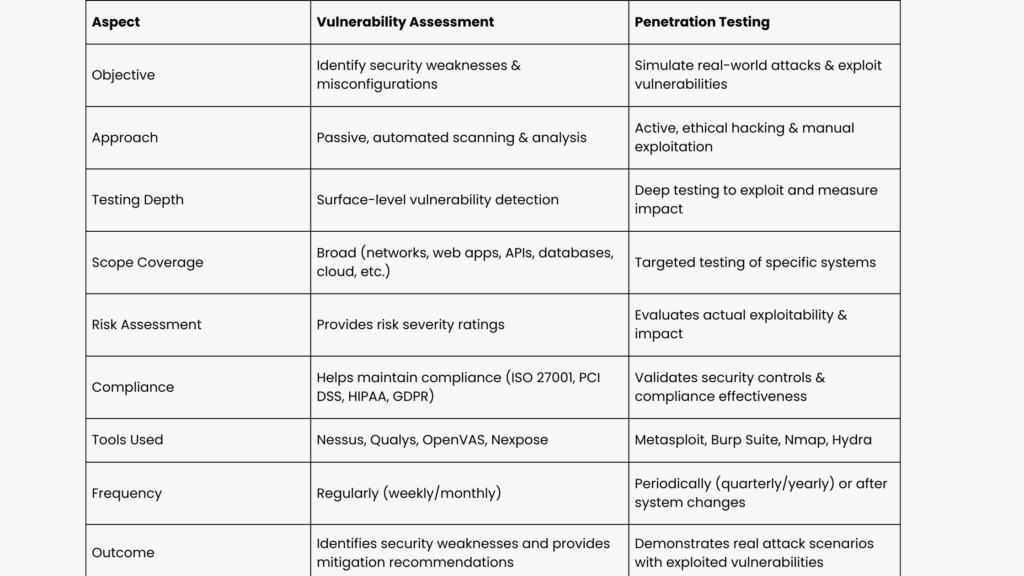
For maximum security, organizations should combine both vulnerability assessment and penetration testing. The former is for ongoing risk management, and the latter is for simulating real-world attack scenarios.
If you’re looking for an expert vulnerability assessment and penetration testing services provider, contact Datacipher today.
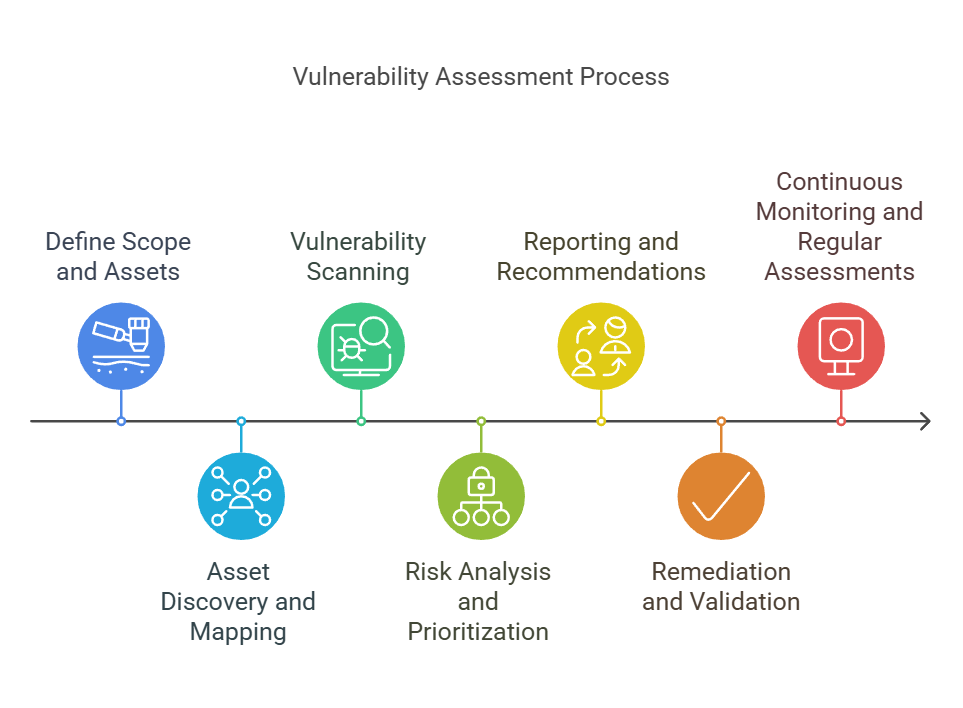
#2. How to conduct a Vulnerability Assessment?
A vulnerability assessment follows a structured process to identify, analyze, and prioritize security weaknesses. Here’s how it is typically done:
- Define scope and assets – Identify which systems, networks, applications, or cloud environments need assessment.
- Asset discovery and mapping – Create an inventory of IT assets to ensure all critical components are included.
- Vulnerability scanning – Use automated tools (e.g., Nessus, Qualys, OpenVAS) to scan for known vulnerabilities, misconfigurations, and security gaps.
- Risk analysis and prioritization – Categorize vulnerabilities based on severity, exploitability, and potential business impact.
- Reporting and recommendations – Generate a detailed report outlining security weaknesses, risk levels, and recommended remediation steps.
- Remediation and validation – Implement fixes (patching, configuration changes, etc.), then re-scan to verify resolution.
- Continuous monitoring and regular assessments – Security is an ongoing process; vulnerability assessments should be conducted regularly to keep up with evolving threats.
Recommended Read: 7 Things to Look for When Choosing a Vulnerability Assessment Company
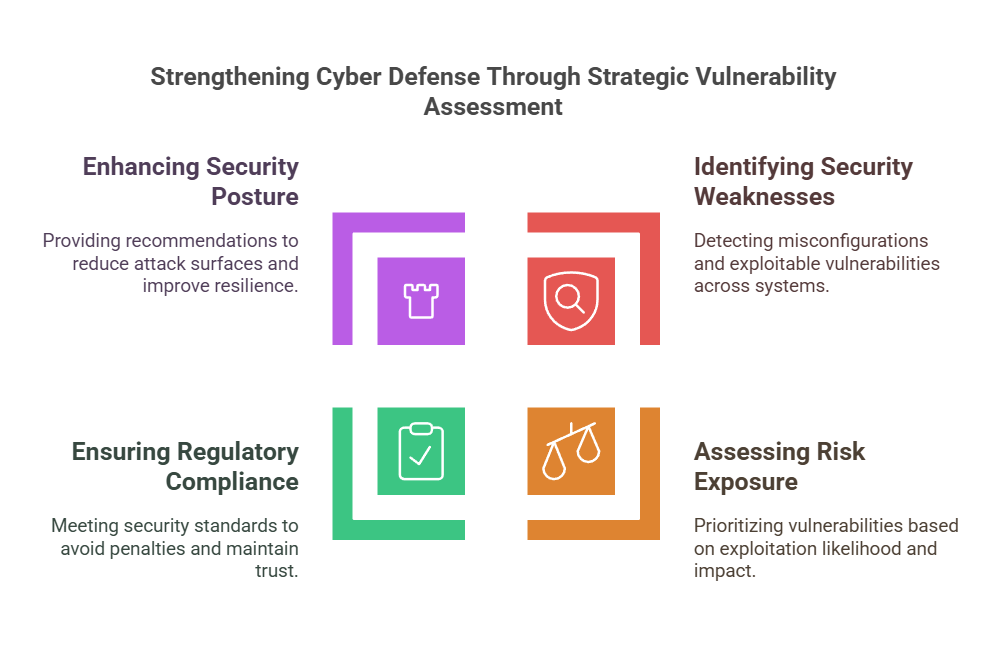
#3. What are the key goals of a vulnerability assessment?
A vulnerability assessment is designed to help organizations proactively identify and mitigate security risks before they can be exploited. It provides a structured approach to evaluating weaknesses, ensuring businesses can strengthen their defenses and reduce potential attack surfaces.
Some of its key objectives include:
- Identifying security weaknesses – Detecting misconfigurations, outdated software, and exploitable vulnerabilities across networks, applications, and cloud environments.
- Assessing risk exposure – Prioritizing vulnerabilities based on their likelihood of exploitation and potential impact on business operations.
- Ensuring regulatory compliance – Meeting security standards such as ISO 27001, PCI DSS, HIPAA, and GDPR to avoid penalties and maintain trust.
- Enhancing overall security posture – Providing actionable recommendations that help organizations reduce attack surfaces and improve cyber resilience.
#4. How much does a vulnerability assessment cost?
The cost of a vulnerability assessment varies based on complexity, scope, compliance requirements, and industry standards. Prices typically range from $1,000 to $10,000, with larger, highly regulated environments costing more. Factors like asset count, testing depth, and frequency also impact pricing.
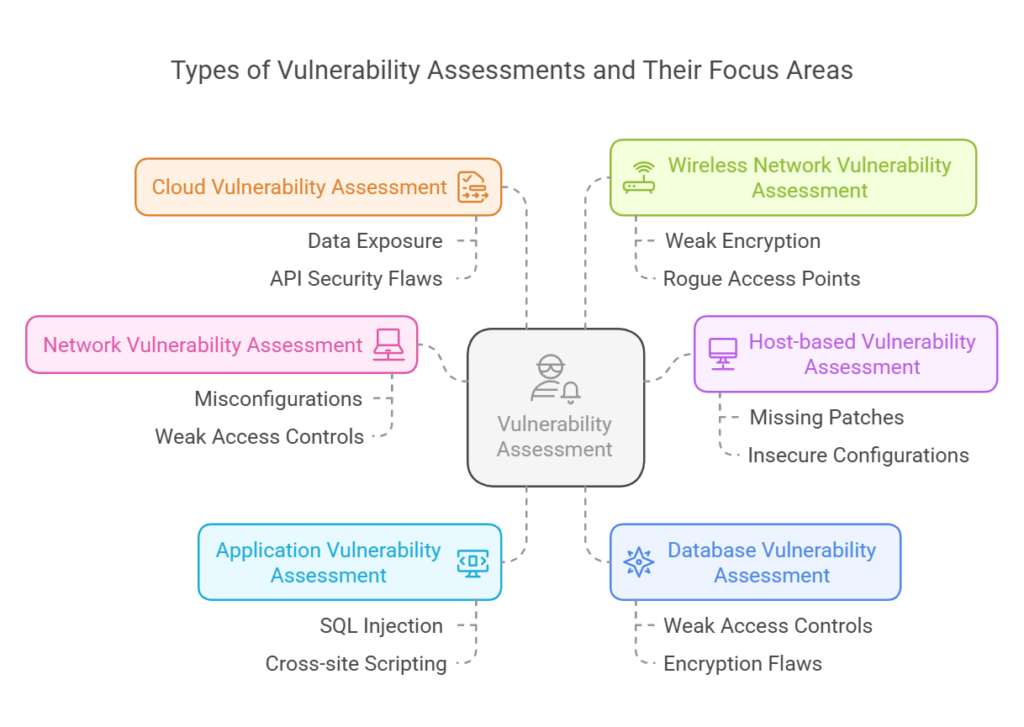
#5. What are the different types of vulnerability assessments?
A vulnerability assessment is a structured evaluation of security weaknesses across an organization’s IT environment. Different types of assessments target specific areas of risk. Major ones include:
#1. Network vulnerability assessment – Scans internal and external networks to detect misconfigurations, weak access controls, and exposed entry points that attackers can exploit.
#2. Host-based vulnerability assessment – Evaluates servers, workstations, and endpoints for missing patches, insecure configurations, and malware risks at the operating system and application level.
#3. Application vulnerability assessment – Identifies security flaws in web, mobile, and cloud applications, including SQL injection, cross-site scripting (XSS), and authentication vulnerabilities.
#4. Database vulnerability assessment – Focuses on securing databases by identifying weak access controls, encryption flaws, misconfigurations, and unpatched vulnerabilities.
#5. Cloud vulnerability assessment – Examines misconfigurations in cloud environments (AWS, Azure, GCP) that could lead to data exposure, API security flaws, and weak identity management.
#6. Wireless network vulnerability assessment – Assesses Wi-Fi networks for weak encryption, rogue access points, and insecure protocols that could allow unauthorized access.
Each type of vulnerability assessment plays a critical role in securing an organization’s digital infrastructure by identifying and mitigating risks before they can be exploited.
#6. What is a network vulnerability assessment?
A network vulnerability assessment is a security evaluation that identifies weaknesses in an organization’s internal and external networks. It scans network devices like routers, firewalls, and servers for misconfigurations, unpatched software, weak access controls, and exposed services that attackers could exploit.
By conducting regular network vulnerability assessments, organizations can proactively reduce their attack surface and prevent cyber threats.
#7. How to conduct a threat vulnerability assessment?
A Threat vulnerability assessment goes beyond standard vulnerability assessments by incorporating threat intelligence to evaluate how vulnerabilities might be actively exploited by attackers.
Here’s the process followed by organizations when conducting this assessment:
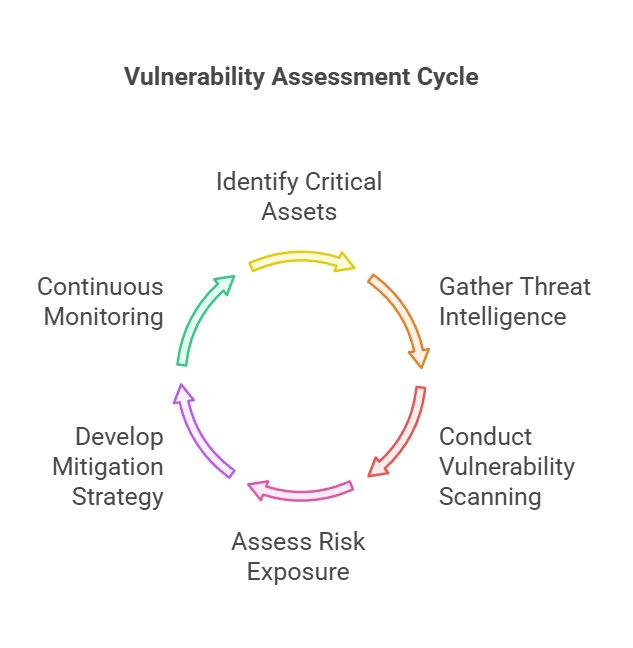
- Identify critical assets – Determine which systems, data, and infrastructure need protection.
- Gather threat intelligence – Analyze emerging cyber threats, attack patterns, and adversary tactics relevant to the industry.
- Conduct vulnerability scanning – Use tools like Nessus, Qualys, or OpenVAS to identify security weaknesses.
- Assess risk exposure – Prioritize vulnerabilities based on likelihood, potential attack vectors, and real-world threats.
- Develop a risk mitigation strategy – Implement patches, update security policies, and enhance defenses based on identified threats.
- Continuous monitoring & reassessment – Regularly update threat intelligence and conduct follow-up assessments to stay ahead of evolving threats.
A threat vulnerability assessment is essential for organizations that want to move beyond basic vulnerability management and take a proactive, threat-informed security approach.
#8. What is a security vulnerability assessment?
A security vulnerability assessment systematically identifies, analyzes, and prioritizes security weaknesses across an organization’s IT infrastructure. It uses automated tools and manual techniques to detect misconfigurations, outdated software, and exploitable flaws. The goal is to provide actionable insights to reduce risks and strengthen cybersecurity defenses.
#9. What is a vulnerability assessment tool, and what are some of the most popular ones?
A vulnerability assessment tool is software designed to scan, identify, and analyze security weaknesses in an organization’s IT environment. These tools help detect misconfigurations, outdated software, and potential security risks, allowing businesses to take corrective actions before threats emerge.
Some of the most popular vulnerability assessment tools include Nessus, Qualys, OpenVAS, Rapid7 Nexpose, and Burp Suite, which are widely used for network, endpoint, and application security testing.
#10. What is the relationship between risk management and vulnerability assessment?
A vulnerability assessment is a key part of risk management, helping organizations identify, analyze, and mitigate security weaknesses before they become exploitable threats.
While risk management focuses on overall business risks, vulnerability assessments specifically detect security gaps, prioritize them by severity, and provide actionable remediation steps to strengthen cybersecurity.
Recommended Read: Want to take your security operations to the next level? Understanding vulnerabilities is just the first step—building a strong SOC (Security Operations Center) is what ensures ongoing protection. Download our free eBook Five Essential Steps to SOC Transformation to learn how to enhance your organization’s security posture and streamline threat detection.

#11. Which type of vulnerability cannot be discovered in the course of a typical vulnerability assessment?
A vulnerability assessment primarily detects known security flaws but may miss zero-day vulnerabilities, business logic flaws, and insider threats that require human expertise to uncover.
It also does not test for real-world exploitability like social engineering attacks, advanced persistent threats, or configuration issues that arise under specific conditions. To identify these risks, penetration testing and red teaming are often necessary.
#12. Why might penetration testing still be needed after a vulnerability assessment?
A vulnerability assessment identifies security flaws but does not test how they can be actively exploited in real-world attack scenarios. Penetration testing goes a step further by simulating attacks to assess exploitability, security control effectiveness, and actual business impact.
While VA focuses on detection and risk classification, penetration testing helps validate vulnerabilities, uncover hidden attack paths, and test an organization’s response to real threats. Penetration testing is essential for organizations needing deeper security validation beyond automated scans.
#13. How does penetration testing work?
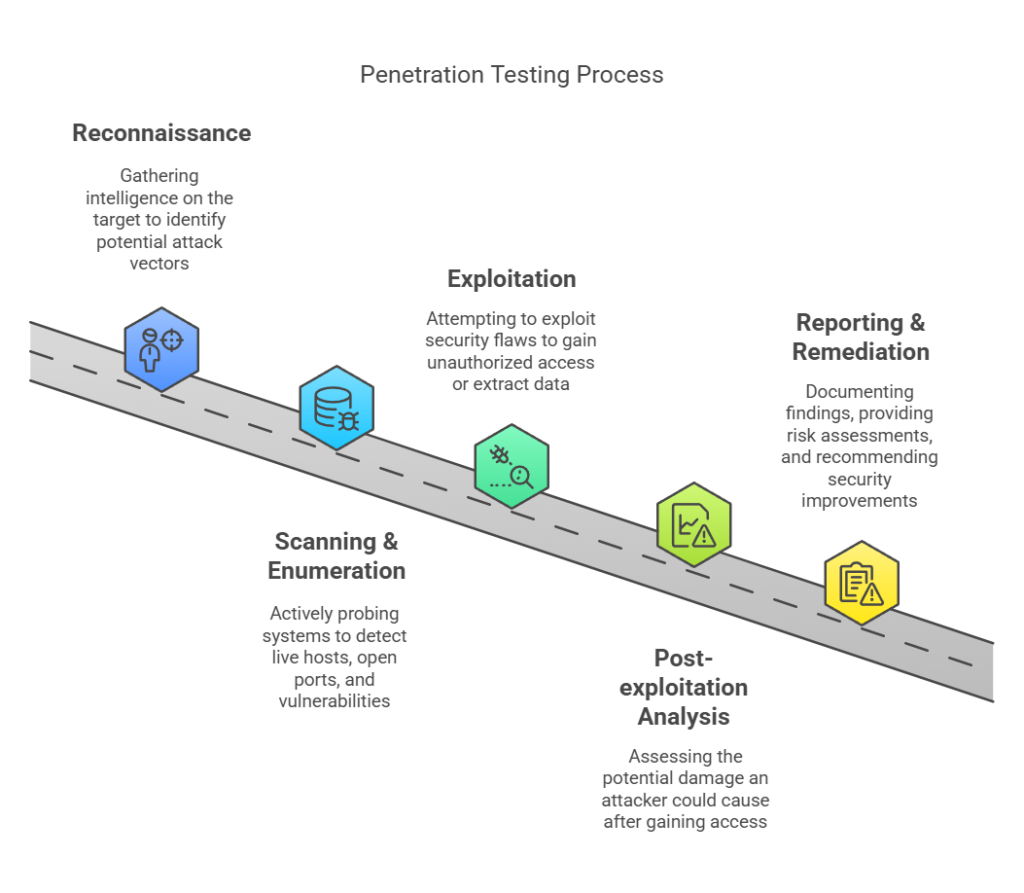
Penetration testing follows a structured approach to simulate real-world cyberattacks and assess how easily an attacker could exploit vulnerabilities. The process typically includes:
#1. Reconnaissance – Gathering intelligence on the target (e.g., domains, IP addresses, employee emails) to identify potential attack vectors.
#2. Scanning & enumeration – Actively probing systems to detect live hosts, open ports, services, and known vulnerabilities.
#3. Exploitation – Attempting to exploit security flaws to gain unauthorized access, escalate privileges, or extract sensitive data.
#4. Post-exploitation analysis – Assessing the potential damage an attacker could cause after gaining access.
#5. Reporting & remediation – Documenting findings, providing risk assessments, and recommending security improvements.
#14. What are the different types of penetration testing?
Penetration testing can target different areas of an organization’s security, depending on the threat landscape and business needs. The most common types include:
#1. Network penetration testing – Assesses external and internal networks for vulnerabilities such as misconfigured firewalls, open ports, and weak authentication mechanisms.
#2. Web application penetration testing – Identifies security flaws in web apps, APIs, and databases, including SQL injection, cross-site scripting, and authentication bypass.
#3. Wireless penetration testing – Evaluates Wi-Fi networks for weak encryption, rogue access points, and unauthorized devices that could lead to network breaches.
#4. Social engineering penetration testing – Simulates phishing attacks, impersonation, and physical security breaches to test employee awareness and resilience against human-targeted attacks.
#5. Physical penetration testing – Tests physical security controls such as access restrictions, badge authentication, and surveillance systems by attempting unauthorized entry.
#6. Cloud penetration testing – Identifies misconfigurations, data exposure risks, and API vulnerabilities in cloud environments like AWS, Azure, and Google Cloud.
Each type of penetration test provides a real-world security assessment, ensuring organizations can detect and mitigate threats before attackers can exploit them.
#15. Why is penetration testing important, and what are its benefits?
Penetration testing helps organizations identify exploitable vulnerabilities, validate security controls, and reduce the risk of cyberattacks. It ensures compliance with industry regulations while improving incident response and overall security posture. By simulating real-world threats, businesses can proactively detect weaknesses and strengthen defenses before attackers exploit them.
#16. How does penetration testing help with compliance requirements?
Penetration testing ensures organizations meet regulatory and industry compliance standards by identifying security weaknesses that could lead to data breaches. Many frameworks, including PCI DSS, ISO 27001, HIPAA, and GDPR, require regular security testing to validate defenses.
Here’s how it aligns with specific compliance frameworks:
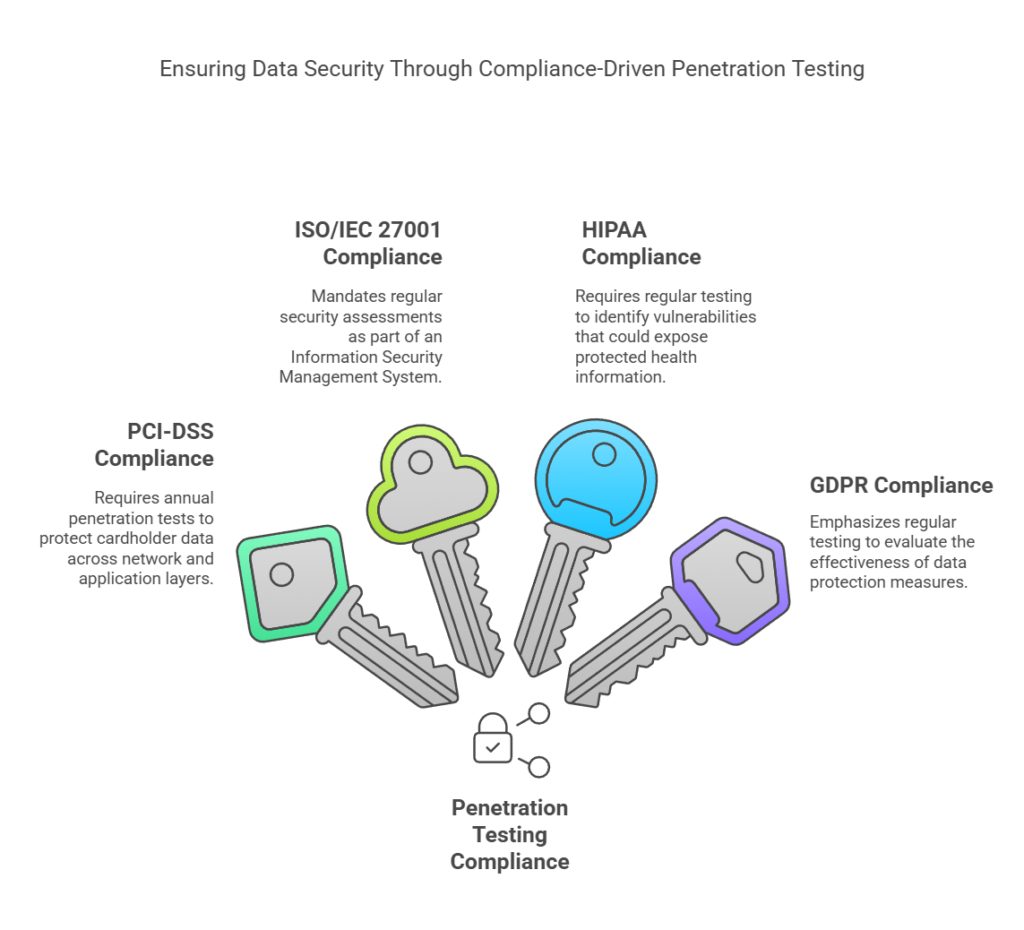
#1. PCI-DSS (Payment Card Industry Data Security Standard): Requires annual and after-significant-change penetration tests to protect cardholder data. Testing must cover network and application layers to ensure robust defenses against breaches.
#2. ISO/IEC 27001: Mandates regular security assessments, including penetration testing, as part of its Information Security Management System (ISMS) to identify and mitigate risks, ensuring the confidentiality, integrity, and availability of information.
#3. HIPAA (Health Insurance Portability and Accountability Act): Requires healthcare organizations to conduct regular penetration tests to identify vulnerabilities that could expose protected health information (PHI), ensuring compliance with the Security Rule.
#4. GDPR (General Data Protection Regulation): Emphasizes the need for regular testing and assessment of technical measures to ensure data protection, with penetration testing serving as a method to evaluate the effectiveness of these measures.
By conducting regular penetration tests, organizations can proactively identify and remediate vulnerabilities, thereby ensuring compliance with these standards and protecting sensitive data.
#17. What is the difference between black box, white box, and gray box penetration testing?
Penetration testing is categorized into three approaches based on the tester’s knowledge of the system:
- Black Box Testing – The tester has no prior knowledge of the target system. This simulates a real-world external attack where hackers must gather intelligence before exploiting vulnerabilities.
- White Box Testing – The tester has full access to system architecture, source code, and credentials. This method provides a deep security evaluation, identifying flaws that may be overlooked in black-box testing.
- Gray Box Testing – A hybrid approach where the tester has partial knowledge (e.g., login credentials but not full system details). This simulates attacks from insiders or compromised user accounts and helps evaluate privilege escalation risks.
Each method serves a different security objective, and organizations often combine them for a comprehensive security assessment.
#18. What is Red teaming?
Red teaming is an advanced cybersecurity exercise where ethical hackers simulate real-world attacks to test an organization’s defenses. Unlike penetration testing, it mimics persistent threats, using tactics like social engineering, network exploitation, and physical security testing to uncover security gaps.
#19. What are some popular penetration testing tools?
Popular penetration testing tools include Metasploit, Burp Suite, Nmap, Wireshark, SQLmap, Hydra, and John the Ripper. These tools help identify security vulnerabilities in networks, applications, and databases, forming the foundation for ethical hacking and security assessments.
#20. Should you hire a penetration testing provider or use tools yourself?
While penetration testing tools can identify security flaws, expert-led assessments offer deeper insights and real-world attack simulations. Here’s how both compare:
| Factor | Using Tools Yourself | Hiring a Provider |
| Expertise and Strategy | Relies on automation, lacks human creativity, and strategic attack thinking. | Ethical hackers simulate real-world attacks, uncovering advanced vulnerabilities. |
| Compliance and Standards | No guarantee of compliance with PCI DSS, ISO 27001, HIPAA, etc. | Ensures penetration testing aligns with regulatory and industry standards. |
| False positives and accuracy | May generate false positives, requiring manual review. | Experts validate and prioritize real risks, reducing unnecessary alerts. |
| Depth of testing | Limited to tool capabilities; cannot simulate complex, multi-layered attacks. | Simulates real-world scenarios, including social engineering and lateral movement. |
| Comprehensive reporting | Provides raw data without actionable remediation insights. | Delivers in-depth reports with risk assessments and step-by-step fixes. |
| Cost and time | Lower upfront cost but requires in-house expertise and time. | Higher cost but provides thorough security validation and expert recommendations. |
While penetration testing tools provide a starting point, they lack strategic attack modeling, compliance assurance, and expert risk validation. For thorough security assessments, hiring a provider is the better choice.
#21. What are the limitations of penetration testing?
Penetration testing simulates attacks but has limitations. It only tests security at a single point in time, may miss insider threats and zero-day vulnerabilities, and focuses on specific systems rather than the entire network. It also cannot replace ongoing security monitoring.
For a stronger defense, penetration testing should be combined with regular vulnerability assessments to detect and mitigate risks continuously.
#22. How often should vulnerability assessments and penetration testing be performed?
Vulnerability assessments should be conducted regularly, either weekly or monthly, to maintain security hygiene and detect emerging risks. Penetration testing should be performed quarterly or annually, or after significant system updates, to evaluate real-world exploitability.
For stronger security, organizations should combine frequent vulnerability assessments with periodic penetration testing to detect and validate vulnerabilities effectively.
#23. How to Choose the Right Vulnerability Assessment and Penetration Testing Provider?
Choosing the right vulnerability assessment and penetration testing provider is critical to strengthening your security posture. The ideal partner should not only identify vulnerabilities but also help mitigate them effectively. Here’s what to look for:
- Industry expertise and Certifications – Look for OSCP, CEH, or CISSP-certified professionals with a strong track record in your industry.
- Testing Methodology and Standards – Providers should follow recognized security frameworks like OWASP, NIST, and ISO 27001 for comprehensive assessments.
- Compliance and Data Security – Ensure they align with PCI DSS, HIPAA, GDPR, and other regulations while maintaining strict confidentiality protocols.
- Detailed reporting and Support – Look for clear, actionable reports with remediation guidance and post-assessment support to fix vulnerabilities.
By carefully evaluating potential providers based on these criteria, you can select a partner that not only identifies vulnerabilities but also enhances your organization’s overall security posture.
Why Datacipher Solutions is the Right Partner for your Vulnerability Assessment and Penetration Testing Needs?
Cyber threats are relentless. New vulnerabilities emerge every day, and a single overlooked security gap can lead to financial loss, reputational damage, or regulatory penalties. You need a partner that doesn’t just scan for threats but actively works to secure your business. That’s why you need Datacipher Solutions as your threat management partner. We have:
Proven expertise with a track record of Success
With 650+ successful projects, 30+ industry awards, and recognition like the Worldwide Highest Customer Satisfaction Award from Juniper Networks, Datacipher has established itself as a trusted cybersecurity partner across industries.
Our penetration testers and security experts hold top certifications like OSCP, CEH, and CISSP, ensuring deep technical expertise and real-world attack simulation capabilities.
End-to-End Security Testing & Compliance Readiness
We provide comprehensive security assessments covering network, cloud, application, and endpoint security by not just identifying vulnerabilities but demonstrating how attackers could exploit them.
Our solutions align with PCI DSS, ISO 27001, HIPAA, GDPR, and other major regulatory requirements, helping you stay compliant without unnecessary complexity.
Beyond Reports – Actionable fixes & Continuous security
Most providers hand you a report and walk away. We don’t. Datacipher delivers detailed risk analysis, remediation strategies, and post-assessment support, ensuring your security actually improves not just on paper, but in practice.
Security that scales with your business
Whether you’re a growing startup, a multinational enterprise, or a government agency, our cybersecurity solutions are tailored to your needs, designed for scalability, and adaptable to evolving threats.
Attackers don’t wait. Neither should you. Partner with Datacipher for proactive, expert-driven security testing that protects your business today and future-proofs it for tomorrow. Request a consultation with us here.





