When a Mumbai-based pharma company got hit with a targeted ransomware attack last December, it wasn’t because they didn’t care about cybersecurity. They had an internal team. They had tools. What they didn’t have was real-time detection, around-the-clock monitoring, or a threat response protocol that could act before the breach spiraled into six days of downtime.
Their mistake wasn’t negligence. It was the belief that in-house was enough. And it’s a belief a lot of Indian enterprises are rethinking right now. Across sectors like BFSI, pharma, logistics, and IT, internal security teams are under siege.
DPDPA compliance has raised the bar. Threats are now faster, stealthier, and powered by AI. And most internal setups aren’t built to run a Security Operations Center at enterprise scale.
That’s why managed security service providers (MSSPs) are the strategic shift today’s enterprises need. The right MSSP doesn’t just monitor. It hunts, responds, remediates, and reports—24x7x365. It extends your team without bloating your overhead.
We’ve curated and vetted the top managed security service providers in India by performance. This guide is built for enterprise leaders comparing serious contenders. Whether you’re reevaluating a current partner, shifting from in-house security, or building your cybersecurity stack from the ground up, this article will help you make a confident, well-informed choice.
Let’s get started.
What Makes a World-Class MSSP?
Too many Indian enterprises think their cybersecurity is fine. Until the breach hits. And by then, it’s never about the firewall. It’s about the gaps between people, process, and response.
Internal SOCs often look impressive from the outside. But inside? There’s tool fatigue, siloed systems, talent churn, and playbooks that exist in theory but fail in practice. Most setups just aren’t built to withstand modern threat velocity.
And in India, the pressure’s higher than ever. You’re dealing with DPDPA, RBI, and industry-specific compliance. Each one is a moving target.
The volume of phishing, insider threats, and third-party exposures is exploding. Most boards now expect security reporting with the same precision as finance.
This is where a true MSSP proves its value. Not in brand slides, but in battle-readiness.
Editor’s Note: Not sure whether an MSSP is right for your organization right now? Then this guide on outsourcing managed security services will come in handy. It breaks down seven high-impact use cases for outsourcing and three situations where in-house still wins. This checklist can help you determine whether or not you are ready for outsourcing. Download it here. If you’re ready, continue reading.
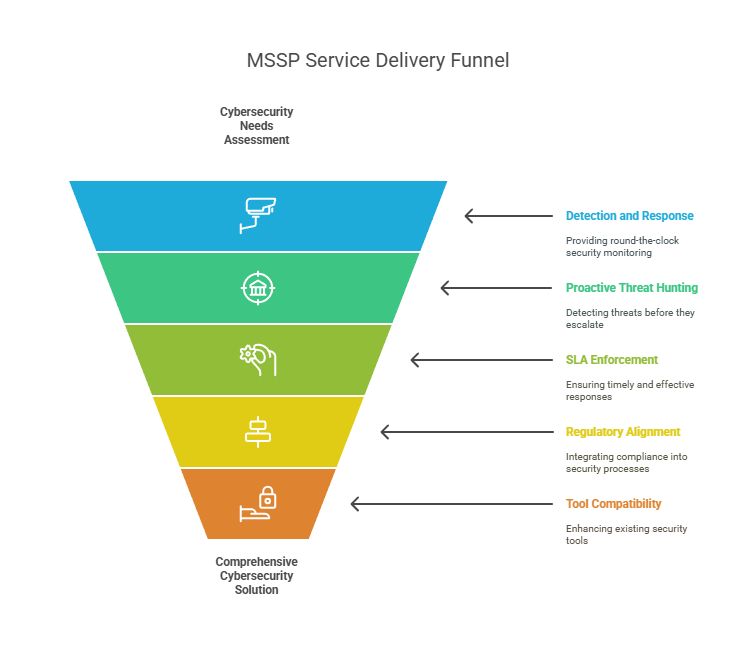
Round-the-clock detection and response: The best MSSPs operate real SOCs with Tier-2 and Tier-3 analysts working in shifts. Not part-time engineers on pager duty. You get 24x7x365 visibility, response, and containment when it matters most.
Proactive threat hunting (Real MDR): Modern MSSPs don’t wait for EDR to raise a flag. They detect lateral movement, privilege misuse, and subtle anomalies across networks and endpoints, often hours before tools catch up.
SLAs that enforce urgency: Timelines matter. A 40-minute response isolates one compromised device. A four-hour delay shuts down your entire operation. World-class MSSPs commit to strict SLAs and consistently deliver on them.
Built-in regulatory alignment: From SEBI to DPDPA, compliance isn’t bolted on. It’s embedded in the MSSP’s processes, dashboards, and audit trails. With a good MSSP, you’re never left scrambling before a board meeting or a breach notification.
Tool and platform compatibility: A mature MSSP integrates with your environment, whether it’s Microsoft Sentinel, CrowdStrike, Fortinet, or a mixed legacy stack, and enhances what’s already in place. They do not pressure you to rip and replace.
Recommended Resource: Want to know how MSSPs gain visibility into everything they’re securing? Download our guide on the 10 Essential Use Cases for Attack Surface Management to understand how advanced ASM solutions proactively discover exposures, eliminate blind spots, and shrink your attack surface.

End-to-end visibility: Logs aren’t enough. You need behavioral analysis, cross-platform correlation, and real-time context across cloud, endpoints, identity systems, and network traffic. World-class MSSPs stitch that together into one operational view.
Autonomous containment and action: In a live breach, hesitation costs millions. The best MSSPs act first and inform second. They isolate machines, trigger containment workflows, and communicate resolution, not excuses.
A world-class MSSP doesn’t ask, “What do you want us to monitor?” They say, “Here’s what we saw. Here’s what we did. Here’s what you need to fix.”
You’re about to meet the few in India who actually deliver on that standard, starting with Datacipher Solutions.
Datacipher Solutions: Built for the Real Demands of Enterprise Security
Every enterprise arrives at managed security from a different path.
Some are replacing a partner who overpromised and underdelivered. Others are scaling beyond what their internal teams can support. Some are navigating compliance mandates under DPDPA or SEBI. Others simply know the next attack won’t wait for another budget cycle.
That’s where we come in.
Source – Datacipher
At Datacipher, we don’t just offer visibility. Our Managed Security Services are built to act, not just alert. And we’ve designed every layer of our stack to serve Indian enterprises that can’t afford second chances.
Here’s where Datacipher stands apart:
Operationalized SIEM, not just centralized logs
Our integrated SIEM solutions are tailored to your IT environment—whether it’s Microsoft Sentinel, Fortinet, or a complex hybrid setup. We bring context to telemetry, cutting through alert noise with real-time, actionable insight.
Proactive detection and real-time response
We don’t wait for EDR to blink. Our analysts detect behavioral anomalies, lateral movement, and privilege misuse across systems, often before the tools raise the flag. The response isn’t queued but executed.
Compliance that’s built into the stack
We don’t bolt on compliance reporting after the fact. From DPDPA to RBI to ISO 27001, our operations are built to generate audit-ready records by default. There is nothing left to assemble when the auditor calls.
Privileged Access Management that doesn’t slow down ops
We secure high-value access points—admin consoles, sensitive databases, CI/CD pipelines—without dragging down user experience. Your engineers move fast, and we keep the doors locked behind them.
Seamless integration with your existing tools and workflows
You don’t have to rip and replace to work with us. We integrate with your existing tech stack, workflows, and escalation protocols so we become an extension of your team, not another silo.
We treat integration like a discipline, not an afterthought. Whether you’re coming from another MSSP, rebuilding after a breach, or tightening an in-house model, we slot in fast, clean, and with zero disruption.
We’re also one of the few MSSPs in India with true multicloud capability. Whether you operate across AWS, Azure, GCP, or hybrid combinations, our platform integrates natively across providers. That means no fragmented dashboards, no policy gaps, and no lag in visibility. Just real-time protection, wherever your workloads live.
Add to it the fact that we don’t offer a one-size-fits-all service. It’s security, engineered for your operational reality.
In a world where most providers aim to monitor, we’re built to manage.
CISO Insight
If your MSSP can’t show you which 10% of threats account for 90% of your actual risk, you don’t have a managed security partner. You have a notification vendor.
World-class security isn’t about noise. It’s about precision. Ask every MSSP provider: What do you prioritize first, and why?
#2. Tata Consultancy Services
Tata Consultancy Services (TCS) offers a broad spectrum of managed security services tailored for large-scale enterprises. Their core offerings include Managed Detection and Response, SOC-as-a-Service, IAM, GRC automation, and vulnerability management.
Source – TCS
They also provide cloud security across Azure and O365, digital forensics, IoT/OT protection, and an integrated Cyber Defense Suite for full-spectrum security operations.
TCS is well-suited for enterprises with complex infrastructures, layered compliance mandates, and high-availability demands. Their security approach blends DevSecOps and platform-native visibility to embed resilience across the tech stack.
For organizations seeking structured governance, broad regulatory alignment, and operational coverage from endpoint to cloud, TCS offers a consolidated and mature MSSP model.
CISO Insight
The broader your digital estate, the harder it gets to tell what’s critical and what’s noise. The right MSSP helps you shrink the attack surface without shrinking visibility.
At scale, it’s not just about detection. It’s about governance, orchestration, and knowing when to act across multiple domains. Make sure your MSSP can do more than monitor. Make sure they can map risk to business impact.
#3. Infosys
Infosys offers a mature suite of managed security services, backed by global Cyber Defense Centers and the proprietary Cyber Next platform. Their MSSP model spans Managed Detection and Response, identity and access security, threat intel, and cloud protection, including posture management and SASE integrations.

Source – Infosys
Infosys leans heavily on automation, with AI-driven detection layered into every tier of monitoring. What stands out is their alignment with digital transformation programs; they design for enterprises shifting into cloud-native, API-driven environments.
Their strength lies in scalable frameworks, risk-based prioritization, and the ability to embed security deeper into the tech stack without slowing velocity. For enterprises seeking an MSSP that can flex across infrastructure types while aligning with business modernization goals, Infosys brings an integrated and automation-first approach.
CISO Insight
Automation is only as good as what it prioritizes. If your MSSP’s AI can’t distinguish a critical API vulnerability from noise, you’ll still be reacting too late.
Ask your provider how their system filters risk across hybrid environments and whether the automation serves your business or just their SOC metrics.
#4. Wipro
Wipro delivers a comprehensive suite of managed security services through its CyberShield platform, designed to provide integrated cyber resilience across complex enterprise environments.
Source: Wipro
Their offerings encompass 24/7 Managed Detection and Response, exposure management, identity and access management, and cloud security services.
Wipro’s approach emphasizes AI-driven automation and analytics to continuously monitor and enhance an organization’s security posture. The Cyber Defense Centers act as vigilant hubs, providing real-time monitoring, detection, and mitigation of cyber threats.
For enterprises seeking a managed security service provider that combines global reach with localized expertise, Wipro offers a scalable and integrated model to fortify security operations without compromising agility.
CISO Insight
Automation without context creates more noise, not less. The real value lies in how well a system filters, correlates, and acts on threats that actually matter.
Before you evaluate AI-driven security operations, ask one question: How does the platform separate high-risk anomalies from harmless alerts?
#5. HCLTech
HCLTech delivers managed security services through its Cybersecurity Fusion Centers, supporting enterprises across hybrid and multi-cloud environments. Their portfolio includes MDR, identity and access management, GRC(Government, Risk and Compliance) services, and vulnerability management.
Source – HCLTech
Cloud security is a key strength, backed by their AWS Level 1 MSSP competency. However, their capabilities are not platform-bound. They offer cross-cloud visibility and protection for hybrid, multi-cloud, and on-premise environments. Their use of automation and analytics helps prioritize threats based on operational context, not just technical severity.
HCL’s MSSP model is built to integrate across IT and cloud stacks, making it suited for enterprises seeking continuous monitoring, compliance readiness, and flexibility in deployment. For organizations balancing modernization with regulatory control, HCLTech offers a security model that scales across architectures.
CISO Insight
Hybrid environments break fast when visibility is fragmented. The real test of any MSSP is whether they can stitch cloud, on-prem, and legacy systems into one threat narrative.
When evaluating providers, go beyond platform certifications. Ask how they correlate risk across architectures and how soon they act when patterns emerge.
#6. Tech Mahindra
Tech Mahindra offers a robust suite of managed security services tailored for enterprises operating in complex digital ecosystems. Their services span infrastructure security, cloud security, identity governance, GRC, data protection, and cyber posture management.
Source – Tech Mahindra
Leveraging their AWS Level 1 MSSP Competency, they provide specialized security solutions for AWS environments, including threat detection, vulnerability management, and compliance monitoring.
Their approach integrates advanced analytics and automation to enhance threat detection and response, aligning security operations with business objectives. For organizations seeking a managed security service provider with a broad portfolio and cloud security expertise, Tech Mahindra presents a scalable and integrated model.
CISO Insight
Your cloud stack is only as secure as its weakest identity, its most exposed workload, or its forgotten misconfiguration.
The right MSSP does not just watch dashboards. They connect those dots in real time, across platforms, accounts, and business units. Ask how they track risk drift before it becomes breach material.
#7. Tata Communications
Tata Communications delivers managed security services with deep integration into its global network and cloud infrastructure. Their portfolio includes 24×7 threat detection and response, cloud and endpoint security, vulnerability assessment, and managed SOC services.
Source – Tata Communications
Enterprise clients can also leverage Secure Connect (SASE), CASB, and Zero Trust solutions for secure access across users, apps, and locations.
What sets Tata Communications apart is its ability to align cybersecurity with network operations backed by global reach, strong interconnectivity, and telecom-grade resilience. For organizations seeking an MSSP that blends threat visibility with infrastructure control, Tata Communications brings an edge that goes beyond monitoring.
CISO Insight
Security that sits on top of your network isn’t enough. The real edge comes when your network is the first line of defense.
If your MSSP also controls the pipes—connectivity, routing, DNS—they’re in the best position to detect and contain threats before they ever reach your endpoints. Ask how they fuse infrastructure intelligence into threat response.
#8. Accenture
Accenture delivers a mature suite of managed security services through its global Cyber Fusion Centers. Their capabilities include Managed Detection and Response, identity security, cloud protection, and incident response across IT, OT, and IoT environments.
Source – Accenture
Accenture’s MSS model is built on advanced threat intelligence, proprietary automation, and strategic partnerships like their joint offering with Verizon Business. For enterprises modernizing rapidly or operating across geographies, Accenture’s strength lies in aligning detection, response, and compliance with sector-specific risk.
Their presence in India enables regionally aligned delivery, supported by global processes and tooling. This makes them a viable choice for enterprises seeking scale with localization.
CISO Insight
The best MSSPs don’t just respond fast; they respond in context.
If your security partner can’t tell the difference between a dev environment misfire and a production breach, they’ll either miss what matters or overreact to what doesn’t. Ask how their team aligns its response to the operational and business impact of the threat.
#9. IBM India
IBM offers a comprehensive suite of Managed Security Services designed to support enterprises in India and across the Asia-Pacific region. Their services encompass threat management, cloud security, identity and access management, endpoint protection, and incident response.
Source – IBM
IBM’s Security Operations Center in Bangalore provides 24/7 monitoring and response capabilities, leveraging its global expertise and local presence. Additionally, the IBM Security Command Center in Bengaluru offers immersive training simulations to prepare organizations for real-world cyber threats.
IBM’s MSS is further strengthened by their proprietary technologies, such as QRadar for security information and event management and Guardium for data protection. Their strategic partnerships, including the AWS Level 1 MSSP Competency, enable them to deliver integrated security solutions tailored to hybrid cloud environments.
CISO Insight
A breach isn’t the time to find out your runbook doesn’t run.
The best MSSPs train for chaos before it happens. Ask how your provider simulates breach scenarios, validates response workflows, and prepares your team to act when everything’s on the line.
#10. PwC India
PwC India provides comprehensive managed security services to enterprises in highly regulated sectors like banking, pharmaceuticals, and manufacturing.
Source – PwC
Their offerings include 24/7 threat detection and response, security orchestration and automation, dark web monitoring, and vulnerability management. Leveraging proprietary platforms like Cyber Risk Insights, PwC delivers contextual risk scoring and unified threat visibility.
Strategic partnerships with AWS and Microsoft enhance their capabilities in cloud security and incident response. For enterprises seeking a managed security service provider that combines global expertise with local delivery, PwC India offers a compelling option.
CISO Insight
Knowing where your risks are is only half the equation. Knowing which ones matter most; that’s what moves the needle.
If your MSSP can’t translate threats into business risk, you’re just patching symptoms. Ask how they connect threat intelligence with what’s actually mission-critical inside your organization.
How These Top Managed Security Service Providers Measure Up: A Strategic Feature Comparison
At the end of the day, choosing an MSSP isn’t about who promises more. It’s about who delivers what matters.
We’ve mapped each provider against the core capabilities that define a world-class MSSP in today’s enterprise environment. From real MDR to compliance readiness, this table shows who meets the mark and where the gaps might lie.
Top 10 Managed Security Service Providers Compared
| Company | 24×7 SOC | Real MDR | SOAR / Automation | PAM | Cloud Security | Regulatory Alignment | Vulnerability Management | Compliance Reporting | Security Analytics |
| Datacipher | Yes – Tier-2/3 SOC coverage | Yes – Real MDR with threat hunting | Yes – Automated detection + triage | Yes – Included in MSS | Yes – Multi-cloud capabilities | Yes – DPDPA, SEBI, ISO 27001 | Yes – Risk-based prioritization | Yes – Pre-built reports | Yes – Cross-layer analytics with SIEM |
| TCS | Yes – Global SOC | Yes – AI-driven threat prevention | Yes – Analytics + orchestration | Yes – IAM/PAM available | Yes – Azure, O365 | Yes – GRC automation | Yes – Enterprise vulnerability mgmt | Yes – GRC dashboards | Yes – Via Cyber Defense Suite |
| Infosys | Yes – Cyber Defense Centers | Yes – Cyber Next threat hunting | Yes – Automated playbooks | Yes – Identity Security Services | Yes – CSPM, SASE | Yes – Compliance-first sectors | Yes – Continuous risk assessments | Yes – CRI platform | Yes – Cyber Next dashboard |
| Wipro | Yes – CyberShield SOC | Yes – MDR + exposure mgmt | Yes – AI-led threat analytics | Yes – IAM/IGA in portfolio | Yes – Broad cloud integrations | Yes – Regulatory tools embedded | Yes – DevSecOps + scanning | Yes – Audit-ready layers | Yes – Central analytics |
| HCLTech | Yes – Fusion Centers | Yes – Threat analytics | Yes – AI/automation-based detection | Yes – IAM + governance | Yes – AWS Level 1 + hybrid | Yes – Compliance controls | Yes – Vulnerability mgmt | Yes – Platform reporting | Yes – Risk scoring tools |
| Tech Mahindra | Yes – Security-as-a-Service | Yes – Threat analytics | Unclear – Automation not detailed | Yes – IAM governance | Yes – AWS Level 1 MSSP | Yes – Sector-aligned compliance | Yes – Exposure services | Unclear – No tooling mentioned | Yes – Risk dashboards |
| Tata Communications | Yes – Real-time threat mgmt | Yes – Threat intelligence | Yes – Includes orchestration | Unclear – PAM not confirmed | Yes – SASE, CASB, Secure Connect | Yes – Audit-aligned | Yes – Risk detection & advisory | Unclear – Reporting not verified | Yes – Unified analytics |
| Accenture | Yes – Global SOC with India delivery | Yes – Fusion Center-based MDR | Yes – Automated, sector-specific | Yes – IAM & resilience | Yes – AWS/Azure integrations | Yes – Compliance-by-design | Yes – Exposure monitoring | Yes – Embedded in MDR | Yes – Business-aligned dashboards |
| IBM India | Yes – Bangalore SOC + global coverage | Yes – QRadar + threat intel | Yes – QRadar SOAR orchestration | Yes – IAM + Guardium | Yes – Multi-cloud capabilities | Yes – Global & local compliance | Yes – Patch & vulnerability mgmt | Yes – Audit trail support | Yes – Unified threat view |
| PwC India | Yes – 24×7 coverage | Yes – Real-time CRI-driven MDR | Yes – Automation via CRI platform | Yes – IAM controls under MSS | Yes – AWS + Microsoft partnerships | Yes – India-specific compliance | Yes – Threat scoring + exposure mgmt | Yes – Reporting built-in | Yes – Executive dashboards via CRI |
Disclaimer: This table is based on publicly available information as of 2025. Where official documentation was not available, we have marked feature status as ‘Unclear.’ For enterprise-grade evaluations, always confirm capabilities via direct provider consultations.
In the rapidly evolving cybersecurity landscape, Indian enterprises require a partner that not only understands the global threat environment but also tailors solutions to local challenges. Datacipher is one of those trusted partners, offering a comprehensive suite of managed security services backed by industry-leading expertise and strategic alliances. Let’s dig deeper.
Why Datacipher is the Top Managed Security Service Provider for Indian Enterprises?
Enterprise security in India has changed. Compliance is no longer a checklist. Threats aren’t just external. And in-house teams, no matter how committed, are under pressure they weren’t built to absorb alone.
That’s where Datacipher fits in. Not as another outsourced vendor, but as a security operations partner built for Indian enterprise realities.
Our MSSP stack isn’t an off-the-shelf service rebranded with local language. It’s architected from the ground up to meet the demands of scale, compliance, and real-time response. Our SOC model offers continuous 24x7x365 threat detection. Moreover, it is staffed by specialists trained in incident response, not generalist engineers juggling after-hours alerts.
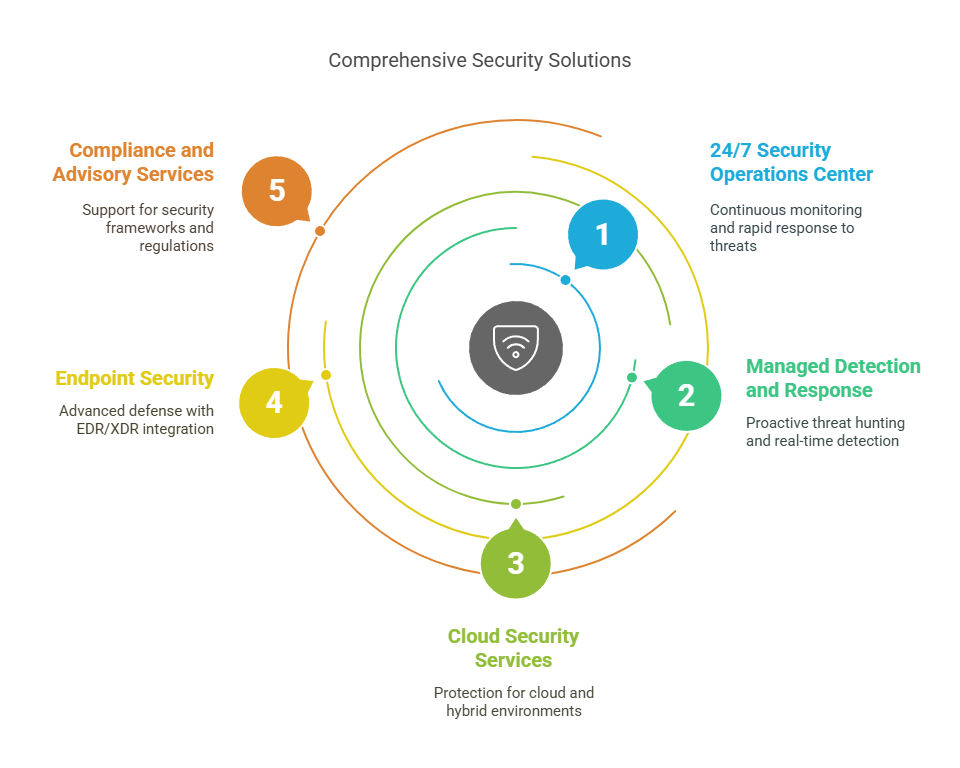
Our Managed Security Services cover every layer of your infrastructure:
- 24/7 Security Operations Center: Continuous monitoring and rapid response to emerging threats, ensuring minimal downtime and swift containment.
- Managed Detection and Response: Proactive threat hunting, behavioral analysis, and real-time detection that goes beyond signature-based alerts.
- Cloud Security Services: Protection across AWS, Azure, hybrid environments, and multicloud setups. We secure Infrastructure as Code (IaC), containers, and serverless architectures with real-time visibility and native cloud integration.
- Endpoint Security: Advanced defense with EDR/XDR integration, ransomware playbooks, and forensic-level telemetry.
- Compliance and Advisory Services: Support for frameworks like ISO 27001, SEBI circulars, and India’s DPDPA backed by reporting, readiness, and remediation.
Here’s what that looks like in the real world: In 2024, a mid-size BFSI firm working on ISO alignment brought us in to replace a legacy MSSP that couldn’t triage alerts fast enough. Within 60 days, we deployed a custom SIEM, embedded role-based access controls, and tuned detection rules. R
Result: 82% reduction in alert noise. First response times dropped under 15 minutes. And the company passed its audit without a single red flag.
What makes us different isn’t just capability, but accountability.
In a world where too many MSSPs outsource the hard parts, we don’t just show up. We dig in and own outcomes. And in 2025, that’s exactly the kind of partner Indian enterprises need.
Want to see what a world-class MSSP looks like in action? Contact us today to get started.
Frequently Asked Questions
#1. How is an MSSP different from an in-house security team with tools like EDR or SIEM?
Most internal teams operate reactively, juggling security alongside IT. A top MSSP like Datacipher delivers 24×7 surveillance, human-led threat hunting, and real-world response at scale. You get not just alerts, but action. That’s the difference between managing tools and operationalizing outcomes.
#2. Do MSSPs like Datacipher offer support for Indian data protection laws like DPDPA?
Yes. Datacipher aligns detection workflows, access controls, and audit readiness with regulations like DPDPA, SEBI, and ISO 27001. Compliance is built into the architecture so you’re always ready, not reacting when a regulator comes knocking.
#3. Can I keep my existing tools like Fortinet or CrowdStrike while working with an MSSP?
You should. The best MSSPs don’t push rip-and-replace. Datacipher integrates directly with what you already use—Sentinel, Fortinet, CrowdStrike, hybrid stacks—and brings in expertise to make those tools deliver the value they were meant to.
#4. How fast should a top-tier MSSP respond to a breach or critical alert?
Speed without precision is noise. A mature MSSP responds to critical threats in minutes, not hours. Datacipher enforces SLA-backed timelines and delivers response with context, not confusion. It’s the difference between isolating a machine and shutting down your business.
#5. What’s the difference between MDR and traditional threat monitoring?
Traditional monitoring waits for alerts. MDR goes looking for trouble. It hunts for behavioral drift, insider threats, and lateral movement before the breach headlines start. If your provider isn’t doing that, you don’t have MDR. You have a log babysitter. If you’re looking for top MDR provider in India, this article will come handy.
#6. Are managed security services scalable for mid-sized enterprises or only large corporations?
Mid-sized businesses face the same threats as the big guys, but with leaner teams. That’s why MSSPs like Datacipher offer modular services. You scale security without overextending resources, and you still get enterprise-grade coverage from day one.